Leaked Credentials
The Leaked Credentials add-on enables automated detection and management of compromised user credentials exposed on the deep and dark web. It strengthens your organization’s identity protection by providing early alerts and actionable intelligence to defend against:
-
Account takeover attempts
-
Unauthorized access using stolen credentials
-
Credential-based phishing and fraud
-
Leaks of corporate and personal data
Overview
When a leaked credential is detected, the Leaked Credentials add-on monitors external sources for compromised credentials and generates a security event in the Harmony Email & Collaboration Administrator Portal, allowing administrators to take immediate action, such as resetting passwords or blocking access, to contain the threat.
Key Features
-
Real-Time Credential Monitoring: Continuously scans deep and dark web sources for compromised credentials.
-
Automated Security Event Generation: Creates a security event for each detected leak.
-
Early Warning Alerts: Notifies administrators of exposed credentials, enabling timely response actions such as password resets.
-
Historical Exposure Tracking: Provides visibility into past credential exposures for risk assessment and remediation.
Benefits
-
Instantly detects exposed employee credentials from breach dumps and underground sources.
-
Enables immediate remediation by blocking users or enforcing password resets before account compromise.
-
Streamlines incident response by integrating exposure events into existing SIEM workflows.
Activating Leaked Credentials
To activate the Leaked Credentials add-on for Harmony Email & Collaboration, contact your Check Point representative.
Leaked Credential Collection Sources
The Leaked Credentials add-on for Harmony Email & Collaboration collects leaked credentials from multiple sources across both the open web and underground ecosystems. These include:
-
Telegram: Channels and groups that share credentials, fullz (complete identity profiles), and malware logs.
-
File-sharing platforms: Services such as GoFile are commonly used to distribute malware logs and credential dumps.
-
VirusTotal (VT): Credential data extracted from malware samples submitted to the platform.
-
Cybercrime forums: A curated set of high-value deep and dark web forums that directly or indirectly contribute to credential exposure. These include, but are not limited to:
-
DarkForums
-
Exploit
-
Cracked
-
Cracking
-
BHF
-
Dread
-
Leakbase
-
BreachForums
-
This multi-source approach enables the comprehensive and timely aggregation of compromised credentials, enhancing visibility across a broad threat landscape.
|
|
Note - This list is partial and is continuously updated to reflect changes in adversary infrastructure and intelligence collection capabilities. |
Reviewing Leaked Credentials Security Events
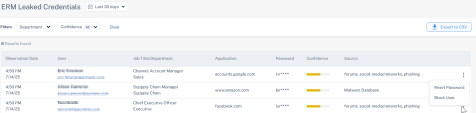
The ERM Leaked Credentials page provides a list of security events for all compromised credentials associated with your organization.
To view the ERM Leaked Credentials page, access the Harmony Email & Collaboration Administrator Portal. From left navigational panel, click Leaked Credentials.
|
|
Note - The ERM Leaked Credentials page appears only when you have a valid license for the Leaked Credentials add-on. |
Extending the Time Frame of the Security Events
By default, the ERM Leaked Credentials page shows security events for the last 6 months.
To view security events for specific time periods, select a time frame from the drop-down at the top of the page.
-
Last 24 hours
-
Last 7 days
-
Last 30 days
-
Last 3 months
-
Last 6 months
To export the details to a CSV, click Export to CSV.
ERM Leaked Credentials Table
The ERM Leaked Credentials table shows the security events and details about compromised credentials within your organization, including their confidence levels and user information, in the selected time frame.
Each record or security event in the ERM Leaked Credentials table is based on the following attributes:
-
User
-
Application
-
Password
For example, the same user may appear with two different published passwords.
|
|
Note - As part of the Leaked Credentials add on, the system retrieves the data from the last six months. Data prior to this period is not available. |
|
Column |
Description |
|---|---|
| Observation Date | Shows the date when the system first detected the leaked credentials. |
| User | The full name and email address of the affected user. |
| Job Title/Department | The job title and department associated with the user. |
| Application | The website from which the credentials were leaked. |
| Password | Lists the compromised password. |
| Confidence |
Indicates the severity level and likelihood of misuse.
|
| Source | The origin of the leak (for example, dark web, public repository, breached database). |
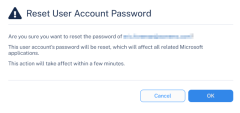
Resetting Passwords for a Compromised User Account
To reset the password for a compromised user account:
-
Go to Leaked Credentials.
-
In the ERM Leaked Credentials table, click the
 icon next to the required security event.
icon next to the required security event. -
Select Reset Password.
-
In the Reset User Account Password pop-up, click OK.
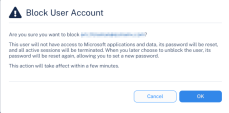
Blocking a Compromised User Account
To block a compromised user account: