Configure CloudGuard SSO with a Generic / Custom Configuration
You can configure CloudGuard SSO![]() Single Sign-On (SSO) - A session/user authentication process that permits a user to enter one name and password in order to access multiple applications. with each Identity Provider that supports SAML 2.0 using a generic (custom) configuration. In this configuration, you create a custom SAML connection. Each SSO Identity Provider requires specific information for creation and configuration of the new connection. Usually, the required information differs by the Identity Provider.
Single Sign-On (SSO) - A session/user authentication process that permits a user to enter one name and password in order to access multiple applications. with each Identity Provider that supports SAML 2.0 using a generic (custom) configuration. In this configuration, you create a custom SAML connection. Each SSO Identity Provider requires specific information for creation and configuration of the new connection. Usually, the required information differs by the Identity Provider.
To create a generic SAML connection, you need the Identity Provider Metadata URL that is available from your Enterprise customer's SAML instance.
-
Log in to the CloudGuard portal with a super user account.
-
Navigate to the Security & Authentication page in the Settings menu.
-
Select Enabled.
The SSO Configuration window opens.
-
Enter the details for the SSO provider as follows:
-
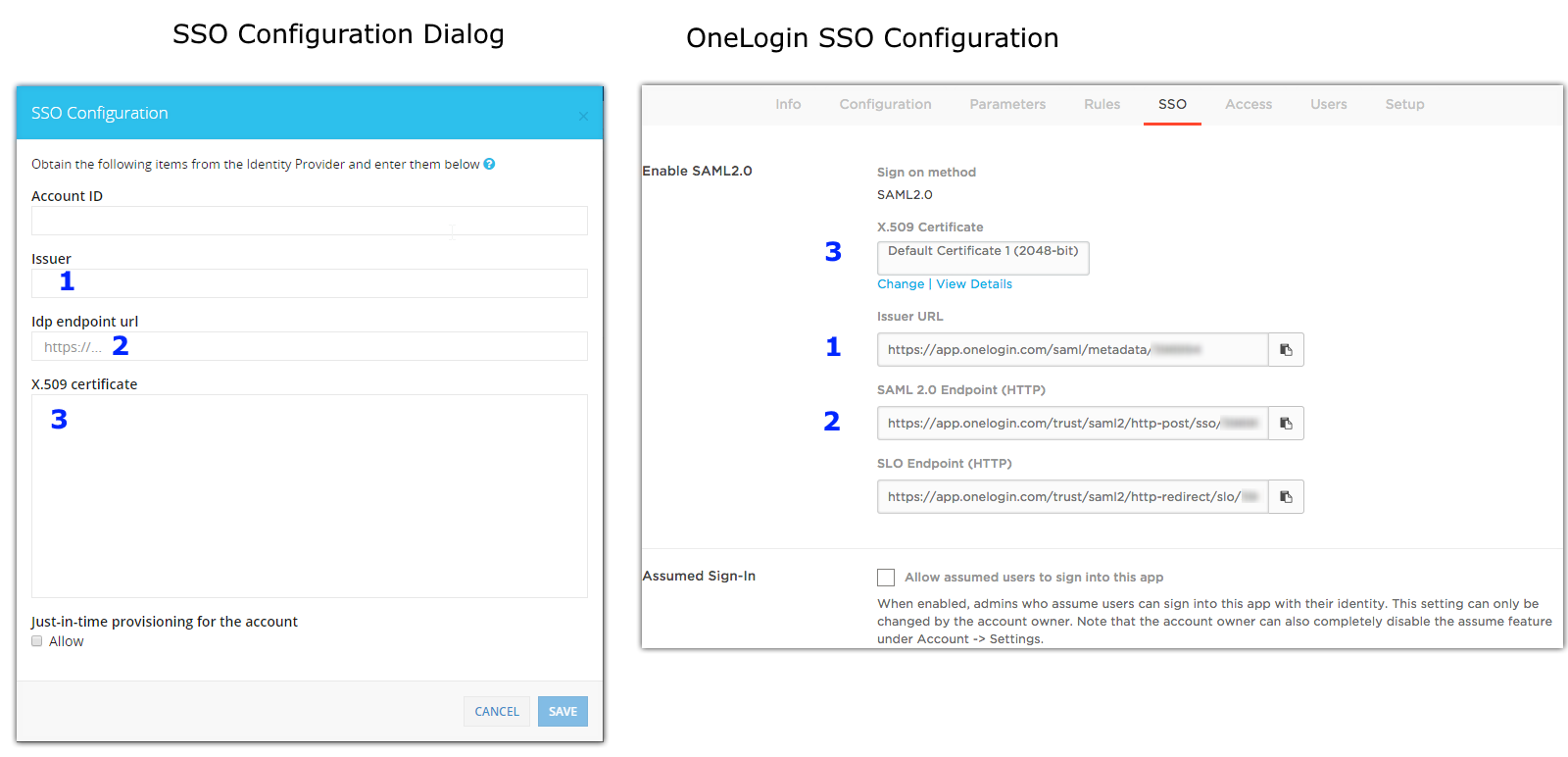
Account ID (For example, for OneLogin, the Account ID is the OneLogin Client ID for CloudGuard)
-
Issuer
-
IDP endpoint URL
-
-
Copy the content of the IDP's X.509 certificate to the X.509 certificate text area in the CloudGuard SSO Configuration window. To view the certificate details in your IDP SSO setting application, click View Details below the certificate context and see the BASE64 representation of the certificate.
-
Click SAVE.
When you use an IDP custom application connector, specify these parameters:
-
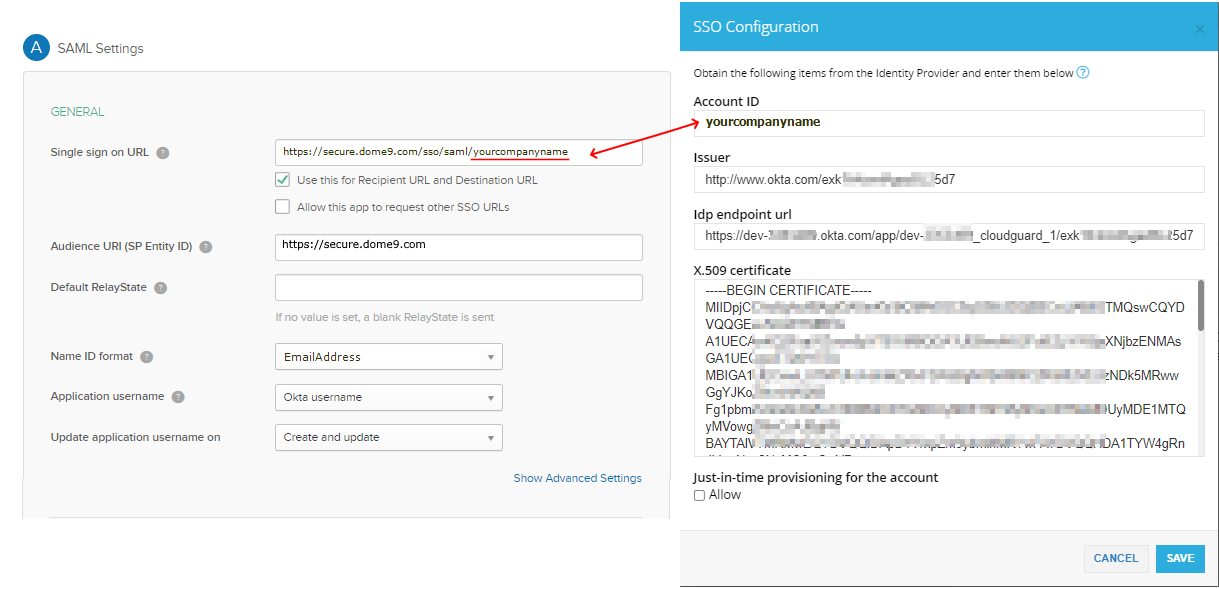
Set the SSO URL / ACS URL to: https://secure.dome9.com/sso/saml/yourcompanyname, where yourcompanyname is the Account ID string used in the CloudGuard SSO configuration.
-
Set the Audience /Entity ID field to: https://secure.dome9.com.
-
Make sure the assertion element is signed but not encrypted. Encryption is handled by the transport layer.
Below is an example of the Okta custom connector.