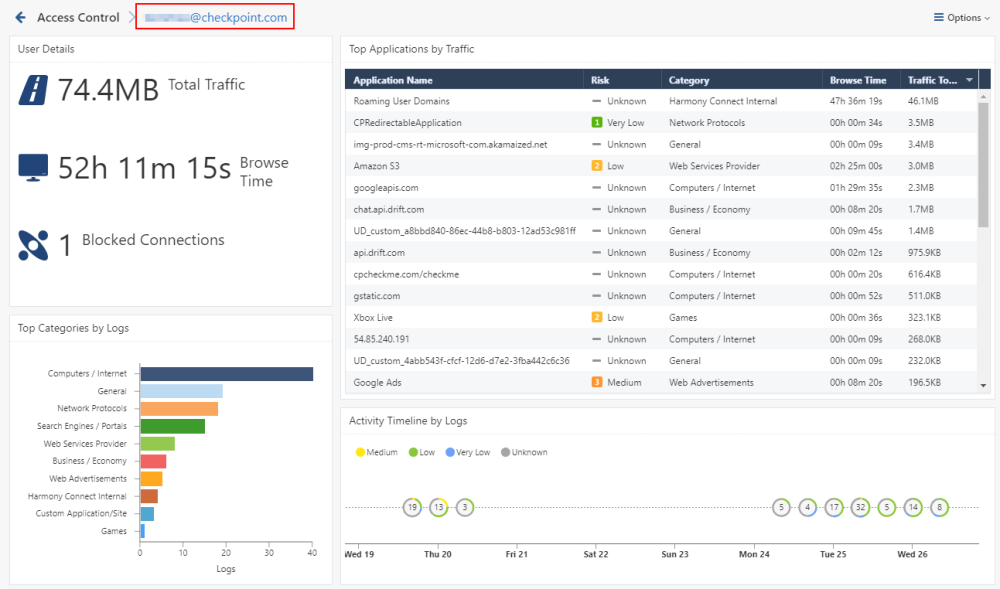
Access Control Logs
This page presents a graphic of the most accessed services and a timeline of the activity and total traffic. You can see the malicious applications that were prevented by Check Point, their total consumed traffic, and their visibility. Use the view to break down activity per user.