Users and Devices
The Uses and Devices page shows all connected users.
Users and Devices View
With the Users and Devices view, in the upper part of this page, you can manage existing users and invite new users.
Available options for user management:
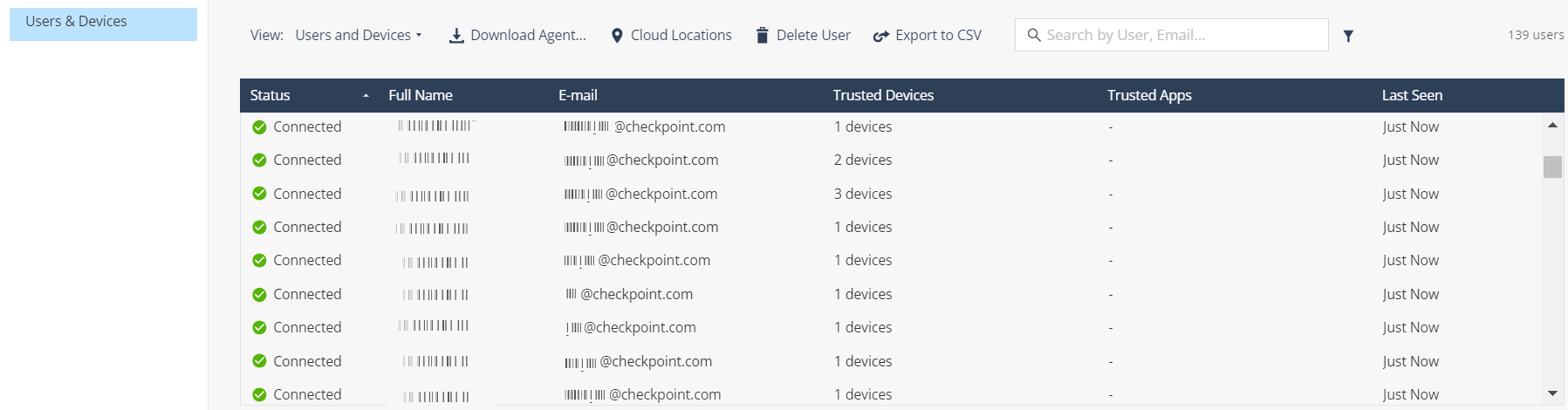
The table shows the current status of your users:
| Parameter | Description |
|---|---|
|
Status |
User status in Harmony Connect. Possible values:
In addition to the status, a warning icon may appear for some of the users. Check Point recommends to review the warning and the suggestions for a resolution. An example of a warning: Could not invite the user to secure Application Access because the user email address already associates with another Infinity Portal account. |
|
Full Name |
User full name. |
|
|
User email address to which the invitation is sent. |
|
Trusted Devices |
For users with secure Internet Access: |
|
Trusted Apps |
For users with secure Application-Level access |
|
Last Seen |
Date and time of the last connection session. |
In the lower part of the page, you can manage trusted devices and policies. For more information, see Managing Devices.
All Trusted Devices View
This view shows all devices that belong to all users. For more information, see All Trusted Devices View.