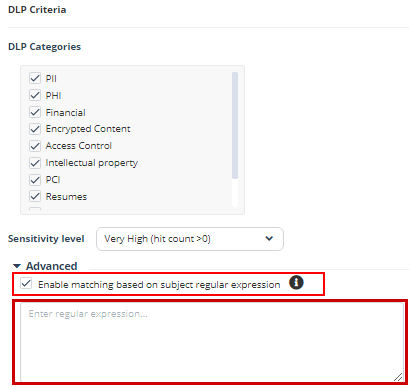
DLP Subject Regular Expression (Regex)
By default, Harmony Email & Collaboration matches emails to DLP policy rules based on the data types detected in them. However, you can use regular expressions to match emails from the email subject.
This type of matching helps you to detect sensitive emails from the email subject and allows you to trigger specific workflow. Therefore, emails with a defined subject pattern will match the DLP policy rule regardless of the data types they include.
To add a regular expression condition to a DLP policy:
-
Go to Policy.
-
To add the regular expression to an existing DLP policy, click the policy and continue from step 6.
-
To create a new DLP policy, click Create New Policy Rule.
-
From the Choose SaaS drop-down, select the desired SaaS application.
-
From the Choose Security drop-down, select DLP and click Next.
-
In the Protection mode section, select Prevent (Inline).
-
Select the Scope of the policy:
-
Select email direction as Outbound.
-
Under Senders, select the Specific Users and Groups the policy applies to.
-
-
In the DLP Criteria section, do these:
-
Enable Check Point DLP Categories toggle button and select the required DLP Categories.
-
Select the required Sensitivity Level. See DLP Policy Sensitivity Level.
-
Enable Subject regular expression toggle button and enter the regular expression. See Subject Regular Expressions Syntax.
-
-
Click Save and Apply.
Subject Regular Expressions Syntax
The Subject Regular Expression field allows you to enter values in the Python Regular Expressions (RE) syntax.
For example, to create a DLP policy rule to find emails that contains the string [secure] in the email subject, add (?i)\[secure] or \[secure] where (?i) is used to specify that it is case insensitive to the Subject Regular Expression field in the policy.
To create a DLP policy rule to find emails that contain either the exact strings [secure] or [encrypt] in the email subject, you can add either \[secure\]|\[encrypt\] or ex \[secure]|\[encrypt] to the Subject Regular Expression field in the policy.
For more information, see Python regular expressions documentation.
The symbols for the start (^) and end ($) of a line are not supported.
To create a DLP policy rule that detects emails containing the exact word sec in the email body (but not words like Security or Seconds), regardless of whether it's at the beginning of a sentence or separated by spaces or tabs, you can use the boundary marker \b. For example, use \bsec\b.
DLP Workflows for Outgoing Emails
Note - The workflows are available only in Prevent (Inline) mode.
|
Workflow |
Description |
||
|---|---|---|---|
|
Email is blocked. User is alerted and allowed to request a restore (admin must approve) |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
||
|
Email is blocked. User is alerted and allowed to request a restore from their manager |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
||
|
Email is blocked. User is alerted and allowed to restore the email |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
||
|
Email is allowed. Header is added to the email |
Any detected email will be delivered to the recipient with additional header that is configured in the policy. |
||
|
Do nothing |
Any detected email will be delivered to the recipient without any changes. |
||
|
Microsoft Encryption Workflows |
|||
|
Email is blocked and user can resend as encrypted by Microsoft |
Any detected email will not be delivered to the recipient and the user can resend the email as Microsoft encrypted email. |
||
|
Email is allowed. Encrypted by Microsoft |
Any detected email will be delivered to the recipient as encrypted by Microsoft and a header will be added to the email. For more information, see Microsoft Encryption for Outgoing Emails. |
||
|
Email is blocked and user can request to resend as encrypted by Microsoft (admin must approve) |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
||
|
Email is blocked and user can resend as encrypted by Email Encryption |
Any detected email will not be delivered to the recipient and the user can resend the email as Check Point Email Encryption email. |
||
|
Email is allowed. Encrypted by Email Encryption |
Any detected email will be vaulted by Check Point Email Encryption and the recipient receives a email notification. For more information, see Encrypting Outgoing Emails. |
||
|
Email is blocked and user can request to resend as encrypted by Email Encryption (admin must approve) |
Any detected email will not be delivered to the recipient and will be moved to quarantine mailbox.
|
||
To create Allow-List for DLP, see DLP Exceptions.
DLP Alerts for Outgoing Emails
You can configure alerts for outgoing emails detected as violating a DLP policy:
-
Send email alert to admins when a DLP policy is violated.
-
Send email alert to specific recipients when DLP is detected. It is possible to customize email template using the gear icon next to the action.
-
Send email alert to the direct manager when an employee sends (or attempts to send) confidential data that violates a DLP policy.

Notes:
-
When this option is enabled, the email alerts are sent to the manager even when the email is blocked.
-
This option is available only for Office 365 DLP policies.
-
-
Send email alert to the direct manager when attachment is encrypted (password protected).

Note - This option available only for Office 365 DLP policies.
-
Send email alert to the sender when DLP Subject Regex pattern and DLP is detected in the email. For details, see DLP Subject Regular Expression (Regex).
-
Send email alert to the sender when DLP Subject Regex pattern is not detected but DLP is detected in the email. For details, see DLP Subject Regular Expression (Regex).
Prerequisites to Avoid Failing SPF Checks
For Office 365 Mail, if you enable Protect (Inline) Outgoing Traffic in the DLP or Threat Detection policy, Harmony Email & Collaboration gets added to the email delivery chain before reaching external recipients (Internal email sender > Microsoft 365 > Harmony Email & Collaboration > Microsoft 365 > External recipient).
The recipient's email security solution sees the Harmony Email & Collaboration IP address as part of the delivery chain. If the recipient's email security solution fails to recognize the original IP address, it may consider the Harmony Email & Collaboration IP address as the IP address from which the email was sent.
If you do not configure the SPF record in your DNS to allow Harmony Email & Collaboration IP addresses to send emails on behalf of your domain, your emails might fail SPF checks and may be quarantined.
Check Point recommends you add the Harmony Email & Collaboration IP addresses to your SPF record before you enable Protect (Inline) Outgoing Traffic for outgoing emails.
To prevent outgoing emails from failing SPF checks and being quarantined, you must add include:spfa.cpmails.com to your SPF record.
|
|
Note - The above statement includes several IP addresses and networks, some outside your Infinity Portal's data region. This is done for uniformity and consistency in all Check Point SPF records regardless of your data region. Harmony Email & Collaboration sends the emails only from one of the IP addresses in your region. |
Outgoing Email Protection - Office 365 Footprint for DLP
Transport rules
Additional transport rule is created when enabling Inline DLP.
-
Rule name: Check Point DLP Outbound
-
Rule:
-
Rule description:

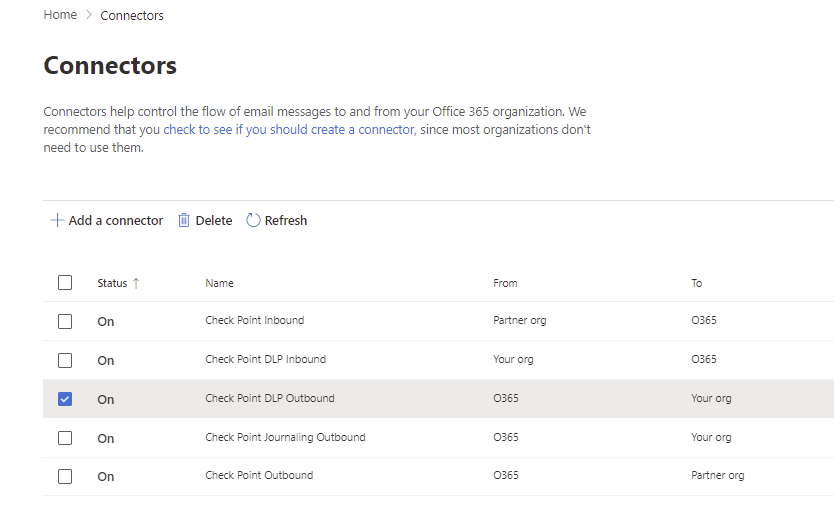
Connectors
Additional connector will be added, Check Point to Office 365.
-
Connector:
DLP Policy Sensitivity Level
The Sensitivity Level for a DLP policy is the minimum number of times all the Data Types in the selected categories need to match (hit count) for the policy to trigger the DLP workflow.
You can select these Sensitivity Level for every policy rule.
-
Very High (hit count > 0)
-
High (hit count > 2)
-
Medium (hit count > 5)
-
Low (hit count > 10)
-
Very Low (hit count > 20)
-
Custom (and enter the minimum hit count (Hit count higher than) required for the policy)
For example, a DLP policy includes only the PII category and you selected the Sensitivity Level as High.
-
If all the Data Types in PII were matched only once - the rule does not trigger the selected DLP workflow.
-
If all the Data Types in PII were matched three times - the rule triggers the selected DLP workflow.