Overview of Cloud Management Extension (CME)
CME is a tool that runs on Check Point's Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. and Multi-Domain Security Management Server
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. and Multi-Domain Security Management Server![]() Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server.. CME allows cloud-native integration between Check Point CloudGuard Network solutions and Cloud platforms.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server.. CME allows cloud-native integration between Check Point CloudGuard Network solutions and Cloud platforms.
As a Service, it continuously monitors CloudGuard Network solutions deployed in different cloud vendors and synchronizes them with the Security Management Server.
Supported Solutions and Features
-
CloudGuard Network for Azure VMSS
-
CloudGuard Network for Azure Gateway Load Balancer
-
CloudGuard Network for Azure Virtual WAN
-
CloudGuard Network for AWS
 Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. Auto Scaling Group
Amazon® Web Services. Public cloud platform that offers global compute, storage, database, application and other cloud services. Auto Scaling Group -
CloudGuard Network for AWS Transit VPC
-
CloudGuard Network for AWS Transit Gateway
-
CloudGuard Network for AWS Gateway Load Balancer
-
CloudGuard Network for GCP
 See 'Google Cloud Platform'. Managed Instance Group
See 'Google Cloud Platform'. Managed Instance Group -
Automatic Hotfix
 Software package installed on top of the current software version to fix a wrong or undesired behavior, and to add a new behavior. Deployment for autoscaling solutions
Software package installed on top of the current software version to fix a wrong or undesired behavior, and to add a new behavior. Deployment for autoscaling solutions -
CloudGuard Network for NSX-T. For more information, see the CloudGuard Network for NSX-T Security Gateway Deployment Guide

|
Note - For the list of supported versions, refer to the Support Life Cycle Policy. |
CME configuration file
The CME configuration file has three fields which are detailed in the CME Structure and Configuration section:
-
Controllers - Cloud accounts for communication with a specific cloud provider. These include the parameters necessary to connect with your cloud application.
-
Management - Parameters of the Check Point Management Server.
-
Templates - The individual scale sets configured in the account.
Scale-In and Scale-Out Events
Scale sets automatically increase the number of VM instances as application demand increases (Scale-Out) and reduce the number of VM instances as demand decreases (Scale-In).
CME constantly scans, and on each iteration, the load dictates if a scale-out or a scale-in event occurs, or if CME detects a demand that is not too high or too low for the current size of the set, there is no change.
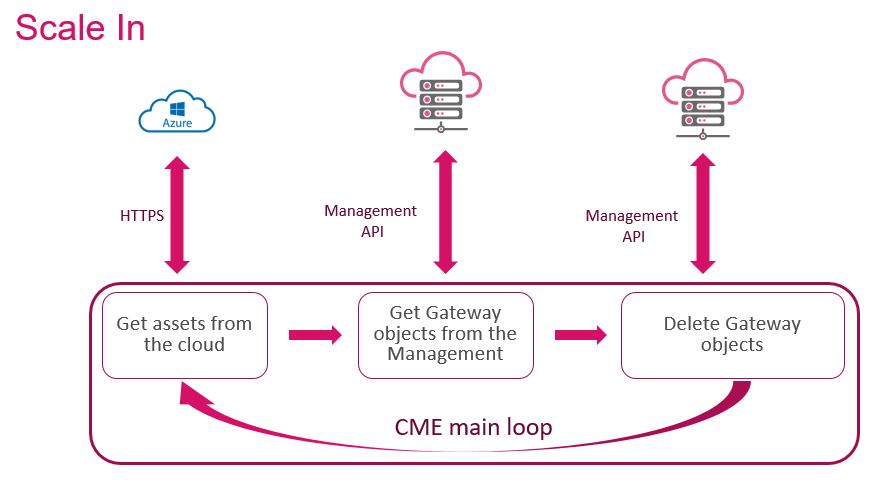
Scale-In
A scale-in event occurs as a result of a decrease in the current load. When a scale-in event triggers, CME designates one or more gateways as candidates for termination. The External Load Balancer stops forwarding new connections to these gateways, and Autoscale ends them. CME detects that these CloudGuard Network Security Gateways are stopped and automatically deletes these gateways from the Check Point Security Management Server's database.
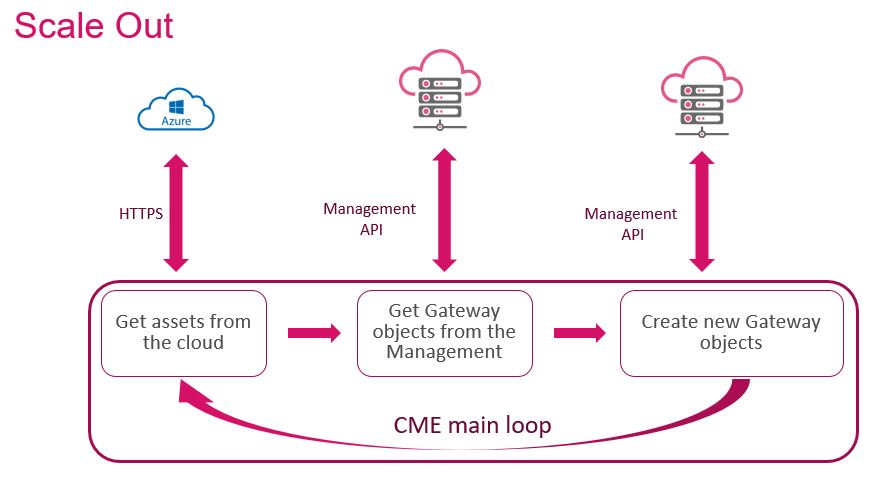
Scale-Out
A scale-out event occurs if the current load increases. When a scale-out event is triggered:
-
The cloud provider auto-scale launches one or more new instances of the Check Point CloudGuard Network Security Gateways.
-
The new instances of CloudGuard Network Security Gateways automatically run the Check Point First Time Configuration Wizard and then reboot.
During the scale-out, CME detects that new CloudGuard Network Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. instances were launched. CME waits until the CloudGuard Network Security Gateways complete to deploy and then automatically:
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. instances were launched. CME waits until the CloudGuard Network Security Gateways complete to deploy and then automatically:
-
Initializes a Secure Internal Communication (SIC
 Secure Internal Communication. The Check Point proprietary mechanism with which Check Point computers that run Check Point software authenticate each other over SSL, for secure communication. This authentication is based on the certificates issued by the ICA on a Check Point Management Server.) channel with these CloudGuard Network Security Gateways.
Secure Internal Communication. The Check Point proprietary mechanism with which Check Point computers that run Check Point software authenticate each other over SSL, for secure communication. This authentication is based on the certificates issued by the ICA on a Check Point Management Server.) channel with these CloudGuard Network Security Gateways. -
Install a restrictive access policy that has only a drop-all cleanup rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. on these CloudGuard Network Security Gateways. For more information see Implied Rules and Restrictive Policy.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. on these CloudGuard Network Security Gateways. For more information see Implied Rules and Restrictive Policy. -
Do more configurations if needed, for example, blade configuration, run user custom scripts, create automatic Access/NAT rules, and more.
-
Installs a Security Policy
 Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. on these CloudGuard Network Security Gateways.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. on these CloudGuard Network Security Gateways.
After the Security Policy installation, these CloudGuard Network Security Gateways start to reply to health probes. The Load Balancer then starts to forward new connections to them. The newly created CloudGuard Network Security Gateways report their status and send logs to CME.