Dynamic Layer
Introduction
R82 introduced a new Dynamic Layer in the Access Control policy to assist customers with highly automated network environments. Dynamic Policy Layers allow managing Access Control layers via API calls to the Security Gateway, without the need to go through Security Management for every change. Layer content (rules and objects) is defined as JSON objects that can be applied directly to the Gateway using GAIA API. To allow tracking changes in dynamic layers, each successful API call generates a list of policy changes along with audit logs on Management / Log Server.
Demo Scenarios
Demonstrate how Dynamic Layer can be used to block an application and IP by deploying an automation script directly to the gateway.. In this example we would block access to Facebook application and also the IP of 8.8.8.8.
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
RDP to windows-client using the desktop shortcut and browse to facebook.com and also ping to 8.8.8.8, verify that both connections are successful. |
||
|
2 |
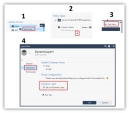
Login to SmartConsole and edit the policy, right click on the policy name under access control and click “Edit Policy”. |
||
|
3 |
Create a new Access Control layer, click the plus sign under Access Control > click New Layer in right corner, name it DynamicLayer1 and checkbox all Blades > select the Advanced menu > checkbox "Set as Dynamic Layer" > click OK |
||
|
4 |
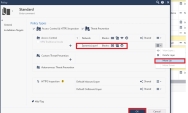
Change the order to layer, so that DynamicLayer1 would be first and click OK.
|
||
|
5 |
Add tracking method- "Log" to the dynamic layer cleanup rule.
then, click install policy. |
||
|
6 |
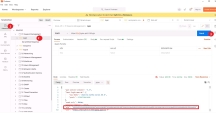
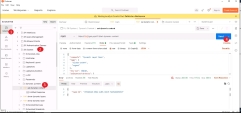
Establish a session to the Gateway, open the desktop Postman application > click Collections on the left menu > Session Management > login > click the send button on the right menu, you should see the SID ID in the response body
|
||
|
7 |
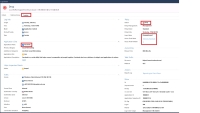
Run The JSON Dynamic Layer script, click System from the collection menu > Dynamic Layer > set dynamic content > click the send button from the right menu You should see a task id the response body, this means that JSON file is valid and the gateway has received the new Dynamic policy correctly |
||
|
8 |
RDP to windows-client again using the desktop shortcut and browse to facebook.com and also ping to 8.8.8.8, the connections should be blocked |
||
|
9 |
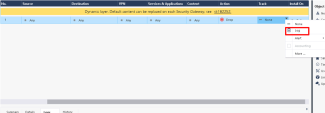
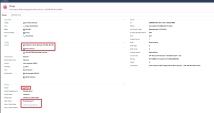
Inspect the gateway's log |
||
|
10 |
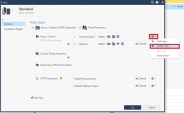
Remove the Dynamic Layer, smart console > right click on policy name > click on Hamburger menu right next to the DynamicLayer1 > click delete > OK and install the policy |
||
|
11 |
Finished |