Harmony Connect Architecture
Application Access Architecture
System Components
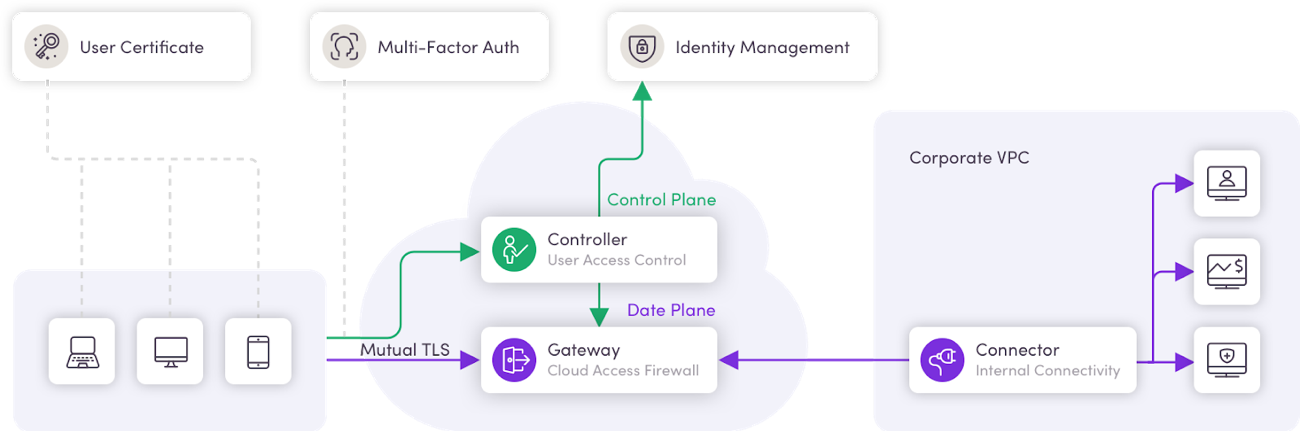
Controller
The controller is the entity authorization end-point. It specifies who has access to what resources through a simple policy framework that factors in contextual data such as user attributes and device state. Policies can be tuned for each team or individual for more granular access management.
Through the controller, the system administrator can:
-
Use the dashboard to create and edit policies with ease
-
Get full visibility on user activity through a detailed activity log
-
Manage device inventory
-
Maintain identities locally or integrate with external IDPs
-
Manage SSH keys
Gateway
A network tunneling gateway. Every user request flows through the gateway for consistent authentication and authorization, as well as providing a unified monitoring and logging point. This component makes sure validated users see only the applications they have permission to see, while the rest of the resources are not only inaccessible, they are completely invisible.
The gateway is in charge of the following attributes:
-
Access Gateway for Web and SSH
-
Contextual firewall
-
End-to-end encryption
-
Network blackening
Connector
The only network leg in the internal site. This component connects to the gateway through a reversed tunnel, and effectively makes the organizational DMZ redundant by being the only access point to the site.
-
Application-level (layer 7) access
-
Cloud and region agnostic
Clients
Application Access is completely clientless.
Login Process
-
Connection: User ↔ Controller
Before any connection is established, the entire network is dark (traffic directed through Gateways in deny-all) with the exception of the controller. The controller receives an access request from the user, which includes contextual data such as device health, host checking, user profile, and credentials.
-
Authorized Services List
After the connection is established, the controller verifies the user credentials with the internal/external identity tools, and retrieves the list of services the user is authorized to access. The list is then passed to the user in the form of a portal, alongside an encrypted authentication token.
-
List of Authorized Services
The controller informs the Gateway of the new access permissions, attached to a specific token. The Gateway then opens the communication to the connector for a specific user, to specific applications only, in a specific period of time.
-
Mutual TLS Tunnel: User ↔ Service
Last, the user turns to the requested service and is automatically directed through its Gateway. The Gateway verifies the identification process took place and opens the right port for encrypted communication between the user and the service.
Internet Access Architecture