Check Point CloudGuard Network for AWS
Check Point CloudGuard Network for AWS![]() Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. easily extends comprehensive Threat Prevention security to the AWS cloud and protects assets in the cloud from attacks, and at the same time enables secure connectivity.
Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. easily extends comprehensive Threat Prevention security to the AWS cloud and protects assets in the cloud from attacks, and at the same time enables secure connectivity.
Use CloudGuard Network to enforce consistent Security Policies![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. across your entire organization. It protects data between the corporate network and the Amazon VPC. CloudGuard Network inspects data that enters and leaves the private subnet in the Amazon VPC to prevent attacks and mitigate data loss or leakage. CloudGuard Network protects services in the public cloud from the most sophisticated threats, unapproved access, and prevents application layer Denial of Service (DoS) attacks.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. across your entire organization. It protects data between the corporate network and the Amazon VPC. CloudGuard Network inspects data that enters and leaves the private subnet in the Amazon VPC to prevent attacks and mitigate data loss or leakage. CloudGuard Network protects services in the public cloud from the most sophisticated threats, unapproved access, and prevents application layer Denial of Service (DoS) attacks.
|
|
Note - For the list of supported versions, refer to the Support Life Cycle Policy. |
Costs and Licenses
You are responsible for the cost of the AWS services that you use, when you deploy the solution described in this guide.
The AWS CloudFormation template for the Security VPC includes parameters that you can configure. Some of these settings, such as instance type have an effect on the cost of deployment. For estimated costs, see the AWS pricing calculator.
This Transit VPC - Transit Gateway solution uses Amazon Machine Images (AMIs) from the AWS Marketplace. You must subscribe to Check Point CloudGuard in the AWS Marketplace before you start the deployment.
Check Point CloudGuard Security Gateways, Check Point CloudGuard Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server., and AWS CloudFormation templates described in this guide must have a license. There are two licensing options:
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server., and AWS CloudFormation templates described in this guide must have a license. There are two licensing options:
-
Pay As You Go (PAYG)
-
Bring Your Own License (BYOL)
To buy BYOL licenses, contact Check Point Sales.
Prerequisites
Before you use this solution, make sure you read the AWS terms and services.
-
EC2 (Elastic Compute Cloud)
-
VPC (Virtual Private Cloud)
-
IAM (Identity and Access Management)
As part of this guide, it is necessary to create an IAM instance profile and later pass the role to the Check Point instances. To do this, you must have an AWS user account with IAM privileges.
If you are new to AWS, see Getting Started with AWS.
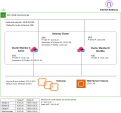
Architecture
The diagram shows Security Cluster![]() Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. architecture for Check Point CloudGuard AWS.
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. architecture for Check Point CloudGuard AWS.
A Check Point cluster in a non-AWS environment uses multicast or broadcast to do state synchronization and health checks across Cluster Members.
As multicast and broadcast are not supported in VPC, the Check Point Cluster Members in AWS use unicast to communicate with each other.
In addition, in a regular ClusterXL in High Availability mode, Cluster Members use Gratuitous ARP Requests to announce the MAC Address of the Active member that is associated with the Virtual IP Address (during normal operations and when cluster failover occurs).
In contrast, in AWS this is implemented by making API calls to AWS.
When a cluster failover occurs, the Standby Cluster Member![]() Security Gateway that is part of a cluster. is promoted to Active and takes ownership of the cluster resources. As part of this process this member:
Security Gateway that is part of a cluster. is promoted to Active and takes ownership of the cluster resources. As part of this process this member:
-
Moves all secondary private IP addresses from the failed Cluster Member to itself.
-
Changes the default route in all routing tables associated with internal networks to point to it's internal interface.
To automatically make API calls to AWS, it is necessary to provide the Cluster Members with credentials. This is done with a standard AWS mechanism called IAM Roles.
For more information about IAM roles, see: IAM roles for Amazon EC2.
Security Policy
A Security Policy package is a collection of different types of policies that are enforced after you install the policy on the Security Gateways.
A policy package can have one or more of these policy types:
-
Access Control
-
Desktop Security
-
Threat Prevention
The Standard policy package is the default Security Policy defined in a newly deployed Security Management Server![]() Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server.. Each policy package has a default cleanup rule
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server.. Each policy package has a default cleanup rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that drops all traffic.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. that drops all traffic.