Advanced HTTPS Inspection features
Introduction
R82 introduces performance improvements and capabilities that enable a better and safer way to deploy HTTPS Inspection, helping organizations to reduce connectivity issues
-
Bypass Under Load - This feature allows connectivity when the Security Gateway is under heavy load (a load resulting from any reason, not necessarily from HTTPS Inspection). The Security Gateway bypasses HTTPS connection until it is stable again. During the HTTPS Inspection bypass, the Security Gateway does not inspect the HTTPS traffic payload. When the Security Gateway is stable again, HTTPS Inspection resumes automatically. This feature is disabled by default.
-
HTTPS Inspection Learning Mode - You can configure partial deployment of HTTPS Inspection to estimate its effect on connectivity and performance issues. With Learning Mode, the Security Gateway inspects a small percentage of the traffic to identify connectivity issues and estimate the expected resource consumption for the configured HTTPS Inspection policy.
-
Client side Fail-Open - The Security Gateway does not perform HTTPS Inspection on connections that failed on the client side (HTTPS Inspection is bypassed).
-
HTTPS Inspection Monitoring - Introducing the HTTPS Inspection statistics view in SmartView, including bypass/inspect statistics..
Demo Scenarios
Goal
Demonstrate how HTTPS "Bypass Under Load" can reduce TLS connectivity related issues due to Gateway's high CPU/Memory utilization
Instructions
|
Step |
Instructions |
||
|---|---|---|---|
|
1. |
From the Jumpserver, open RDP to windows-client |
||
|
2 |
Open google chrome and browse to "Facebook.com" > click the site settings button in the left corner of the address bar > "connection is secure" > click "connection is valid" and view the certificate menu |
||
|
3 |
Review the certificate issuer, it should be "secureyournetwork", which is the gateway's certificate |
||
|
4 |
From the left menu, click Gateway's and Servers > double click the Gateway object |
||
|
5 |
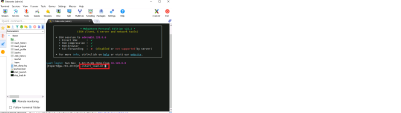
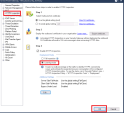
Enable HTTPS Bypass Under Load, go to HTTPS Inspection from the left menu > click the edit under "Advanced Settings" > select Enable in Bypass under load > click on OK twice
|
||
|
6 |
Install Policy |
||
|
7 |
Artificiality force high Gateway's CPU/Memory utilization, go to JumpServer > click the Gateway Desktop SSH shortcut > start the load script "./start_load.sh" |
||
|
8 |
Go back to the Smart Console > Gateway's and Servers > select the gateway object > review the high CPU/Memory utilization |
||
|
9 |
RDP again to windows-client and browse to facebook.com again to review the certificate issuer, it should be the original non-gateway's certificate, meaning that HTTPS Bypass Under Load works properly
|
||
|
10 |
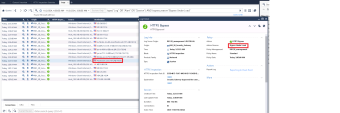
You can also see the HTTPS Bypass Under Load in logs > In smart console, click the logs menu and add new view > click the "HTTPS Inspection Statistics" > double click the Bypass Under Load section and search for facebook.com |
||
|
11 |
Stop the CPU utilization script, go back the SSH terminal and input "stop script.sh" |
||
|
12 |
Finished |
Goal
Demonstrate Learning Mode and examine the anticipated effects of a complete rollout on connectivity and performance.
Instructions
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
Double click the gateway from the Gateways and Servers menu |
||
|
2 |
Click on HTTPS inspection from the left menu and select learning mode option. |
||
|
3 |
Install Policy |
||
|
4 |
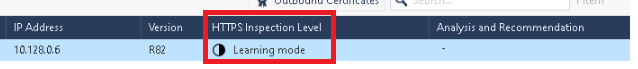
At this point the Learning Mode is configured, you can view the HTTPS Inspection status in
|
||
|
5 |
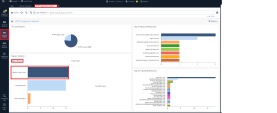
Viewing HTTPS Inspection Statistics, In SmartConsole, click the Logs and Events menu and add a new view> click the "HTTPS Inspection Statistics" view and inspect the HTTPS logs, for example sessions that were bypassed due to invalid client/server side certificates. Using this view, organizations would be able to easily address HTTPS issues before deploying a full inspection.
|
||
|
6 |
Finished |