Application-Level Access to Corporate Applications
Clientless Application-Level access![]() Clientless access to specific corporate applications, such as web, SSH, RDP, tunnel, and database applications. enables companies to benefit from zero-trust network architecture without the need for VPNs. Built for a mobile cloud
Clientless access to specific corporate applications, such as web, SSH, RDP, tunnel, and database applications. enables companies to benefit from zero-trust network architecture without the need for VPNs. Built for a mobile cloud![]() An administrator approved Harmony Connect cloud location that processes the internet and corporate traffic.-first world, Application-Level access provides trusted access to corporate applications, with total visibility on all network activity.
An administrator approved Harmony Connect cloud location that processes the internet and corporate traffic.-first world, Application-Level access provides trusted access to corporate applications, with total visibility on all network activity.
Zero-Trust Mindset
With no fixed perimeter to secure, companies can no longer rely on binary security models. The zero-trust security model embraces today's reality that users need frictionless access from any device and any location, and treats every access attempt as suspect until both the user and device are authenticated and authorized.
The zero-trust security model presents a new approach:
-
Consider internal threats - Network locality is no longer sufficient to determine trust in a network. External and internal threats exist on your network at all times.
-
Authenticate first, connect second - Every device and user that attempts to access an application must first be authenticated and authorized. Authentication is based on contextual user attributes such as credentials, device ID and state, time, location etc.
-
Granular, limited access - Access to applications does not require access to the entire network. Users should only be able to connect to applications on a need-to-know basis and for a limited period of time.
-
Network blackening - External users, as well as internal users, should not be aware of unauthorized applications. Unauthorized resources should be inaccessible and completely invisible.
-
Network activity monitoring - IT teams must be able to easily monitor and manage of all network activity and block suspicious commands in real time.
Reduced Network Attack Surface
With Application-Level access, you can mitigate known attacks to reduce the network risk:
-
Lateral movement: When unauthorized resources are invisible, attackers cannot crawl through the network.
-
Credential theft: Application-Level access verifies users by multiple authentication factors such as device ID, location, time of day and user behavior before allowing network access.
-
Man-in-the-middle: All traffic is encrypted end-to-end.
-
DDoS: Application-Level access allows you to effectively cancel the organizational DMZ and make all the resources internal and protected.
Zero Trust architecture uses the principle of never trust, always verify to address the threat of lateral movement within the network. It leverages micro-segmentation and granular perimeters enforcement, based on user type, data and location. Zero Trust mode delivers access on a need-to-know basis - users can only access pre-approved network resources. Other resources are not only inaccessible, but completely invisible.
Improved User Experience
The agentless cloud-based solution delivers a seamless user experience across different device types and network conditions.
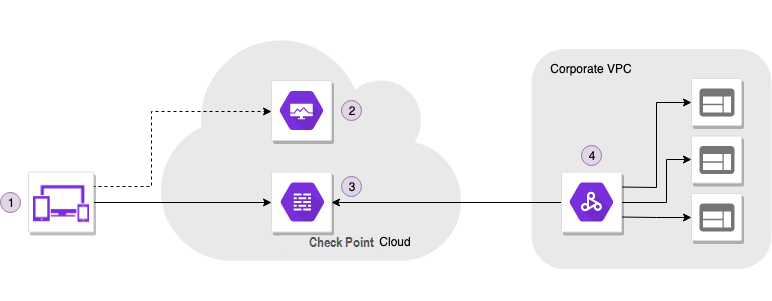
How It Works
Application-Level access zero-trust architecture moves access control mechanisms from the network perimeter to the application level, to better enforce business-driven security policies![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. and access controls.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. and access controls.
-
Users & Devices
Application-Level access provides clientless, secure application access with SaaS-like user experience. You do not need to install a client or agent is required. Implementation occurs in minutes.
-
Control Plane
Indicates the geographical region (location) that hosts your Infinity Portal instance. You can use Control Plane to specify user and resource access through a simple policy framework that factors in user attributes and device state.
You can assign policies to each team or individual for more granular access management.
Use the dashboard to create and edit policies with ease.
-
Centralized access control from Harmony Connect at the Infinity Portal
-
Policy management
-
Device management
-
Detailed activity logs and recorded sessions (Web, SSH, RDP)
-
Native integration with your identity provider
-
Built-in SSH key management
-
-
Data Plane
Every user request flows through a contextual firewall for consistent authentication and authorization, and provides a unified monitoring and logging point.
-
Access Gateway for Web and SSH
-
Contextual firewall
-
Secure tunnel
-
Layer 7 visibility
When you set up your site, you can connect each Control Plane to multiple Data Planes.
-
-
Corporate Network
Validated users see only the applications they are pre-authorized to see.
For unauthorized users (or attackers), your network is not only inaccessible, it is invisible.
-
Application-level access only
-
Network blackening
-
Auto-discovery for containerized applications
-
Cloud-agnostic
-
API Reference
With Harmony Connect Application-Level access API, you can configure various aspects of application sites, users and groups.
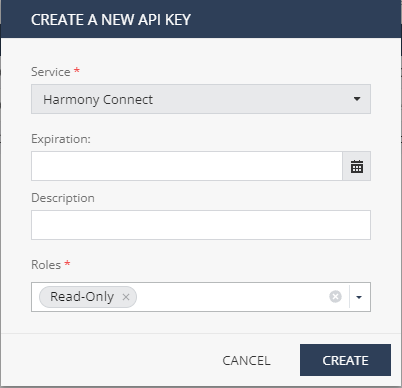
Before you can use the API, you must create an API key in the Infinity Portal. In the Portal's Global Settings, you can generate the API key for read-only access at Harmony Connect Application-Level. For instructions, see the Infinity Portal Administration Guide.
Make sure to set Service to Harmony Connect and Roles to Read-Only.
For full documentation on API, see the Harmony Connect Application-Level Access API guide.
