Security Awareness Training
The Security Awareness Training feature in Harmony Email & Collaboration helps organizations create awareness among employees on essential security skills. It includes awareness of phishing simulation emails reflecting recent attacks and interactive training modules.
|
|
Note - The Security Awareness Training is supported only for Exchange Online (Microsoft 365 cloud) mailboxes. |
Creating Security Awareness Training Policy
To create a security awareness training policy:
-
Access the Harmony Email & Collaboration Administrator Portal.
-
From the left navigation panel, click Security Training > Policy.
-
Click Create New Policy Rule.
-
From the Choose SaaS dropdown, select the required option.
-
Office 365 Mail
-
Gmail
-
-
Click Next.
-
Make sure the Rule state is Running.
-
(Optional) In the Rule name field, enter a name for the policy.
-
Click Save.

Notes:
-
By default, the security awareness training policy is applied to all the Microsoft 365 users in your organization.
-
Phishing simulations are not sent via SMTP and therefore do not originate from any Check Point IP address. They are inserted directly into user mailboxes via API, so there is no sending IP range to add to the allowlist.
-
Customizing Security Awareness Training Policy
To customize the security awareness training policy:
-
Click on the security awareness training policy you want to customize.
-
In the Users and groups section, select the users and/or group of users for whom the policy is applicable:
-
To apply the policy to all users and groups in your organization, select All Office 365 users or All Google users.

Note - Group selection is currently not supported for Gmail.
-
To apply the policy to specific users or groups, select the users/groups and click Add to Selected.
-
-
Select a Phishing Simulation Strategy:
- Prioritize the past attack types of the user - Sends phishing simulation emails that reflect recent attack types faced by the users in your organization.
-
None, do not perform simulations - No simulation emails are sent to the users.
-
(Optional) To view the phishing email templates used to send simulation emails to users, click Generated Phishing Simulations (samples).
To view generated phishing simulation samples based on a user’s recent communication patterns, enter the user's email address and click Generate.
-
To exclude simulated phishing scenarios that impersonate internal users, such as executives, managers, or colleagues, select the Include phishing simulations impersonating internal users checkbox in the Simulation Types section.
-
Configure the Simulation Scheduling section.
-
In the Frequency section, select the required frequency of the simulation emails.
-
Weekly
-
Biweekly
-
Monthly
-
Quarterly
-
Yearly

Note - By default, the frequency of the simulation emails is set to Biweekly.
-
-
In the Send randomly on section, select the days to randomly send simulation emails to users.
-
Monday
-
Tuesday
-
Wednesday
-
Thursday
-
Friday
-
Saturday
-
Sunday
-
-
In the Time Range section, select the start time to send emails, end time to stop sending emails, and the required time zone on the selected days.

Note - By default, the time range is set to 9:00 AM to 18:00 PM and the time zone is set to (UTC +00:00) UTC.
-
-
Configure the Action on Failure section.
-
In the Automatically enroll users in follow-up training if they fail consecutive phishing simulations section, select one of the following options:
-
Yes
-
No
-
-
From the Consecutive failures dropdown, select the number of consecutive phishing simulation failures that will trigger automatic enrollment for users in follow-up training.

Notes:
-
By default, the number of consecutive simulation failures is set to 1.
-
If the Automatically enroll users in follow-up training if they fail consecutive phishing simulations option is enabled, the system automatically enrolls users who fail the specified number of consecutive phishing simulations in follow-up training.
-
-
In the Due in (days) field, select the number of days to complete the assigned follow-up training.

Note - By default, the due is set to 7 days. After the due date, Check Point no longer sends any training reminders or notifications to end users.
-
-
-
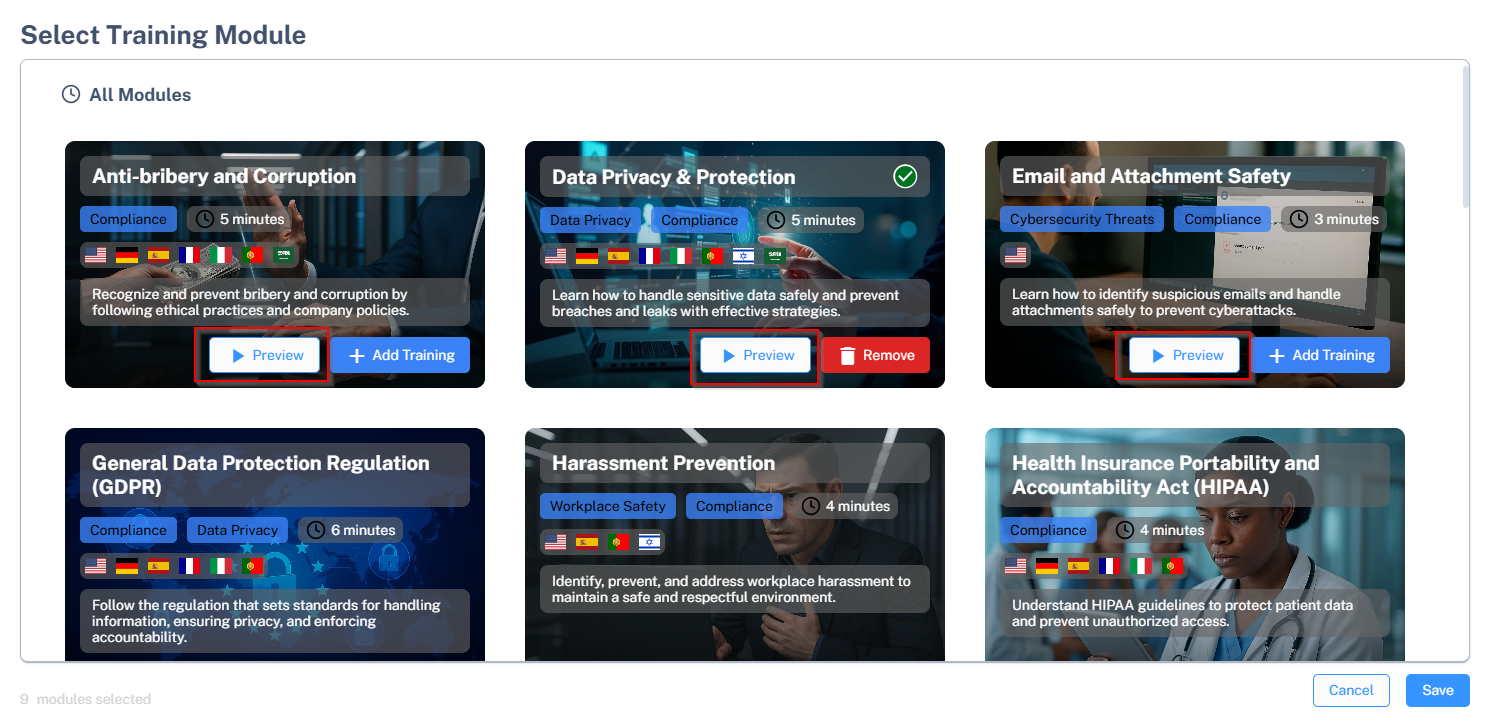
Click Select training modules.
The Select Training Module pop-up displays the available training modules.
Each module provides the following details:
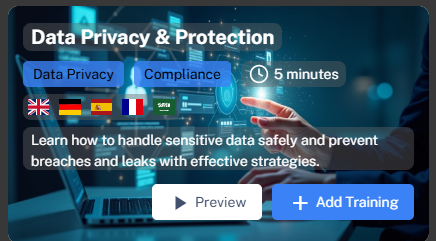
-
The training module name and key concepts in the module.
-
The time duration shows the time required to complete the module.
-
The flags represent the languages available for the training module.
-
(Optional) To view a preview of the training module, click Preview.
After adding a training module to the policy, you must authorize access for the entire organization by granting the necessary permissions. See Authorizing Training Module Access for the Organization.
-
-
Click Add Training for the required modules.
-
Click Save.

Note - The deadline for completing each training is 14 days.
-
-
The Selected training modules section shows the order of the modules assigned to the user.
-
To arrange the training modules in the required order:
-
Click the
 icon.
icon. -
Move the module to the desired position in the order and drop it.
-
-
To remove a selected training module, click the
 icon.
icon.
-
-
To configure settings for the training and reminders for the email notifications, click Advanced settings and do these:
-
In the Training max frequency (days) field, enter the number of days after which the system initiates a new training session.
-
In the Training reminder interval field, enter the number of days after which the system sends a reminder. For example, if you enter 2, the system sends reminder after every 2 days.
-
To configure email notifications for the training and reminders:
-
In the Training invitation subject field, enter the subject for the training invitation email.
-
In the Training invitation body template field, enter the body for the training invitation email.
-
In the Training remind subject field, enter the subject for the training reminder email.
-
In the Training remind body template field, enter the body for the training reminder email.
-
(Optional) In the Phishing simulation banners section, select the Add banner to phishing simulation emails checkbox.

Note - If the Add banner to phishing simulation emails checkbox is enabled, the system adds a banner to every phishing email sent to the user's inbox.
To view the supported placeholders, see Training and Reminder Emails - Supported Placeholders.
-
-
Click Save.
-
-
Click Save.

Notes:
-
Now that the security awareness training policy is configured, the end users receive an email with a link to access the training modules. To allow users to access the training modules, the administrator must authenticate by granting the necessary permissions.
-
When new users are added to an existing Security Awareness Training policy, each user’s completion period starts from the date they are enrolled. Each new user gets the full duration specified in the policy (for example, 90 days) to complete the assigned training course, regardless of when the policy was originally created or when other users were enrolled.
-
Customizing the Sender of Security Awareness Training Notifications
Harmony Email & Collaboration allows you to customize the sender details for security awareness training notifications.
End users receive notifications when they are assigned training modules or when they fail simulated phishing tests. By customizing the sender, organizations can centralize responses to a designated mailbox, which helps security and training managers streamline communication.
|
|
Note - This customization applies only to security awareness training notifications. For simulated phishing emails, the system automatically generates the sender through GenAI to realistically resemble real-world phishing attempts. |
To configure the sender of security awareness training notifications:Go to
-
Access the Harmony Email & Collaboration Administrator Portal.
-
Go to Security Training > Policy.
-
Click Global Settings.
-
In the Configure Global Settings pop-up, scroll down and configure the Custom Notification Sender section.
-
Friendly-From name
-
If no friendly-from name is required, select None.

Note - Some email clients duplicate the sending address to the Friendly-from name.
-
To use a customized name, select Custom and enter the sender name.
-
-
From address
-
To use the default email address, select Default. The default email address is no-reply@checkpoint.com.
-
To use a custom email address, select Custom and enter the email address.
-
If you use the default sender or any email address under your domain, you must add the Check Point statement to the custom domain's DNS to prevent SPF and DMARC failures.
include:spfa.cpmails.com -
The custom domain must be one of the protected domains in your Infinity Portal tenant.

Notes:
-
-
Reply-to address
-
To use From address as the Reply-to address, select Same as From address.
-
To use a custom email address, select Custom and enter the email address.
-
-
-
Click Save.
Adding a Banner to Phishing Simulation Emails
Harmony Email & Collaboration allows administrators to add a banner to phishing simulation emails that resembles the external sender warning banner.
To add a banner to phishing simulation emails:
-
Access the Harmony Email & Collaboration Administrator Portal.
-
Go to Security Training > Policy.
-
Click Global Settings.
-
In the Configure Global Settings pop-up, scroll down to the Phishing simulation banners section.
-
Select the Add banner to phishing simulation emails checkbox.

Note - If the Add banner to phishing simulation emails checkbox is enabled, the system adds a banner to every phishing email sent to the user's inbox.
-
Click Save.
Authorizing Training Module Access for the Organization
Harmony Email & Collaboration allows users to access the training modules using the link provided in the email notification.
The administrator must authorize access for the entire organization by granting the necessary permissions.
To authorize the Microsoft login permissions for training modules:
-
Click on the link provided in the email.
or
You can authorize from the Preview page while configuring the security awareness training policy. See Select the Training Modules.
Click Preview.
-
In the sign in page, click Sign in with Microsoft.
-
Enter the admin credentials and sign in.
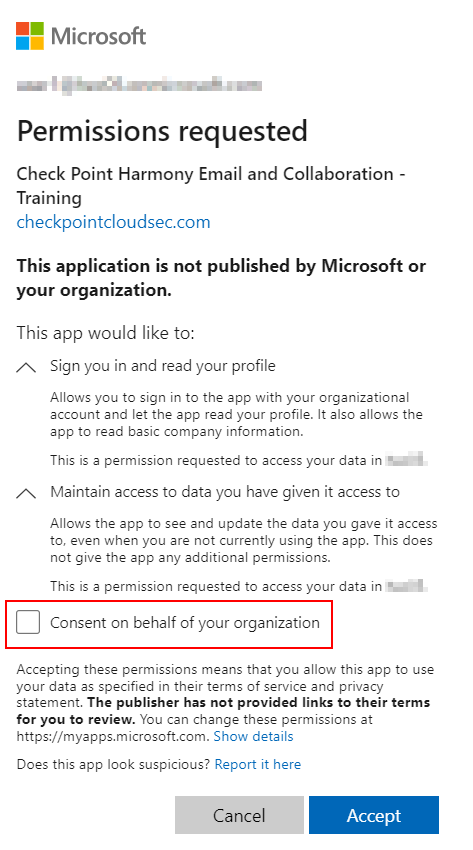
The Permissions requested pop-up appears for the Check Point Harmony Email & Collaboration – Training application and requests the necessary permissions. See Required Permissions for Microsoft Login Authorization.
-
To allow end users to sign in using Microsoft credentials, select the Consent on behalf of your organization checkbox.

Note - To grant permission by selecting the Consent on behalf of your organization checkbox, allowing users to sign in with Microsoft. The administrator must have one of the following roles:
-
Global Administrator
-
Privileged Role Administrator
-
Cloud Application Administrator
-
Application Administrator
-
A custom directory role that includes the permission to grant consent on behalf of all users
-
-
Click Accept.
End users can now sign in with their organization's Microsoft credentials using the link provided in the email to access the training modules.
Security Awareness Training Email Headers
Check Point’s Security Awareness Training emails include a dedicated header that allows security teams to quickly identify them as training messages.
Header Name:
X-Check-Point-Security-Awareness-Training
Header Values:
-
phishing-simulation – Indicates a simulated phishing email.
-
training-notification – Indicates the email as a training invitation or reminder.
-
phishing-simulation-feedback – Identifies the email as feedback provided to a user after they respond to a phishing simulation email.
Required Permissions for Microsoft Login Authorization
|
Permissions required from Microsoft/Google |
Functions performed by Harmony Email & Collaboration |
|---|---|
| Sign you in and read your profile | Allows users to sign in to the app and allows the app to read the profile of signed-in users. It also allows the app to read basic company information of signed-in users. |
| Maintain access to data you have given it access to | Allows the app to view and update the signed-in user data even when you are not currently using the app. |
Training and Reminder Emails - Supported Placeholders
While configuring email notifications for training and reminders in Security Awareness Training, the administrators can use these placeholders to replace content dynamically.
|
Placeholder Name |
Placeholder Value |
|---|---|
|
Email recipient name |
{recipient_name} |
|
Training module name |
{training_name} |
|
Training module description |
{training_description} |
|
Date before which the training module must be completed |
{training_due_date} |
|
Length of the training mode in minutes or hours |
{training_duration} |
|
Number of days remaining to complete the training module |
{training_days_left} |
Branding the Security Awareness Training Web Page
To customize the training module interface and phishing simulation web pages to reflect your organization’s branding:
-
Go to Security Training > Policy.
-
Click Configuration next to Security training policies from the top of the page.
-
In the Branding of user interaction (landing pages, course screens) section, select one of these:
-
To show the web pages and course screens that matches your organization's branding, select Auto-brand pages with AI for my domain (recommended). Harmony Email & Collaboration uses AI and auto-brands the pages based on your organizational domain.
-
To use Check Point's branding, select Use Check Point branding.
-
-
Click Save.
Security Awareness Training Domains
While emails will be delivered, some URLs may be blocked upon clicking due to security tools. To prevent this, allowlist the following domains and their subdomains for both senders and links in your non-Check Point security solutions.
-
us.login-microsoftonline.co
-
eu.login-microsoftonline.co
-
au.login-microsoftonline.co
-
me.login-microsoftonline.co
-
ca.login-microsoftonline.co
-
uk.login-microsoftonline.co
-
in.login-microsoftonline.co
-
us.office356.co
-
eu.office356.co
-
au.office356.co
-
me.office356.co
-
ca.office356.co
-
uk.office356.co
-
in.office356.co
-
us.office356.email
-
eu.office356.email
-
au.office356.email
-
me.office356.email
-
ca.office356.email
-
uk.office356.email
-
in.office356.email
-
us.redeem-amazon.com
-
eu.redeem-amazon.com
-
au.redeem-amazon.com
-
me.redeem-amazon.com
-
ca.redeem-amazon.com
-
uk.redeem-amazon.com
-
in.redeem-amazon.com
-
us.tracking-amazon.com
-
eu.tracking-amazon.com
-
au.tracking-amazon.com
-
me.tracking-amazon.com
-
ca.tracking-amazon.com
-
uk.tracking-amazon.com
-
in.tracking-amazon.com
-
us.update-fedex.com
-
eu.update-fedex.com
-
au.update-fedex.com
-
me.update-fedex.com
-
ca.update-fedex.com
-
uk.update-fedex.com
-
in.update-fedex.com
-
us.training-cp.com
-
ca.training-cp.com
-
eu.training-cp.com
-
uk.training-cp.com
-
au.training-cp.com
-
me.training-cp.com
-
in.training-cp.com
-
us.fedex.email
-
ca.fedex.email
-
eu.fedex.email
-
uk.fedex.email
-
au.fedex.email
-
me.fedex.email
-
in.fedex.email
-
us.dnc.cloud
-
ca.dnc.cloud
-
eu.dnc.cloud
-
uk.dnc.cloud
-
au.dnc.cloud
-
me.dnc.cloud
-
in.dnc.cloud
-
us.rnc.cloud
-
ca.rnc.cloud
-
eu.rnc.cloud
-
uk.rnc.cloud
-
au.rnc.cloud
-
me.rnc.cloud
-
in.rnc.cloud
-
us.avnn.us
-
ca.avnn.us
-
eu.avnn.us
-
uk.avnn.us
-
au.avnn.us
-
me.avnn.us
-
in.avnn.us
Monitoring User Interactions with Phishing Simulations
The Security Training Dashboard shows an overview of training completion and phishing simulation performance for organization members using widgets, charts, and tables. It also shows individual training statuses and user details, enabling administrators to analyze the organization's security awareness and readiness against phishing threats.
To view the Dashboard page, click Security Training > Dashboard.
To select a time frame for the Dashboard, select an option from the dropdown next to Dashboard at the top of the page.
-
Last 24h
-
Last 7 days
-
Last 30 days
-
Last 12 months
-
Custom
To export the details to a PDF, click Export to PDF.
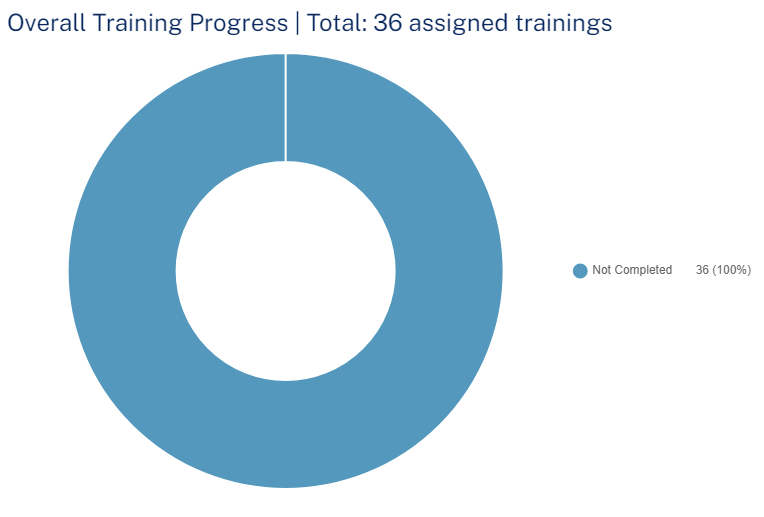
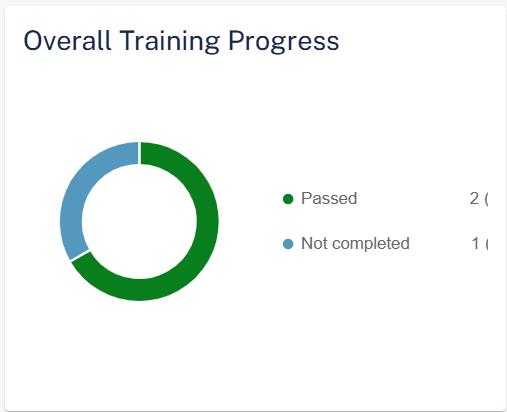
Overall Training Progress
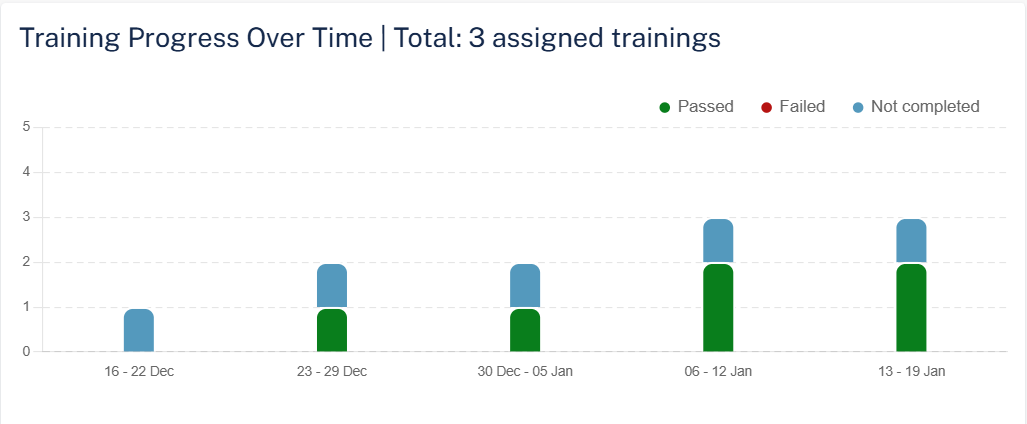
The Overall Training Progress widget shows the number of trainings assigned and their status in the selected time frame.
-
Passed
-
Failed
-
Not Completed
To view specific assigned trainings, click the relevant field in the widget, and the system shows the filtered trainings on the Users page.
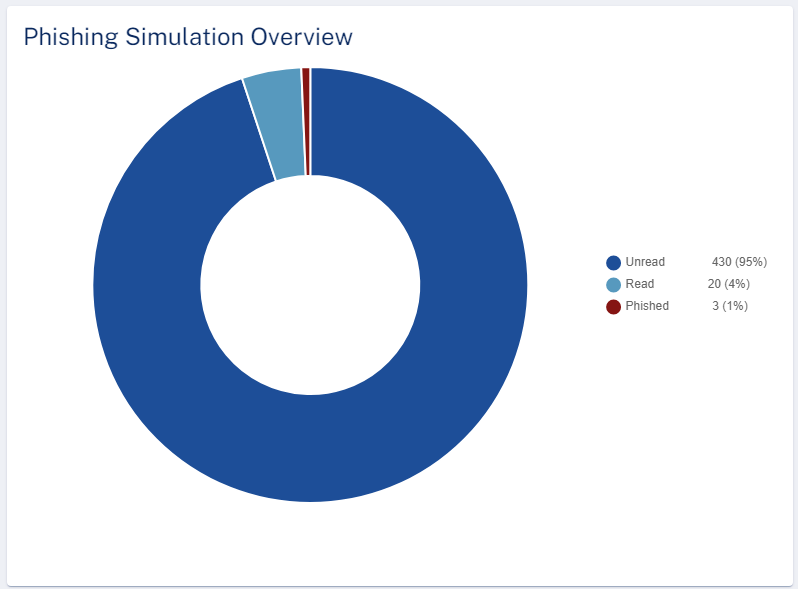
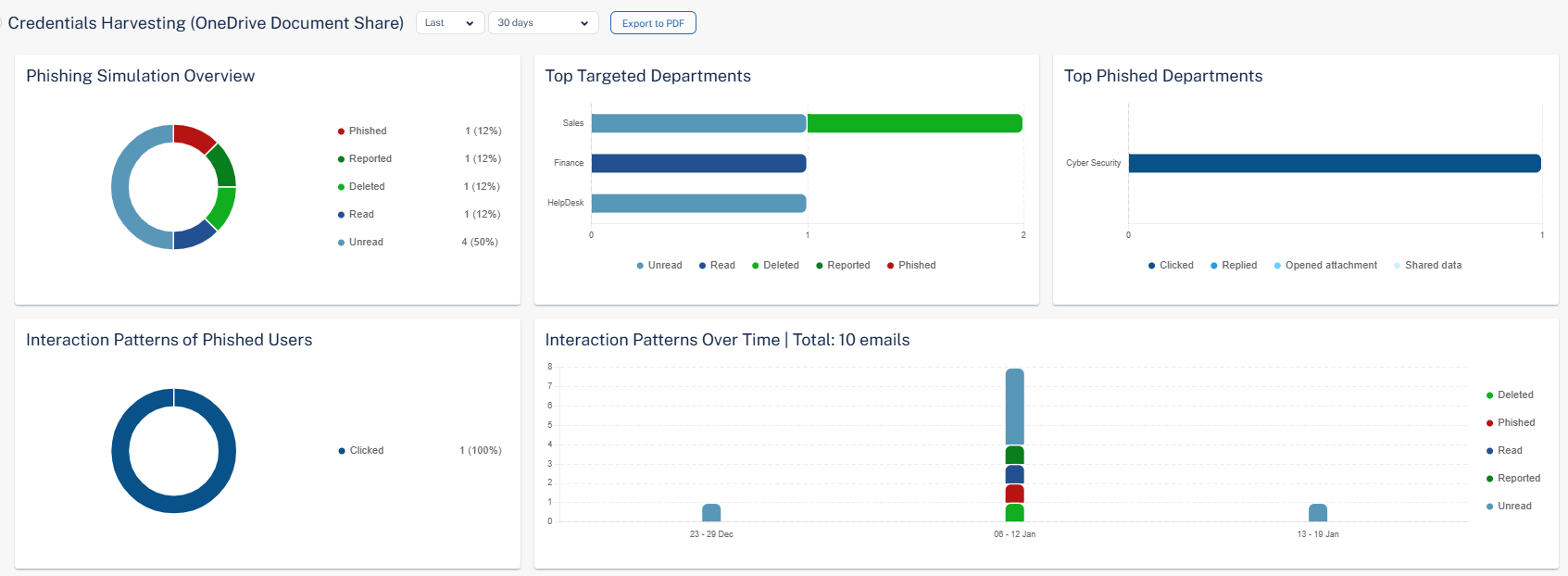
Phishing Simulation Overview
The Phishing Simulation Overview widget shows the number of phishing simulation emails sent and their status in the selected time frame.
-
Unread
-
Read
-
Deleted
-
Reported
-
Phished
-
Clicked
-
Scanned QR Code
-
Replied
-
Forwarded
-
Opened attachment
-
Called unknown number
-
Shared data
-
To view specific phishing simulations, click the relevant field in the widget, and the system shows the filtered phishing simulations on the Users page.
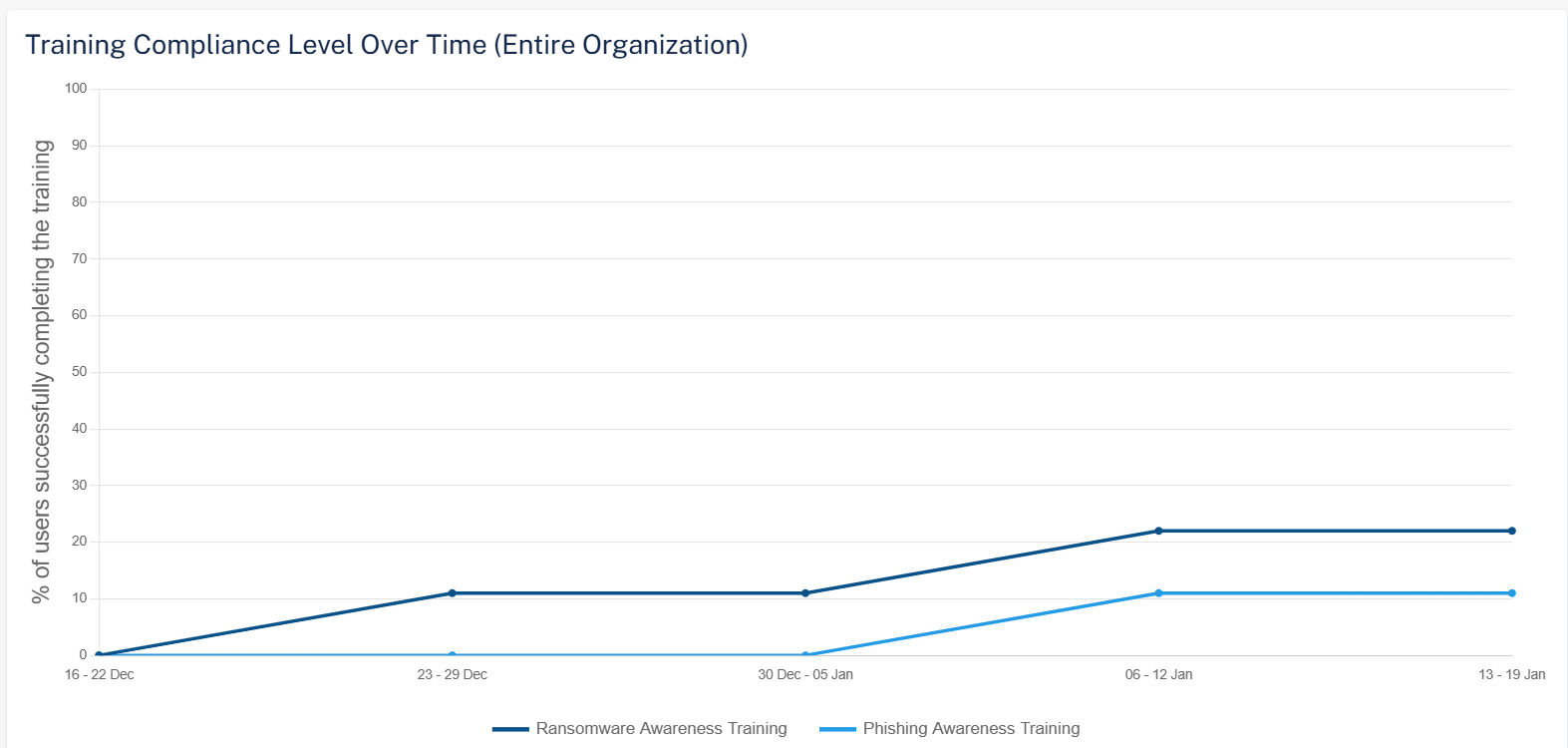
Training Compliance Level Over Time (Entire Organization)
The Training Compliance Level Over Time (Entire Organization) widget shows the percentage of users in the organization who have completed the training in the selected time frame.
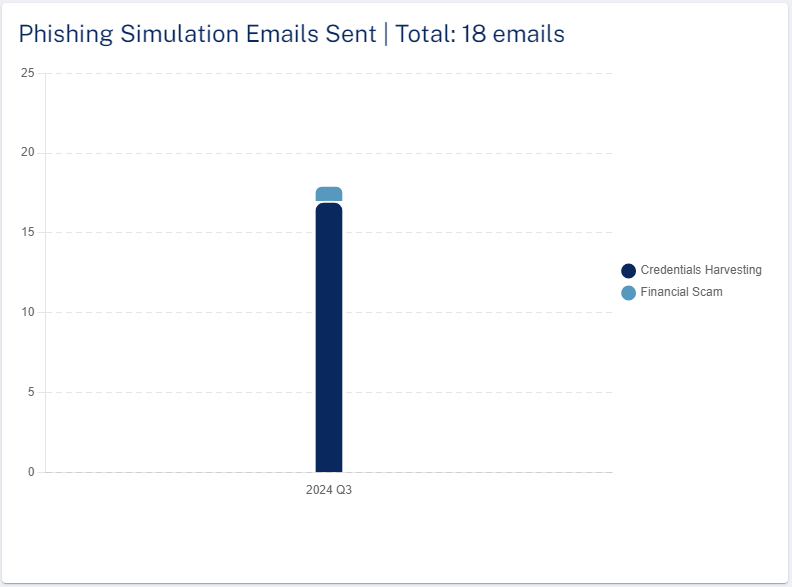
Phishing Simulation Emails Sent
The Phishing Simulation Emails Sent widget shows the total number of phishing simulation emails sent and their status in the selected time frame.
Phishing Simulation by Attack Type
The Phishing Simulation by Attack Type widget shows the number of phishing simulation emails sent based on the attack type in the selected time frame.
To view specific phishing simulation details based on the attack type, click the relevant field in the widget, and the system shows the filtered phishing simulations by attack type on the Users page.
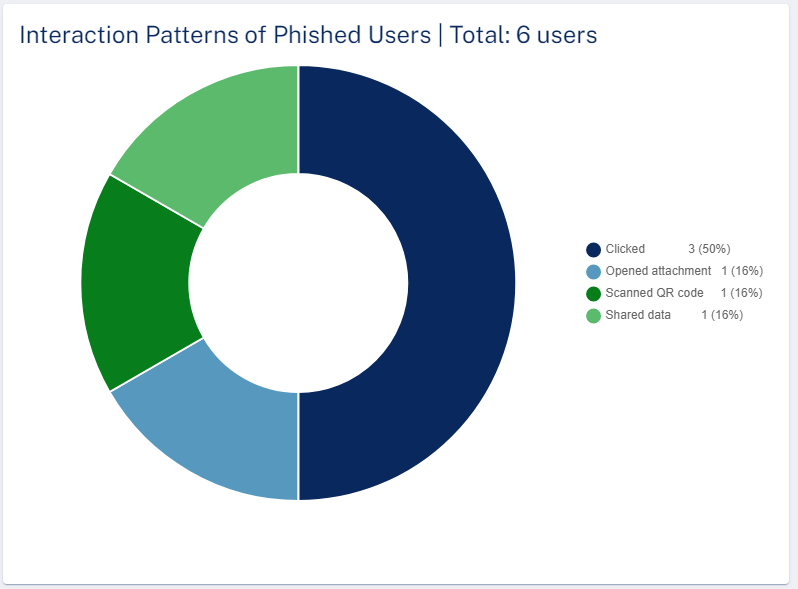
Interaction Patterns of Phished Users
The Interaction Patterns of Phished Users widget shows the total number of phished emails and their interaction status in the selected time frame.
To view specific phished emails and their interactions, click the relevant field in the widget, and the system shows the filtered interactions of phished users on the Users page.
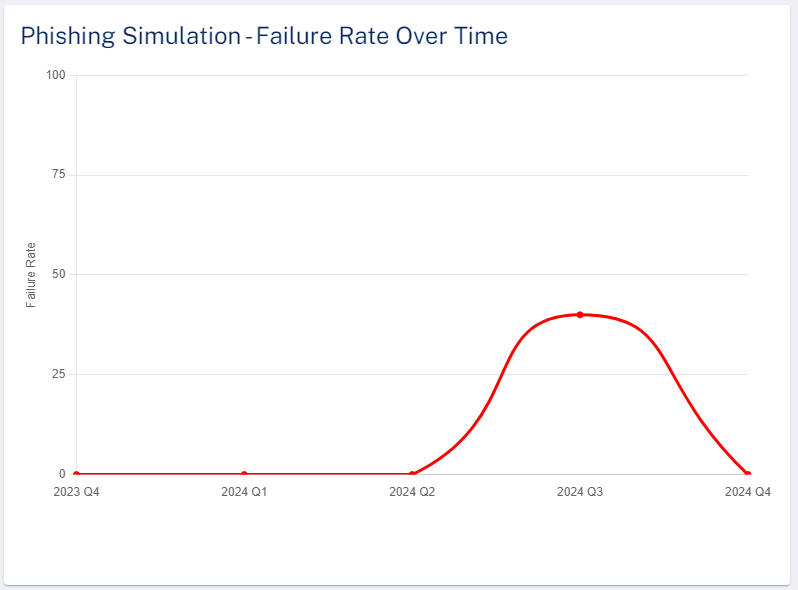
Phishing Simulation - Failure Rate Over Time
The Phishing Simulation - Failure Rate Over Time widget shows the percentage of emails that have failed the simulation in the selected time frame.
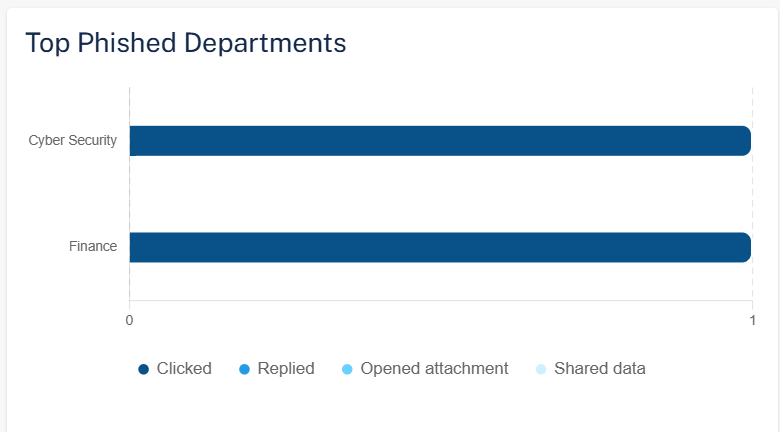
Top Phished Departments
The Top Phished Departments widget shows the top ten departments in the organization with the most phished users in the selected time frame.
To view specific department in the organization with the most phished users, click the relevant field in the widget, and the system shows the filtered departments on the Users page.
Top Phished Users
The Top Phished Users table shows the users that are phished more times in the selected time frame.
|
Column |
Description |
|---|---|
|
Name |
Name of the user in the organization. |
|
Title |
Job title of the user in the organization. |
|
Department |
Department the user belongs to within the organization. |
|
Failures |
Number of phishing emails opened. |
Monitoring User Training Progress
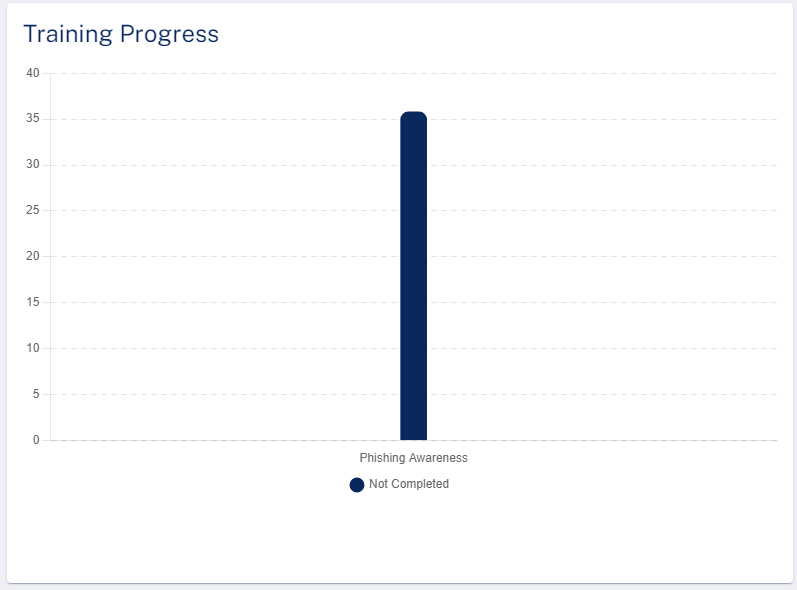
Training Progress
The Training Progress widget shows the training modules and their status in the selected time frame.
Training Status
The Training Status table shows the status of each training module.
|
Column |
Description |
|---|---|
|
Training |
Training module name |
|
Policy |
Name of the policy. |
|
Start Date |
Date on which the training module is assigned to the users. |
|
Training Status |
Training status:
|
|
Users |
Users that are assigned the training module. |
|
Passed |
Percentage of users that have passed in the training module. |
|
Failed |
Percentage of users that have failed in the training module. |
|
Not Completed |
Percentage of users that have not started the training module. |
Users
The Users table shows the phishing simulation emails sent to the users and their training status in the selected time frame.
|
Column |
Description |
|---|---|
|
Name |
Name of the user in the organization. |
|
Title |
Job title of the user in the organization. |
|
Department |
Department the user belongs to within the organization. |
|
Phishing Simulation |
Type of simulation email sent to the user and their status. Click on the simulation name to view analytics filtered specifically for that simulation. See Monitoring Phishing Simulations. |
|
Awareness Training |
Training module name and their status. Click on the training module name to view analytics filtered specifically for that module. See Monitoring User Awareness Training Progress. |
Monitoring Phishing Simulations
To view the details of a specific phishing simulation, click on the required phishing simulation name in the Phishing Simulation column of the Users table.
Harmony Email & Collaboration redirects you to the relevant phishing simulation dashboard.
To select a time frame for the phishing simulation, select an option from the drop-down next to the phishing simulation name at the top of the page.
-
Last 24h
-
Last 7 days
-
Last 30 days
-
Last 12 months
-
Custom
To export the details to a PDF, click Export to PDF.
Phishing Simulation Overview
The Phishing Simulation Overview widget shows the number of phishing simulation emails sent and their status for the selected phishing simulation in the selected time frame.
-
Unread
-
Read
-
Deleted
-
Reported
-
Phished
-
Clicked
-
Scanned QR Code
-
Replied
-
Forwarded
-
Opened attachment
-
Called unknown number
-
Shared data
-
Top Targeted Departments
The Top Targeted Departments widget shows the top ten targeted departments in the organization with the most phished users for the selected phishing simulation in the selected time frame.
Top Phished Departments
The Top Phished Departments widget shows the top ten departments in the organization with the most phished users for the selected phishing simulation in the selected time frame.
-
Clicked
-
Replied
-
Opened attachment
-
Shared data
Interaction Patterns of Phished Users
The Interaction Patterns of Phished Users widget shows the total number of phished emails and their interaction status for the selected phishing simulation in the selected time frame.
-
Clicked
-
Replied
-
Opened attachment
-
Shared data
-
Scanned QR Code
Interaction Patterns Over Time
The Interaction Patterns Over Time widget shows the total number of phished emails sent to the users and their interaction status for the selected phishing simulation in the selected time frame.
-
Unread
-
Read
-
Deleted
-
Reported
-
Phished
-
Scanned QR Code
User Interaction
The User Interaction table shows the phishing simulation emails sent to the users and their training status in the selected time frame.
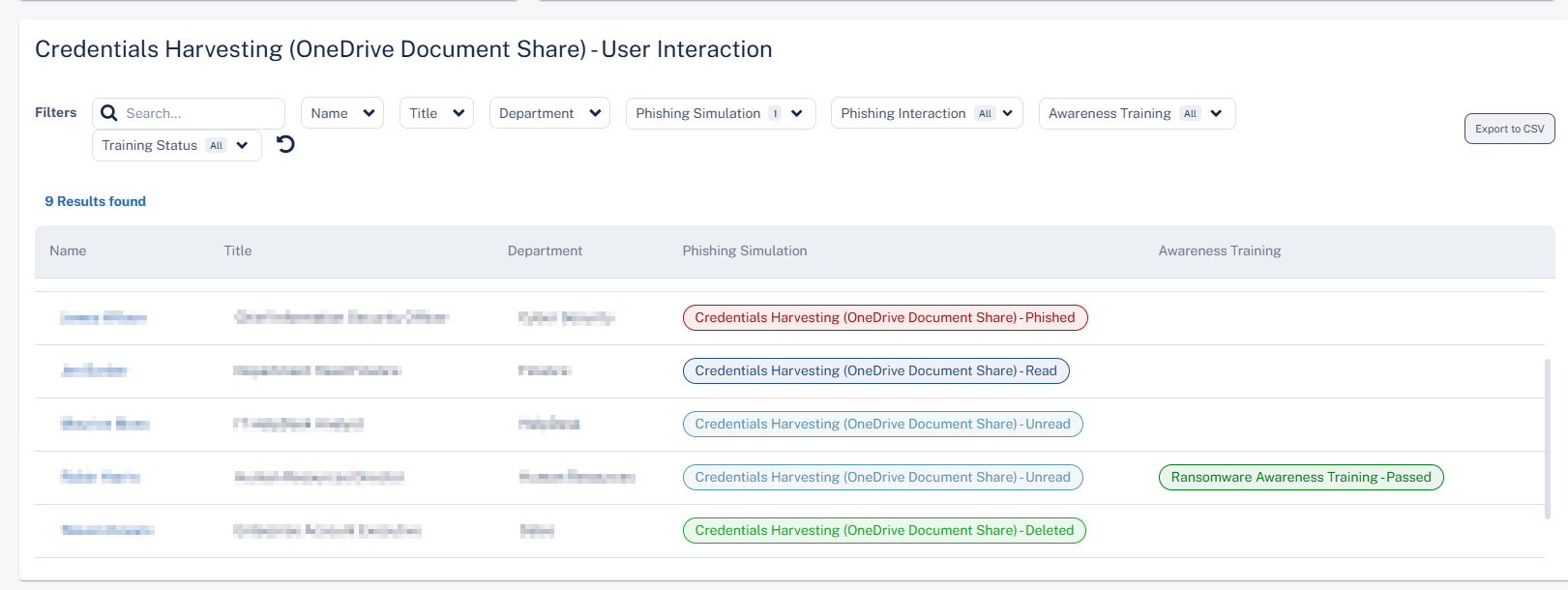
|
Column |
Description |
|---|---|
|
Name |
Name of the user in the organization. |
|
Title |
Job title of the user in the organization. |
|
Department |
Department the user belongs to within the organization. |
|
Phishing Simulation |
Type of simulation email sent to the user and their status. Click on the simulation name to view analytics filtered specifically for that simulation. See Monitoring Phishing Simulations. |
|
Awareness Training |
Training module name and their status. Click on the training module name to view analytics filtered specifically for that module. See Monitoring User Awareness Training Progress. |
Monitoring User Awareness Training Progress
To view the progress of a specific training module, click on the training module name in the Awareness Training column of the Users table.
Harmony Email & Collaboration redirects you to the relevant awareness training module progress dashboard.
To select a time frame for the training module, select an option from the drop-down next to the awareness training module name at the top of the page.
-
Last 24h
-
Last 7 days
-
Last 30 days
-
Last 12 months
-
Custom
To export the details to a PDF, click Export to PDF.
Overall Training Progress
The Overall Training Progress widget shows the number of training modules and their status for the selected training module in the selected time frame.
-
Passed
-
Failed
-
Not Completed
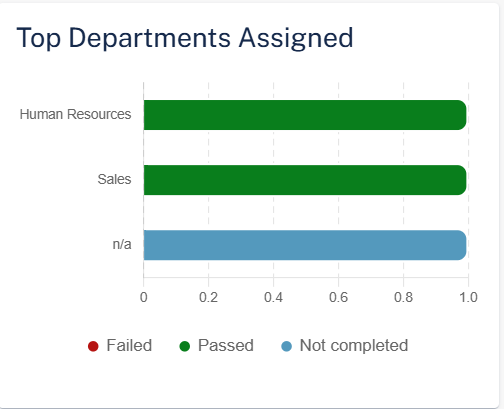
Top Departments Assigned
The Top Departments Assigned widget shows the top ten departments in the organization assigned to the selected training module and their status in the selected time frame.
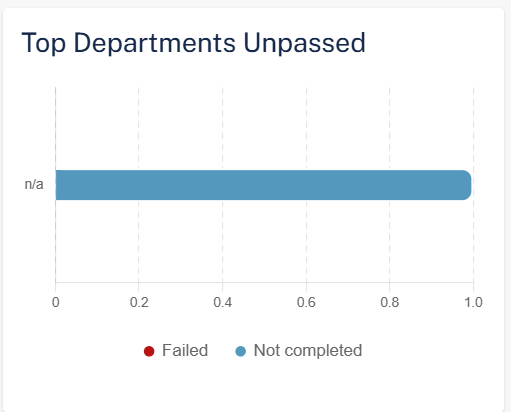
Top Departments Unpassed
The Top Departments unpassed widget shows the top ten departments in the organization that did not pass the selected training module in the selected time frame.
-
Failed
-
Not Completed
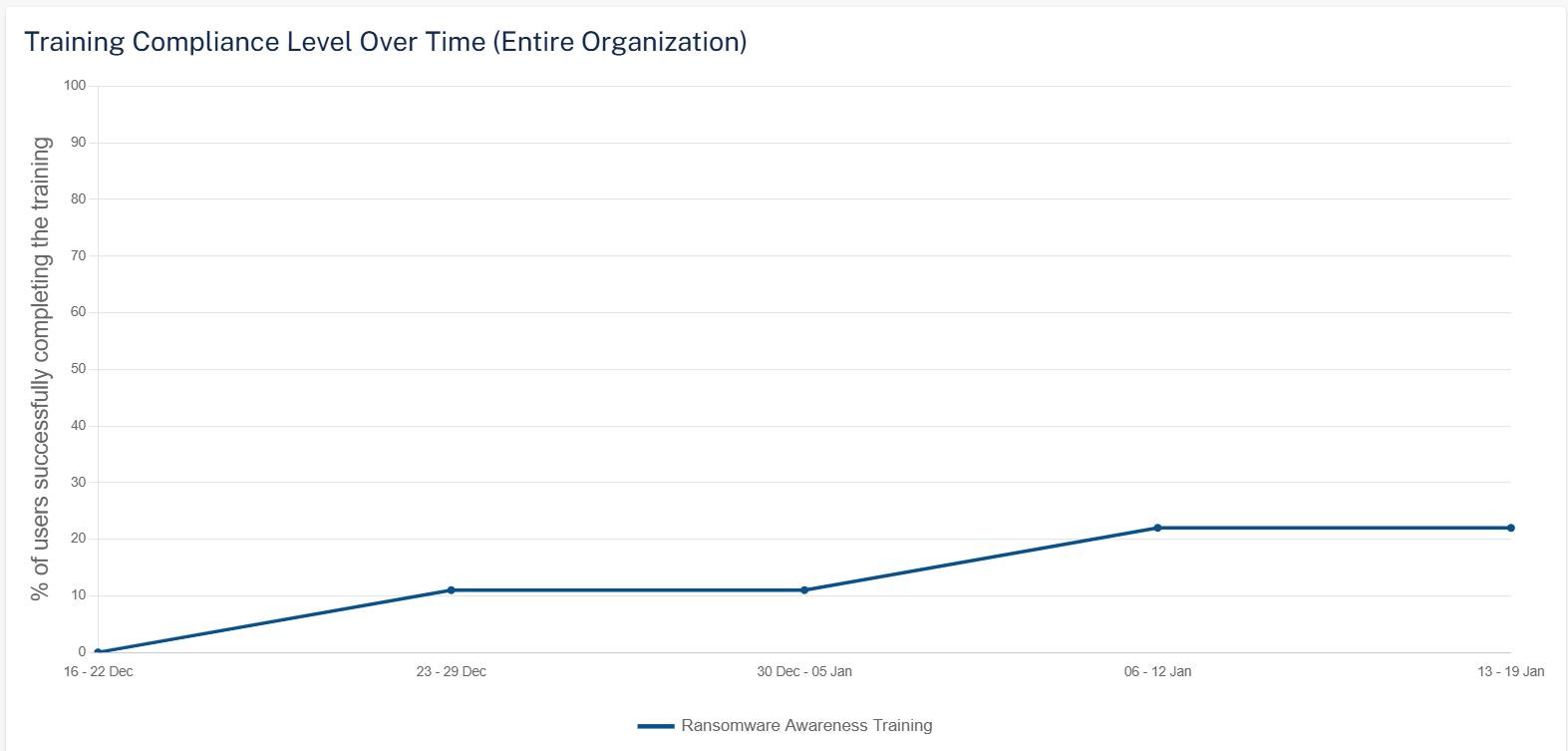
Training Compliance Level Over Time (Entire Organization)
The Training Compliance Level Over Time (Entire Organization) widget shows the percentage of users in the organization who completed the training for the selected training module in the selected time frame.
Training Progress Over Time
The Training Progress Over Time widget shows the number of trainings assigned and their status for the selected training module in the selected time frame.
User Progress
The User Progress table shows the phishing simulation emails sent to the users and their training status in the selected time frame.
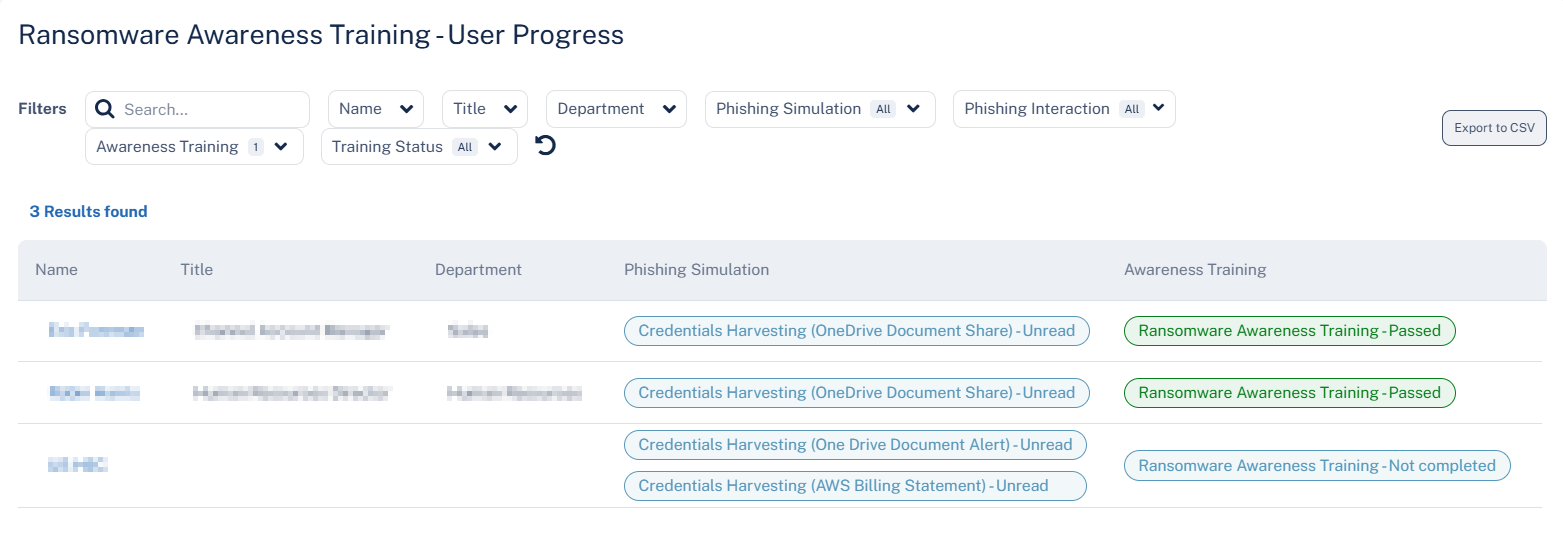
|
Column |
Description |
|---|---|
|
Name |
Name of the user in the organization. |
|
Title |
Job title of the user in the organization. |
|
Department |
Department the user belongs to within the organization. |
|
Phishing Simulation |
Type of simulation email sent to the user and their status. |
|
Awareness Training |
Training module name and their status. |
Training Log
The Training Log table shows the users and their training status in the selected time frame.
|
Column |
Description |
|---|---|
|
Name |
Name of the user in the organization. |
|
Title |
Job title of the user in the organization. |
|
Department |
Department the user belongs to within the organization. |
|
Days Left |
Number of days left to complete the training module. |
|
Training |
Name of the training module. |
|
Status |
Status of the training module.
|
|
Status Details |
Detailed information about the status. |
|
Time |
Date and Time of the training started. |
Phishing Simulations Live Activity Log
The Phishing Simulations Live Activity Log table shows the simulation emails sent to the users and their status.
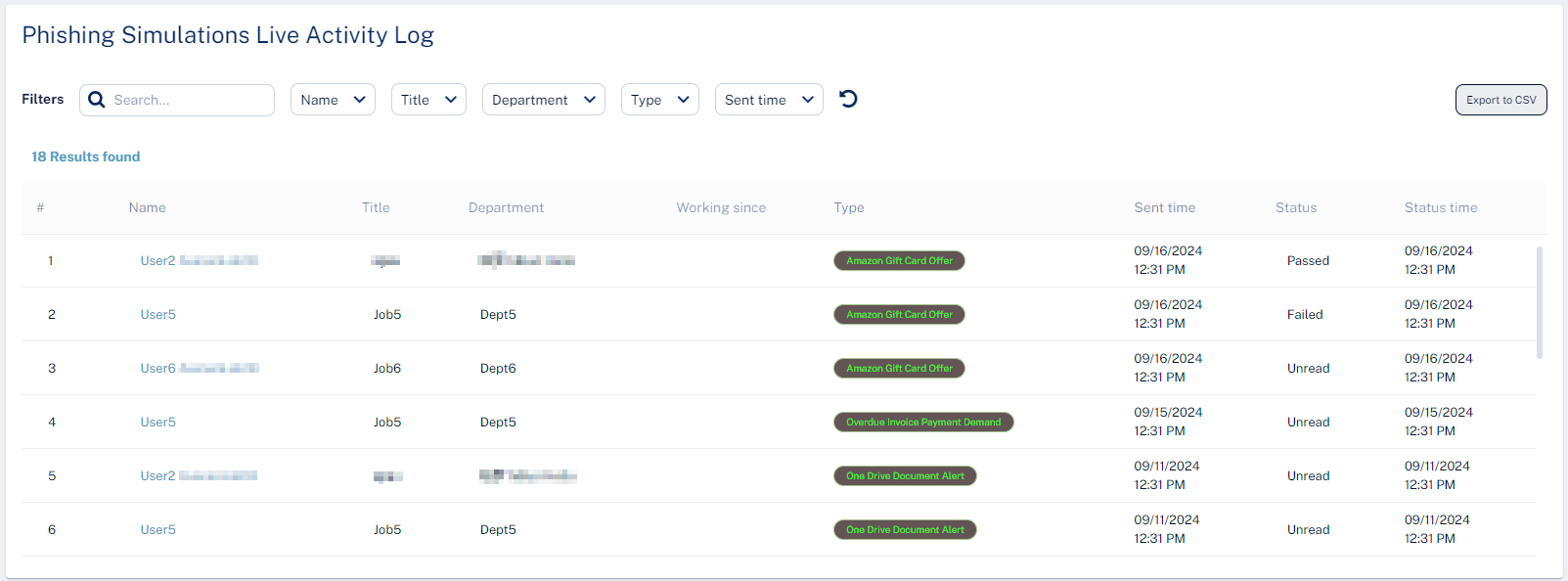
|
Column |
Description |
|---|---|
|
Name |
Name of the user in the organization. |
|
Title |
Job title of the user in the organization. |
|
Department |
Department the user belongs to within the organization. |
|
Simulation |
Type of simulation email sent to the user. |
|
Sent time |
Date and time at which the simulation email is sent. |
|
Status |
Status of the simulation email.
|
|
Status time |
Time at which the status is received. |
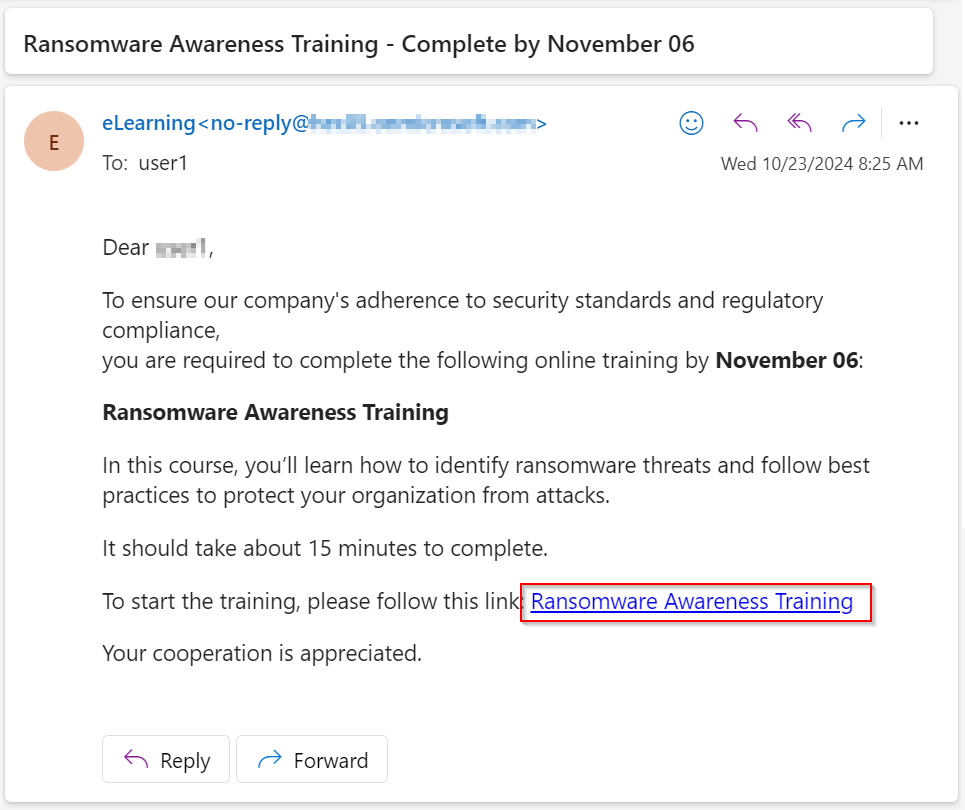
Security Awareness Training - End User Experience
As per the security training policy configured by the administrator,
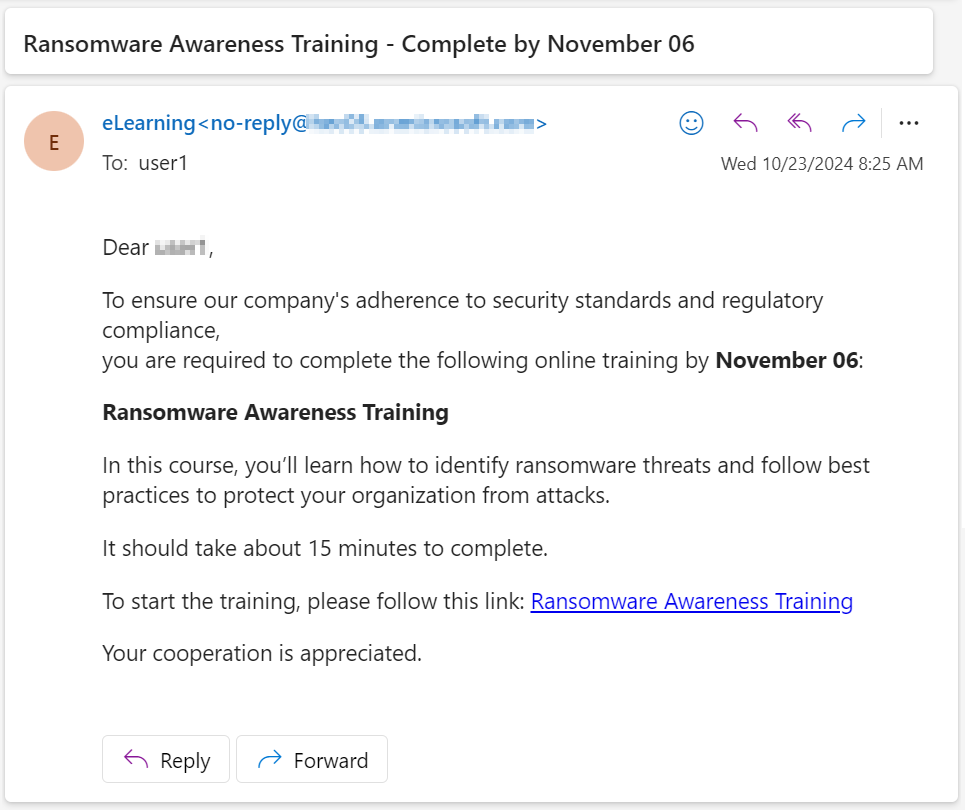
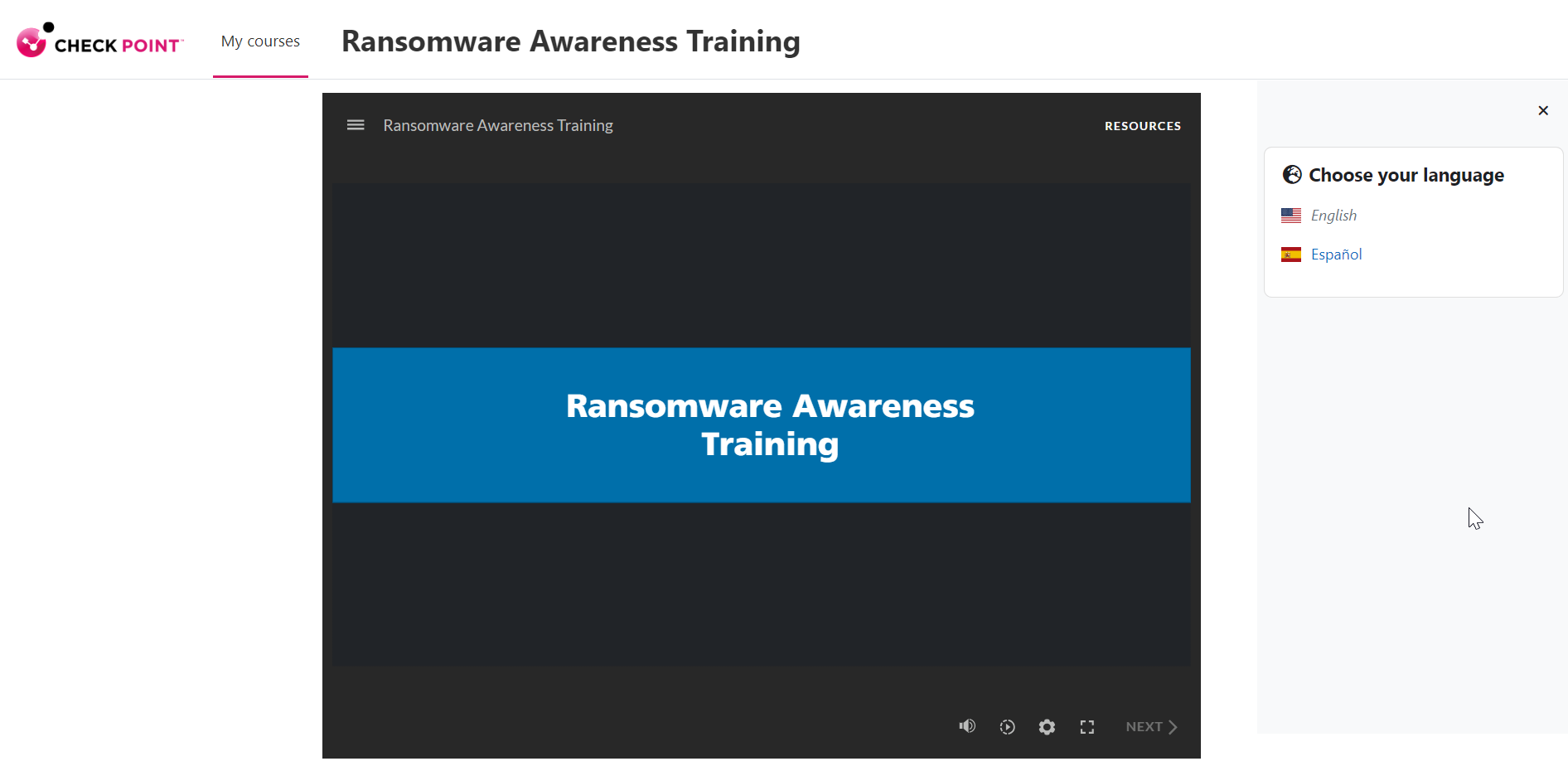
To start the training module:
-
Click the link provided in the email.
The Welcome to Security Awareness Training page appears.
-
Click Sign in with Microsoft.
-
Enter your organization's Microsoft credentials and sign in.
The training module page appears.
-
(Optional) If the training module is available in multiple languages, the Choose your language widget appears to the right of the screen. Select the required language.

Note - The system determines the user's language for phishing simulation emails and training modules based on Microsoft account attributes:
-
preferredLanguage: If this attribute is set, the system uses it as the primary language (if supported).
-
usageLocation: If preferredLanguage is not defined. By default, the system selects the primary language of the country specified in usageLocation.
For more information about supported languages, see Supported Languages for Phishing Simulations and Supported Languages for Training Modules.
-
-
(Optional) To view the different sections in the training module, click the
 icon.
icon.The Menu appears, displaying the different sections in the training module.
-
If required, click Start to begin the training.
The training includes a quiz with multiple questions to help understand the content. It also covers key use cases and provides strategies to protect against security threats.
Supported Languages for Phishing Simulations
Harmony Email & Collaboration supports these languages for phishing simulation emails:
-
Arabic
-
Czech
-
English
-
French
-
German
-
Greek
-
Hebrew
-
Polish
-
Portuguese
-
Russian
-
Spanish
-
Turkish
Supported Languages for Training Modules
Harmony Email & Collaboration supports these languages for training modules:
-
Arabic
-
English (US)
-
French
-
German
-
Hebrew
-
Spanish
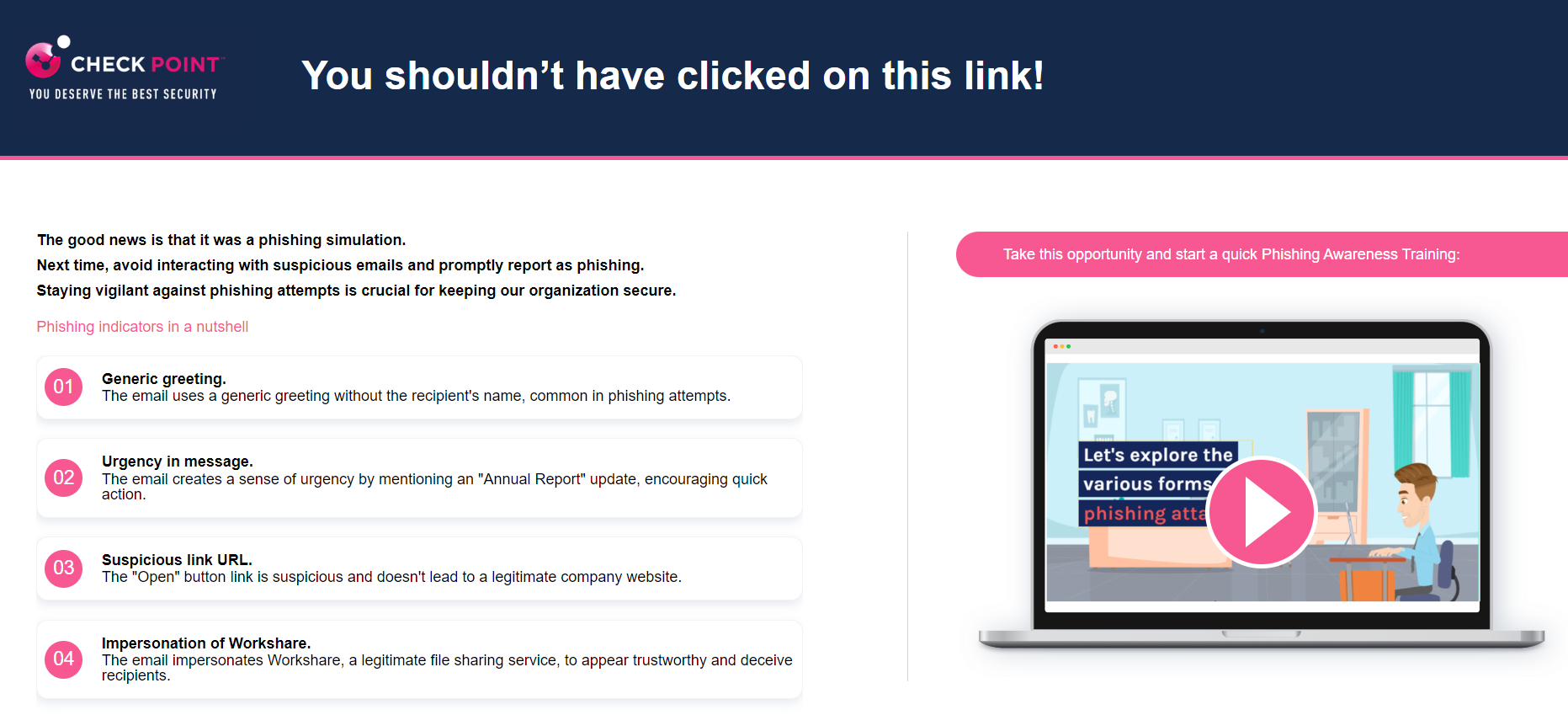
Phishing Simulation Email - End User Experience
As per the security training policy configured by the administrator, the end-user receives phishing simulation emails periodically. When a user clicks a link in these emails, a web page displays the risk indicators relevant to the simulation and allows the user to take the Phishing Awareness Training.