Cyber-Attack View
This page shows the list of all the attacks that Check Point ThreatCloud prevented at your branch offices and remote users, and their detailed description:
-
Hosts infected with Bots
-
Malicious Files
-
Malicious Websites
-
Cyber-Attack Trends
Harmony Connect covers all network protocols.
Double-click a widget, graph or timeline to see sub-views with more granular data.
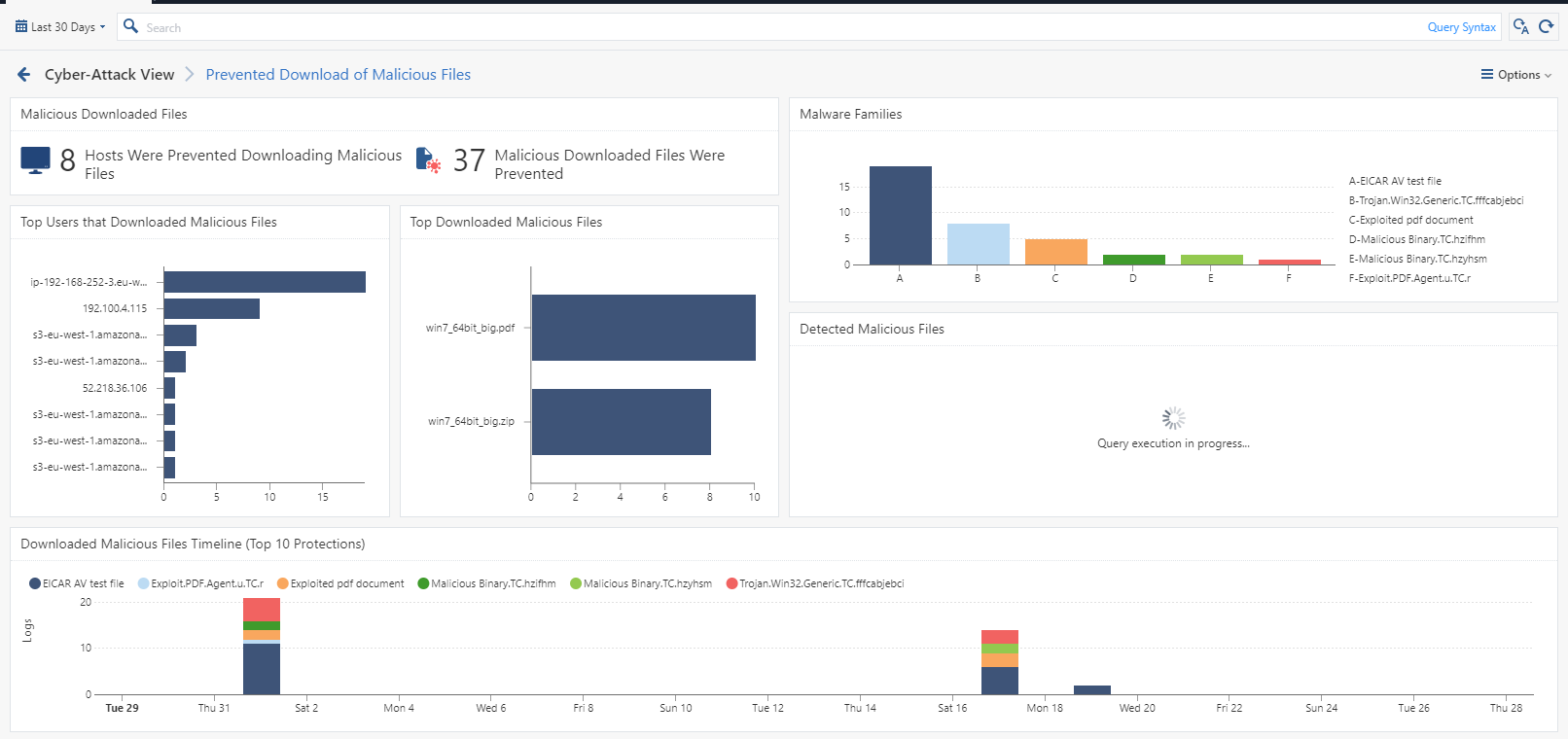
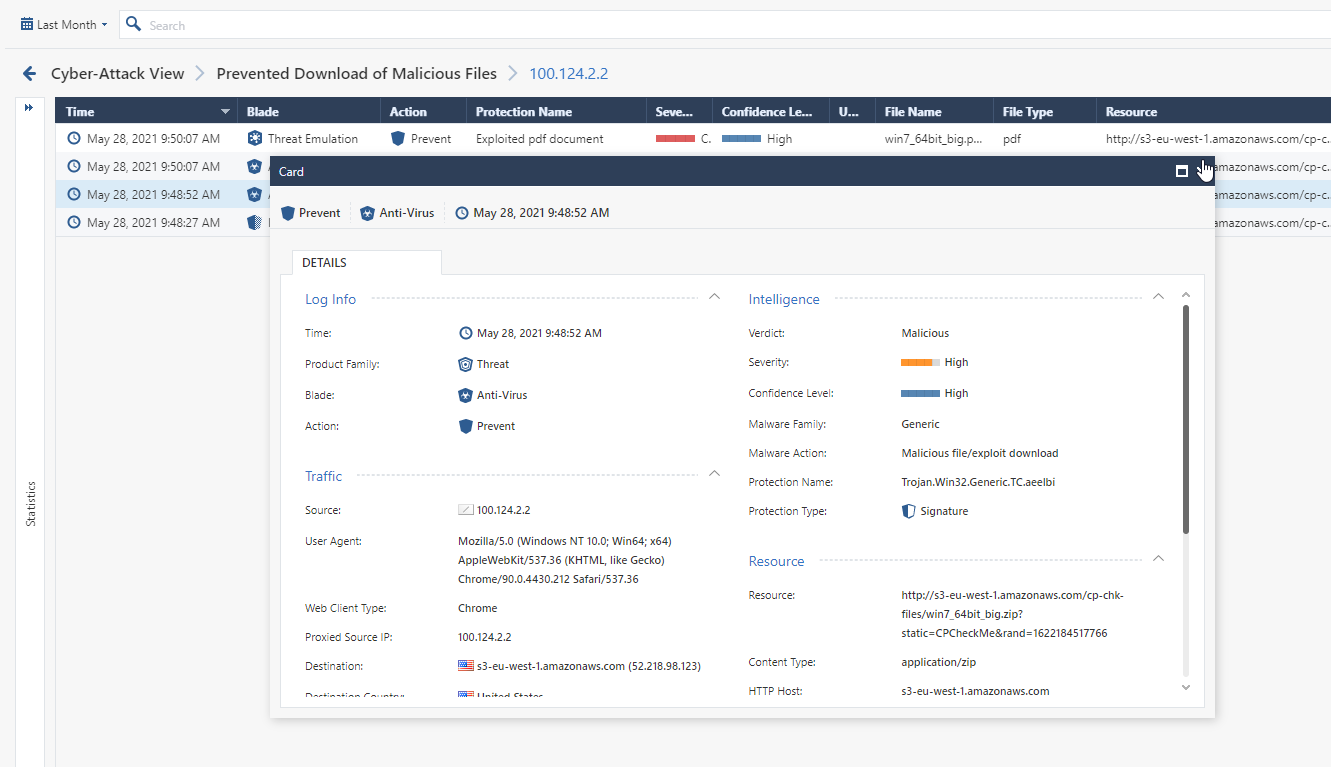
You can see a complete break-down of the connection and the malicious operations prevented on a granular traffic logs.
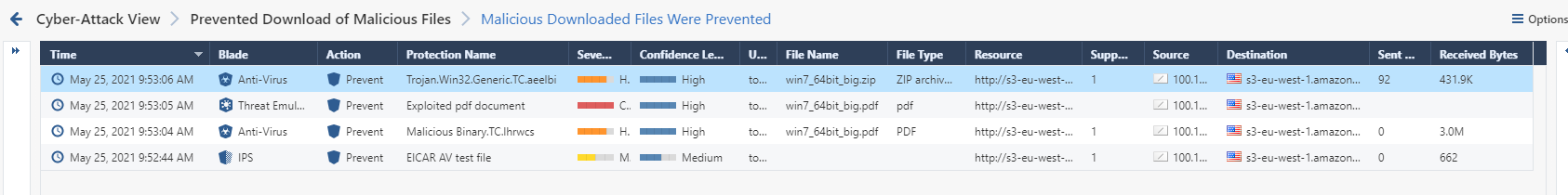
Double-click to see a log card displaying detailed analysis of every event.