Zero Phishing
Introduction
Zero Phishing is a new technology and a Threat Prevention protection introduced in R81.20.
Zero Phishing prevents unknown zero-day and known phishing attacks on websites in real-time, by utilizing industry leading Machine-Learning algorithms and patented inspection technologies.
Phishing attacks continue to play a dominant role in the digital threat landscape, which is becoming more mature and sophisticated. Most cyber-attacks start with a phishing attempt.
The Check Point Zero Phishing protection scans the web traffic on the Security Gateway and sends it to the Check Point Cloud for scanning. This way, the Zero Phishing protection prevents access to the most sophisticated phishing websites, both known and completely unknown (zero-day phishing websites).
Because the protection is initiated on the network Security Gateway, the protection is browser-agnostic and platform-agnostic and it does not depend on an email security solution.
Protections usually provided by endpoint or email solutions are now available through the Security Gateway, with no need to install and maintain clients on any device.
The Zero Phishing protection uses two main engines:
-
Real-time phishing prevention based on URLs
The engine prevents both known and unknown zero-day phishing attacks, by analyzing various features on the URL in real-time. The engine sends the URL information to the URL-reputation cloud service to perform the analysis. For example: brand similarity, non-ASCII characters and time of registration.
Using Machine-Learning, the risk is calculated and URLs are classified as phishing and blocked.
-
In-browser Zero Phishing
The Security Gateway performs patented Java Script injection to scan HTML forms when they are loaded on the browser (including dynamic forms).
When the end-user clicks the input fields in the form, all HTML components are scanned in real-time, and the information is sent to the Check Point Zero Phishing cloud service for AI-based analysis.
The risk is calculated and the phishing site is blocked accordingly.
Discussion Points
-
The enhanced solution is available through the Security Gateway network flow, introducing dynamic security components that run within the browser with no need to install any client.
-
Delivered as part of your existing SandBlast (SNBT) license.
-
Works out of the box for Security Gateways with Autonomous Threat Prevention enabled.
Goal
Demonstrate the capability of Zero Phishing protection.
Instructions
|
|
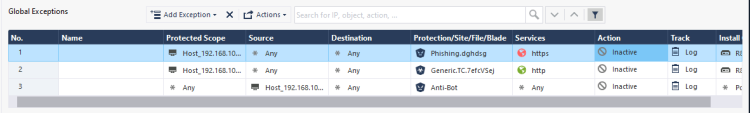
Important - Zero Phishing sites on this demo are not really a phishing sites and it exists for demo purposes only. For that reason other products like Anti-Virus & Anti-Bot may block it as well. In order to demonstrate Zero Phishing capabilities , you may need to add an exception for these blades under global exceptions: Security Policies > Threat Prevention > Exceptions > Global Exceptions. Example: |
|
Step |
Instructions |
|---|---|
|
1 |
From the Jump-Server VM , Open RDP connect to "Windows-Client" VM - Click on the Remote Desktop Shortcut "Windows-Client" with the saved credentials of user : demolab-ad\bruce: |
|
2 |
Open Chrome Browser on the Windows-Client VM. |
|
3 |
Click on the saved bookmark : Zero Phishing Site1: |
|
4 |
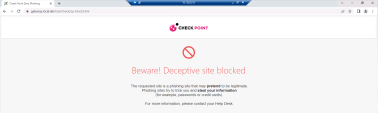
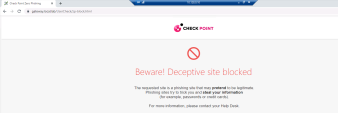
You will receive the following block page : |
|
5 |
In SmartConsole, in the "LOGS & MONITOR" view, the following log should appear: |
|
Step |
Instructions |
|---|---|
|
1 |
From the Jump-Server VM , Open RDP connect to "Windows-Client" VM - Click on the Remote Desktop Shortcut "Windows-Client" with the saved credentials of user : demolab-ad\bruce: |
|
2 |
Open Chrome Browser on the Windows-Client VM. |
|
3 |
Click on the saved bookmark : Zero Phishing Site2: |
|
4 |
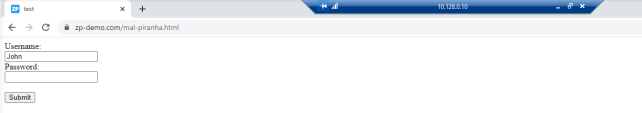
You will receive the following page : |
|
5 |
Start typing in the Password textbox , you should be redirected to the block page : |
|
6 |
In SmartConsole, in the "LOGS & MONITOR" view, the following log should appear: |
Check Point’s products provide better cyber security. Now you have a tool to help you demonstrate just that! - Total Cyber Protection.
You can use this tool to get insights and demos using actual phishing URLs found in the wild.
Total Cyber Protection tool presents empirical results to contribute to a cyber-security capabilities discussion, in addition to existing tools for performance, costs and features sets discussions with potential customers.
You are able to easily see and share with your potential customers, examples of recent relevant threats, detected by Check Point security products, compared to other security products. This illustrates Check Point’s Best in Security approach.
Tool is available for Check Point SE's & Partners and can be access from PartnerMap:
Direct link: https://totalprotection.checkpoint.com/
User Guide for Total Cyber Protection is available in CheckMates - Link
|
|
Important -
|
|
|
Note - The R81.20 Security Gateway is preconfigured to generate logs for scanned non-phishing sites using the following command :
|
|
Step |
Instructions |
|---|---|
|
1 |
From the Jump-Server VM , Open RDP connect to "Windows-Client" VM - Click on the Remote Desktop Shortcut "Windows-Client" with the saved credentials of user : demolab-ad\bruce: |
|
2 |
Open Chrome Browser on the Windows-Client VM. |
|
3 |
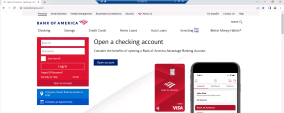
Click on the of the saved bookmark : Bank of America or Paypal to browse to a non-phishing site page that includes a textbox for adding user credentials: |
|
4 |
Start typing in the User Name / Password textbox to verify by Zero Phishing : |
|
5 |
In SmartConsole, in the "LOGS & MONITOR" view, the following Accept logs should appear: |