Smart-1 Cloud Advanced Configuration
Use these commands on the Security Gateway to see the communication status and clear the communication between the Security Gateway and the Smart-1 Cloud service.
How to Connect a Security Gateway Behind a NAT/Proxy or Third-Party Security Gateway
In Smart-1 Cloud, the Security Gateway opens a HTTPS tunnel to the service. Smart-1 Cloud can open A Secure Internal Communication (SIC) to the Security Gateway when the tunnel is finished and operational.
You must allow outbound HTTPS traffic to FQDN listed below to allow the communication between the Security Gateway and the service:
-
To your domain at Smart-1 Cloud:
<Service-Identifier>.maas.checkpoint.com -
For Smart-1 Cloud deployments in Europe:
cloudinfra-gw.portal.checkpoint.com -
For Smart-1 Cloud deployments in the United States:
cloudinfra-gw-us.portal.checkpoint.com -
For Smart-1 Cloud deployments in the APAC:
https://cloudinfra-gw.ap.portal.checkpoint.com
How to Connect a Quantum Spark Appliance with a Dynamic IP (DAIP)
Step 1: Create a Gateway object
-
From the left navigation panel, click Gateways & Servers.
-
Click the New icon
 or a
or a  button and select Gateway....
button and select Gateway....The Check Point Gateway properties window opens.
-
Fill in the required fields for the Check Point Security Gateway:
-
Enter name - The name for the Security Gateway.
-
IP Address - Select the Dynamic Address checkbox.
-
-
Click Yes in the Enable Dynamic Address? window.
Step 2: Prepare the connection
-
In the Device section, click Connect.
The Connect Device window opens.
-
In the Security Gateway section, select Quantum Spark.
-
In the Connection preference section, select Prepare the object now, connect the Security Gateway later.
-
Click Next.
Step 3: Configure Authentication
-
Set up the one-time password (OTP) for secure communication between the Security Gateway and Smart-1 Cloud.
-
Choose how to identify the device:
-
MAC Address
-
Gateway Name
-
First to Connect
-
-
Click Next and securely save the generated token. This will be used on the Quantum Spark device later.
-
Click Close and then OK.
-
Publish the changes and push the Policy.
Step 4: Connect the Quantum Spark Appliance
-
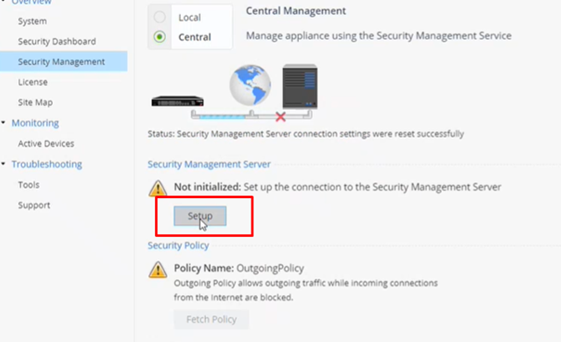
Connect to the Quantum Spark WebUI, navigate to the Security Management tab, and click Setup.
-
Select the Use Security Management service checkbox and click Next.
-
Click Use the Infinity Portal to generate a new authentication token and paste the token. Click Connect.
-
Wait for the status to change to Connected successfully to the Security Management Server, then click Next.
-
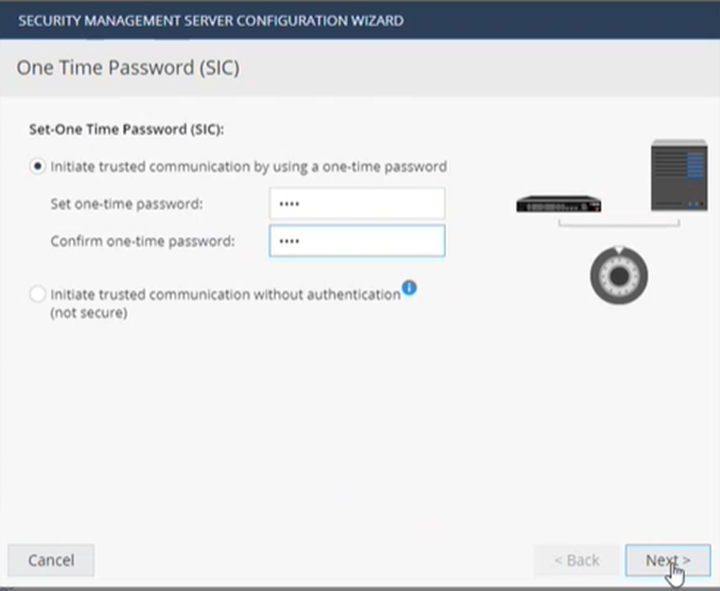
Set the one-time password and click Next:

Important - Do not select the "Initiate trusted communication without authentication" option. Authentication with the SIC password is required.
-
Check Connect to the Security Management Server now and click Connect.

Note - The following message will appear:
"Security Policy Installation: Trust is established with the Security Management Server. However, unable to fetch the Security Policy from the Management Server"
After the trust is established, you can continue with the process.
-
Click Finish.
Step 5: Finalize configuration in Smart-1 Cloud
-
Connect to the Smart-1 Cloud WebUI.
-
In Gateways & Servers, double-click the Quantum Spark device that was configured earlier. The device properties window opens.
-
Under Network Management, select General.
-
In the Interfaces menu, select Get Interfaces with Topology.
-
Once it is done, publish the changes.
How to Configure the Query Settings in SmartConsole
-
From the left navigation panel, click Logs & Monitor > Logs.
-
To the right of the query field, click Options > Tools > Query Settings.
-
In the Query Settings window, configure the applicable settings.
-
Click OK.
For more information, see the Logging and Monitoring Administration Guide for your version.
How to Connect a Local Active Directory to Smart-1 Cloud
Smart-1 Cloud customers that want to use their local AD server in their Identity Awareness configuration must configure the gateway as proxy for the cloud management.
To connect your local AD server to Smart-1 Cloud:
-
In the Streamed SmartConsole > Objects window on the right, click New > Host and create a host for your Domain Controller.
-
Create LDAP Account Unit: Click New > More > User/Identity > LDAP Account Unit.
-
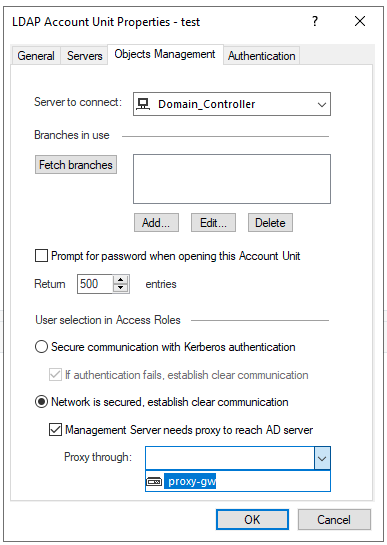
On the LDAP Account Unit Servers tab, add an LDAP server.
-
On the Object Management tab > Server to connect field > Select the host object you created for the Domain Controller.
-
Manually add the branch(es).
Fetching branches is not supported; it is necessary to add them manually.
The branch name is the suffix of the Login DN that begins with
DC=.Example:
If the Login DN is:
CN=John.Smith,CN=Users,DC=mycompany,DC=comthen the branch name is:
DC=mycompany,DC=com -
Select Management Server needs proxy to reach AD server.
-
In the Proxy through field, select the Security Gateway / Security Cluster that has a route to your AD server.

Important - Notes about the Identity Awareness Gateway as Active Directory Proxy feature:
-
This feature operates only with Microsoft Active Directory.
-
This feature supports only the user picker in the Access Role object.
Other settings, such as Identity Awareness Configuration wizard, Client certificate, Legacy user picker, Fetch branches, Fetch fingerprint, and LDAP tree are not supported.
-
This feature operates only with Security Gateway R80.20 and higher running Gaia OS.
-
This feature operates only with Quantum Spark appliances R80.20.00 and higher running OS (see the Quantum Spark Appliances Centrally Managed Administration Guide for your version).
-
This feature does not support DAIP gateways or externally managed gateways.
-
Available communication types:
-
Clear - Communication between the Security Management Server and the Security Gateway is encrypted by SIC. But the communication from the Security Gateway to the Active Directory server is not encrypted.
-
SSL - Active Directory domain controller needs to allow SSL.
-
-
Required Active Directory permissions for the account used to configure the Account Unit:
-
For user picker functionality, the account must have permission to do LDAP queries.
-
For Security Gateway functionality - depends on the identity sources that are used on the Security Gateway.
-
To get identities with the Active Directory Query, without use of domain admin credentials, refer to sk93938.
-

Important -Identity Logging is not supported in Smart-1 Cloud.
-
How to Configure Access to Security Gateway Gaia Portal
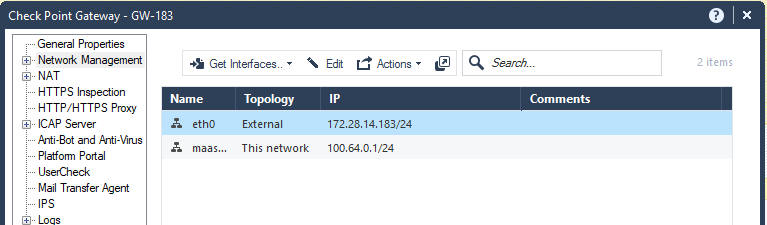
The IP address in the Security Gateway object represents the interface between the Security Gateway and the service.
This IP address is internal (private) and you cannot use it on the Internet.
|
|
Note - If a Security Gateway object is created with a static IP address, access to the Security Gateway Gaia Portal is allowed without any change. |
To allow access to the Security Gateway Gaia Portal:
-
In SmartConsole, navigate to Gateways & Servers.
-
Open the Security Gateway object.
-
From the left tree, click Platform Portal.
-
Change the primary URL to the Security Gateway IP address used for Gaia login.
-
Publish the SmartConsole session.
-
Install the Access Control policy.
Example:
The displayed Gateway IP address is the MaaS tunnel IP address.
Change the Platform Portal IP address to the Security Gateway IP address used for the Gaia login.
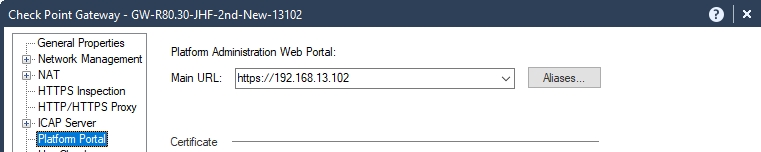
How to Configure Access from the Security Gateway External IP Address to the Internal Asset with Static NAT
Smart-1 Cloud uses the Security Gateway object's primary IP address for tunnel communication between the Security Gateway and the cloud service. It is a virtual interface.
|
|
Note - When configuring NAT rules, standard settings are available if the Security Gateway object is created with a static IP address. |
Consequently, this rule's destination IP address is a virtual tunnel IP address, not the Security Gateway's physical external interface.
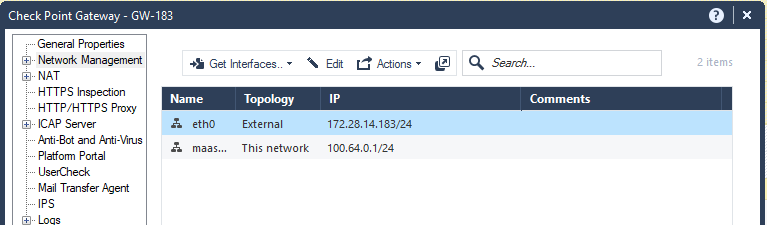
This screenshot shows the IP address in the tooltip:
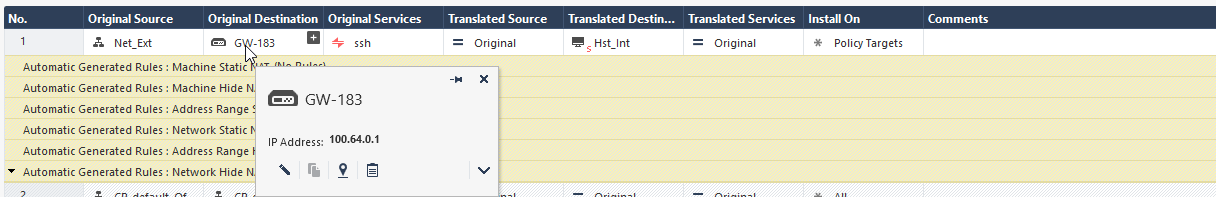
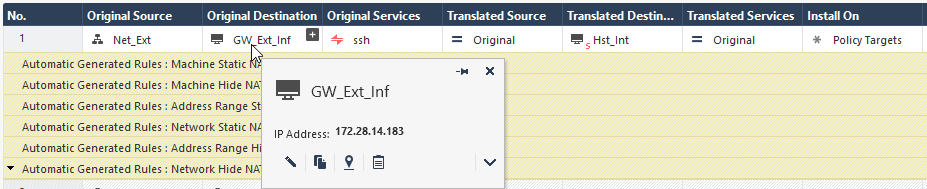
To configure access from the Security Gateway's External IP address to the Internal Asset with NAT Policy, a static rule in Smart-1 Cloud, you must create a dummy object with the physical IP address of the Security Gateway. You then use it in the NAT rule.
In this screenshot, the dummy Host object ("GW_Ext_int") that contains the Security Gateway's physical IP address, replaces the Security Gateway object ("GW-183").
How to Configure IP Address Selection by Remote VPN Peer
There are some methods that can determine how remote peers resolve the IP address of the local Security Gateway.
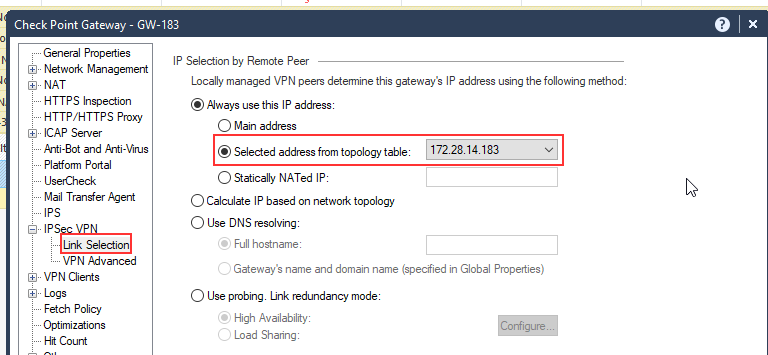
Configure these settings in Security Gateway Properties > IPsec VPN > Link Selection.
|
|
Note - If you create the Security Gateway object with a static IP address and not with the tunnel IP address, link selection is not required. You can use the standard settings for VPN configuration on the Security Gateway. We recommend configuring in Smart-1 Cloud a static IP address in the Security Gateway object for VPN configuration. |
Smart-1 Cloud uses the Security Gateway object's primary IP address for tunnel communication between the Security Gateway and our cloud service. It is a virtual interface.
Consequently, you cannot use the Main address option.
As an alternative, use one of these options to select an address from the topology table:
Option 1:
Option: 2
Smart-1 Cloud Configuration for Site-to-Site VPN
When you configure a Site-to-Site VPN between two gateways, the VPN status can show as "down".
To resolve this issue, it is necessary to configure the topology of the maas_tunnel interface as "Internet (External)."
|
|
Note - You require this configuration only when you have Site-to-Site VPN between two Security Gateways (not clusters). |
To configure a Site-to-Site VPN in SmartConsole:
-
From the left navigation panel, click Gateways & Servers.
-
Open the Security Gateway object.
-
Navigate to Network Management.
-
Select the maas_tunnel interface > click Edit.
-
On the general page, click Modify.
-
Select Override > Internet (External).
-
Click OK.
-
Run steps 2-7 again for all Security Gateways in the Site-to-Site VPN.
-
Install the Access Control policy on all applicable Security Gateways.
Example:
Configuring MDPS to activate a MaaS Tunnel Interface
You can configure Management Data Plane Separation (MDPS) to activate the MaaS_Tunnel interface in the Management Plane context.
-
Connect to the relevant Security Gateway using SSH or console access.
-
Add required MDPS tasks. For this, run the commands below to add the tunnel processes to MDPS:
add mdps task process vtunneladd mdps task process wstunnel -
Reboot the Security Gateway to apply the changes.