
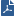

Check Point Blades |
CIM Data Model |
|---|---|
IOS profile, Device |
Alert |
Application Control |
Application Control |
DLP |
Data Loss Prevention |
MTA, Anti-Spam |
|
IPS, WIFI Network, Cellular Network |
Intrusion Attack |
Threat Emulation, Anti-Virus, Anti-Bot, Threat Extraction, Anti-Malware, Anti-Ransomware, Anti-Exploit, Forensics, OS Exploit, Application, Text Message, Network Access, Zero Phishing |
Malware |
Firewall |
Network Traffic |
VPN, Mobile |
Network Session |
URL Filtering |
Web |
When you use Splunk format, Log Exporter replaces these characters:
Original Character |
Exported Characters |
|---|---|
| |
; |
= |
\= |
\n |
Space |