Troubleshooting
|
Issue |
Solution |
||
|---|---|---|---|
|
How to enable debugging on each Cluster Member |
From the Cluster
Debug output is written to: $FWDIR/log/aws_had.elg To disable debugging, you MUST run the following command on each Cluster Member:
|
||
|
What permissions are required for the CloudGuard Security Cluster Members IAM role? |
Copy
Example of a JSON script
IAM roles, not properly configured, will prevent the Cluster Members from communicating with AWS |
||
|
Experiencing issues with Cluster |
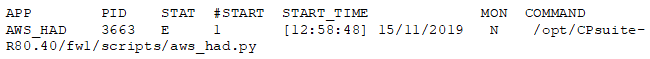
Verify that the script in charge of communicating with AWS is running on each Cluster Member. On the Cluster Member (either one), run in the Expert mode:
The output should have a line like this:
|
||
|
Testing the environment |
For testing the Cluster environment, run in the Expert mode:
This will run tests that verifies:
|
||
|
Routing tables (RTB) do not fail over with AWS cluster members when more than one RTB is configured |
Refer to sk121598. |
||
|
During failover, the AWS route tables do not change their route from the failed member to standby active member |
|