Legacy Exclusions
You can exclude specific objects from inspection by the protections:
Adding Exclusions to a Specific Rule
To add exclusions to a specific rule:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Select the rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. for which you want to create the exclusion
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. for which you want to create the exclusion -
In the Capabilities & Exclusions pane, click Exclusions Center.
-
Expand an exclusion category. For example, Anti-Bot -> URL Filtering Exclusions.
Note - Global Exclusions is read-only. To add Global Exclusions, see Adding Global Exclusions.
-
Expand Rule Exclusions.
-
Select the exclusions you want to add to the rule.
-
Click OK.
-
In the bottom right corner of the policy configuration pane, click Save.
-
From the top, click Install Policy.
Adding Global Exclusions
To add global exclusions that apply to all the rules:
-
Go to Policy > Threat Prevention > Global Exclusions.
-
Expand an exclusion category. For example, Anti-Bot -> URL Filtering Exclusions.
-
Select the exclusions you want to add to the rule.
-
Click Save.
-
From the top, click Install Policy.
Adding Exclusions from Logs
To add exclusions from the Logs menu:
-
Go to Logs menu.
-
Right-click a log to add and configure an exclusion to your endpoint device. This redirects you to the appropriate rule, section, and capability.
-
Select one of these options to apply the exclusions:
-
Effective option: For a specific device or a user rule.
-
All options: For a specific rule.
-
Adding a New Exclusion to an Exclusion Category
To add an exclusion to an exclusions category:
-
Do one of these:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Go to Policy > Threat Prevention > Global Exclusions.
The Edit Exclusions Center window appears.
-
-
Click
 .
.The New Exclusion window appears.
-
Specify these details:
-
Exclusion
-
Method
-
Value
-
(Optional) Comment
-
To add the exclusion to all the rules, select the Add to all rules checkbox. This step does not apply to Global Exclusions.
Note - If the current rule contains this exception, then the system adds a duplicate exclusion.
-
-
Click OK.
-
In the bottom right corner of the policy configuration pane, click Save.
-
From the top, click Install Policy.
Editing an Exclusion
To edit an exclusion:
-
Do one of these:
-
Go to Policy > Threat Prevention > Policy Capabilities.
-
Go to Policy > Threat Prevention > Global Exclusions.
The Edit Exclusions Center window opens.
-
-
Expand an exclusion category. For example, Anti-Bot -> URL Filtering Exclusions.
-
If you are editing a local exclusion, expand Local Exclusions. This step does not apply to Global Exclusions.
-
Select the exclusion you want to edit.
-
Click
.
The Edit Exclusion window appears.
-
Specify these details:
-
Exclusion
-
Method
-
Value
-
(Optional) Comment
-
To apply the changes to all the rules that contain this exclusion, select the Update all rules checkbox. This step does not apply to Global Exclusions.
-
To add the exclusion to all the rules that does not contain this exclusion, select the Add to all rules checkbox. This step does not apply to Global Exclusions.
-
-
Click OK.
-
In the bottom right corner of the policy configuration pane, click Save.
-
From the top, click Install Policy.
Below is the list of supported exclusions.
You can exclude specific domains from a rule. Click + to add the required domain you want to exclude from the rule.
Syntax
-
* indicates a string or a character. For example, A* can be ADomain or AB or AAAA.
-
? indicates a character. For example, A? can be AA or AB or Ab.
For example:
|
If you enter |
It excludes these |
It does not exclude these |
|---|---|---|
| www.domain.com |
|
|
| domain.com |
|
- |
| sub.domain.com |
|
https://sub2.domain.com |
|
*.domain.com |
Sub-domain of domain.com such as:
|
|
You can exclude:
-
Domains
-
SHA1 hashes from Threat Emulation
 Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Threat Extraction
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Threat Extraction Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX.
Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX.
Domain exclusions
-
To exclude an IP, in the Element field, enter IP address followed by subnet mask in the format <X.X.X.X>/ <subnet mask >. For example, to exclude a computer with IP address 192.168.100.30, enter 192.168.100.30/24.
-
Domain exclusions must be added without http, https or any other special characters except asterisk (*).
Domain exclusions can be added with or without www.
-
Sub-domain exclusions are supported.
Exclusion of a domain will exclude all its subdomains as well.
For example:
|
If you enter |
It excludes these |
It does not exclude these |
|---|---|---|
| www.domain.com |
|
|
| domain.com |
|
- |
| sub.domain.com |
|
https://sub2.domain.com |
|
*.domain.com |
Sub-domain of domain.com such as:
|
|
SHA1 exclusions -
-
It is not supported with Internet Explorer.
-
Macro exclusion - To exclude the office files which includes a macro, set exclusions for the SHA1 hash of the macro.
For example, if an exclusion is set to SHA1 hash of the macro, all the files which includes this macro are excluded.

Notes -
-
This is supported with Endpoint Security Client
 Application installed on end-user computers to monitor security status and enforce security policies. version E88.00 or higher.
Application installed on end-user computers to monitor security status and enforce security policies. version E88.00 or higher. -
To view the hash of a macro, see the Description in the Forensic Details section in the Card of the event. For more information see, Adding Exclusions from Logs.
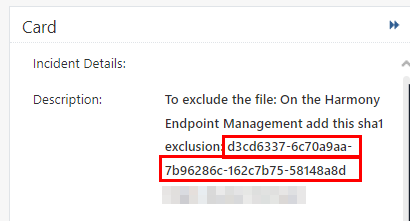
-
-
Excludes downloaded files from File Protection.
-
Excludes local HTML files from Zero Phishing.
