Internet Access
Add, delete and manage the internet Access Rules for your system. You can create granular Security Policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. based on users and groups to control access to Web services, URLs, networks, and services.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. based on users and groups to control access to Web services, URLs, networks, and services.
All the changes you make to the rules are displayed on the Changes pane on the right side of the window.

|
Note - Changes to the Internet Access policies apply only after you click Install Policy. |
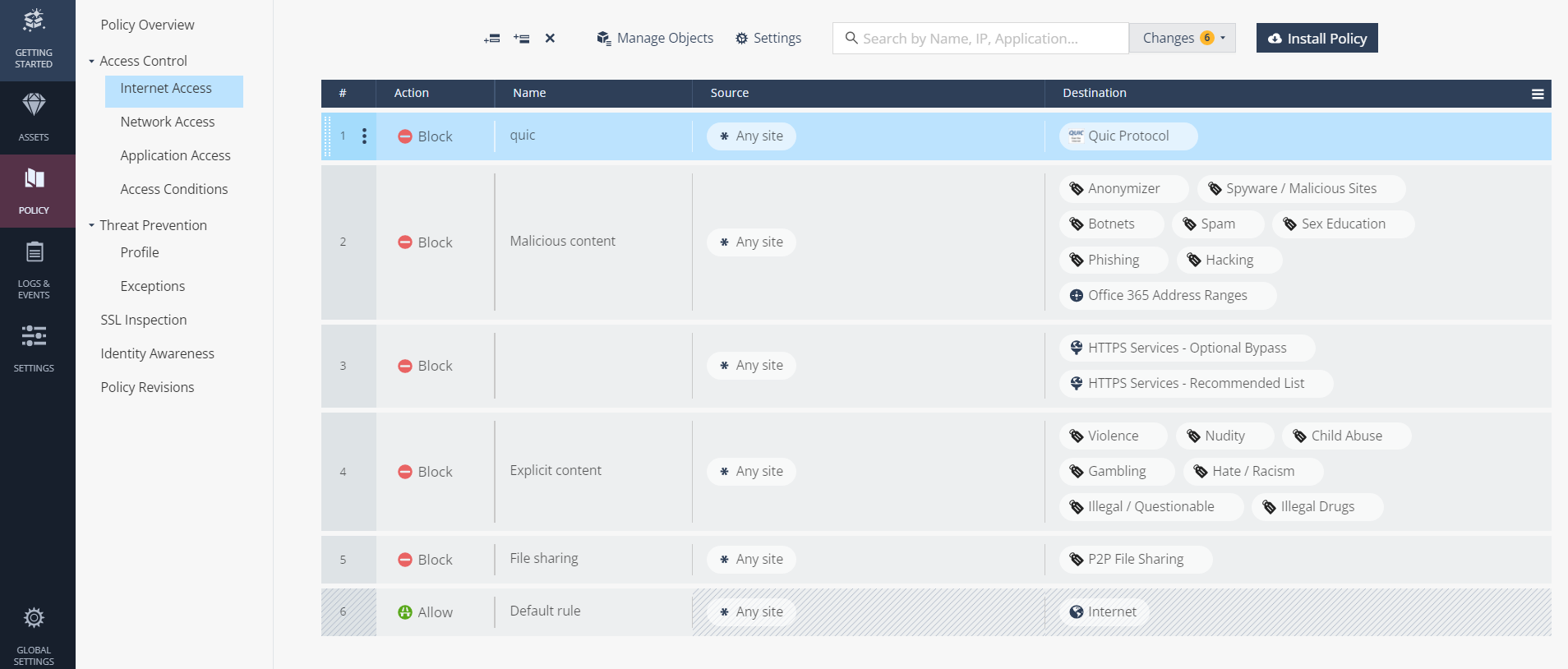
Check Point provides a default initial set of rules:
-
Block Quic Protocol
-
Block Malicious content
-
Block Explicit content
-
Block File sharing
-
The Default Rule (The default value is Allow) - Allows the general internet access when none of the 3 Block Rules are applied. You cannot change its Source or Destination.

|
Best Practice:
|
Check Point provides one Access Control Policy for all of your branch offices. You can use specific objects at a rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. source to apply them to specific sites.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. source to apply them to specific sites.
Define the Policy
To add and configure an Access Control Policy Rule:
-
Navigate to Policy > Access Control > Internet Access.
-
Click one of the Add Rule buttons
 in the row above the table.
in the row above the table.A new rule appears in the table.
-
Configure the required parameters for this rule:
-
Action - Block / Allow status. The default value is Allow.
-
Name
-
Source - User, Groups, or Network Lists, to which the rule applies. The default value is Any Site or User.
-
Destination - Select the destination. The default value is Internet.
-
Categories & Applications
-
URL Lists
-
Services & Networks
-
-
-
Click Install Policy to publish the policy to Check Point cloud
 An administrator approved Harmony Connect cloud location that processes the internet and corporate traffic..
An administrator approved Harmony Connect cloud location that processes the internet and corporate traffic..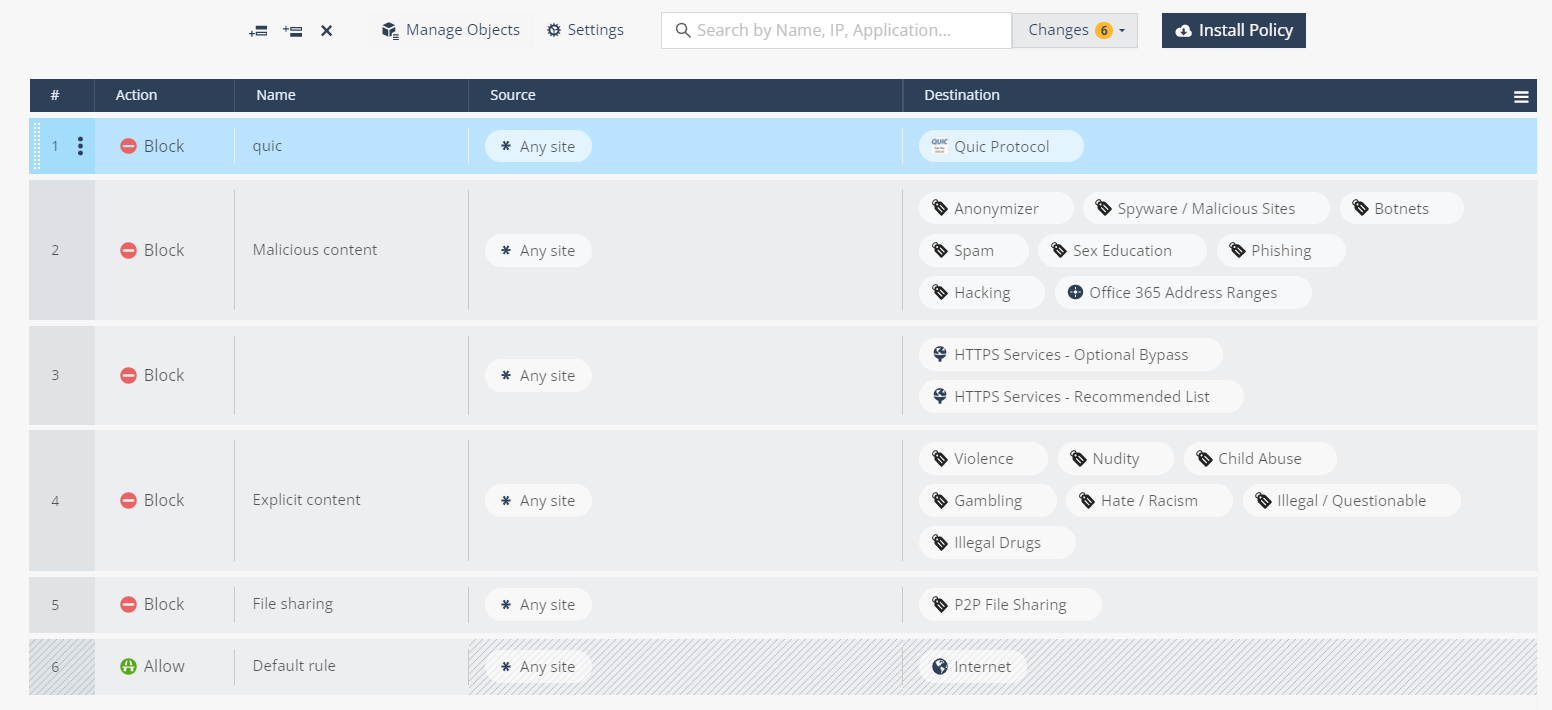
Updatable Objects
An updatable object is a network object which represents an external service. For example:
-
Online services - Office 365, Azure, and AWS
-
GEO locations - The GEO database provides mapping of location data to IP addresses. For each location, there is a network object you can import. You can block or allow access to and from specific locations based on their IP addresses.
External services providers publish lists of IP addresses or Domains or both to allow access to their services. These lists are dynamically updated. Updatable objects derive their contents from these published lists of the providers, which Check Point uploads to the Check Point cloud. The updatable objects are updated automatically each time the provider changes a list. There is no need to install policy for the updates to take effect.
You can add updatable objects:
-
To the destination in the Internet Access policy.
-
As an exception to the Full Inspection. For more information see SSL Inspection
Reviewing Changes
You can review policy or exceptions changes before you install the changes on Check Point cloud.
To review the changes:
-
Click Changes> View Changes. The number on the Changes button indicates the number of changes made that is pending to be installed.
The Changes pane on the right-side of the screen lists the changes made to the Internet Access policy first followed by Exceptions. The changes are listed in the reverse chronological order (most recent first).
-
To undo the changes, click
 .
. -
To revert the last undone change, click
 .
. -
(Optional) Enter comments for the changes in the text field.
Manage Objects
Create, manage, and delete internet objects to which you apply the rules.
Click Manage Objects in the upper section of the screen.
Alternatively, you can click (+) in each cell of Source or Destination to manage objects that are relevant to this Source or Destination.
Safe Search
You can enable safe search for Google, Bing and Yahoo search engines. When users use any of these engines to perform a search, the safe search is turned on by default.
Before you enforce safe search:
-
Make sure that QUIC Protocol is blocked by the first rule.
-
SSL Inspection is set to Full Inspection.
To enforce safe search:
-
Go to Policy > Access Control > Internet Access.
-
Click Settings.
-
Select Enforce Safe Search.
-
Click Save.
After you enable safe search and perform a search, the safe search argument is appended to the end of the URL:
-
Google - https://www.google.com/search?q=trending+news&source=hp&ei=AI&&safe=active
-
Bing - https://www.bing.com/search?q=stock+future&form=Qstock+futur=10-11&qs=&cvid=0&adlt=strict
-
Yahoo - https://search.yahoo.com/search?p=yahoo+maps&fr=yfp-t&fr2=p%3Afpi=UTF-8&fp=1&vm=r
API Reference
With Harmony Connect Internet Access API, you can configure various aspects of application sites, users and groups.
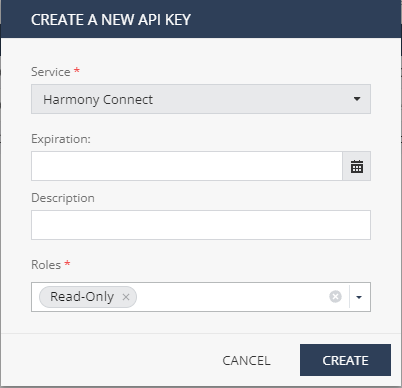
Before you can use the API, you must create an API key in the Infinity Portal. In the Portal's Global Settings, you can generate the API key for read-only access at Harmony Connect Internet Access. For instructions, see the Infinity Portal Administration Guide.
Make sure to set Service to Harmony Connect and Roles to Read-Only.
For full documentation on API, see Check Point Harmony Connect API.