Threat Extraction
Practical and proactive prevention with Threat Extraction
Goal
-
Demonstrate practical prevention with a range of capabilities using the SandBlast Threat Extraction and Threat Emulation modules.
Discussion points
-
Check Point SandBlast Threat Extraction - a proactive solution to security using the CDR (Content Disarm and Reconstruction) technology
-
Delivering safe and sanitized files to users in seconds, supporting continuity of business. Users receive risk-free files - a big advantage for many parts of the organization with self-catered ability to receive original benign files.
-
The advantages in our threat emulation solution inspecting the file while Threat Extraction delivers safe copies of files to the users
-
Practical prevention, consolidated solution, reduced overheads to IT
Instructions
The procedure below describes all steps to demonstrate the scenario.
|
Step |
Instructions |
||||||||
|---|---|---|---|---|---|---|---|---|---|
|
1 |
From the Windows-Attacker VM, Change the MD5SUM of the file on the 'dropbox' server : John_Smith_White_Paper.docx by Execute the GW First Step - Varient me shortcut:
|
||||||||
|
2 |
From Jump server, Click on the RDP shortcut Windows-Client to Connect to the Windows-Client machine with the saved credentials of user : demolab-ad\bruce
|
||||||||
|
3 |
On the Windows-Client VM, open Chrome bookmark John Smith Dropbox: |
||||||||
|
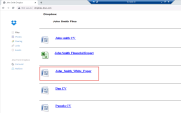
4 |
Click on the John_Smith_White_Paper.docx link to download the document: |
||||||||
|
5 |
The file will be downloaded & cleaned (Active Content was extracted from file) |
||||||||
|
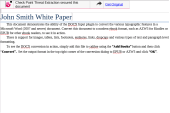
6 |
Try to open the file (John_Smith_White_Paper.cleaned.docx) and notice that the file includes a header with a self-catered link to receive the original file by him /herself (self-catered service). |
||||||||
|
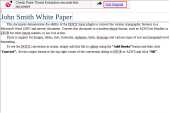
7 |
Click the link in the header - Get Original, |
||||||||
|
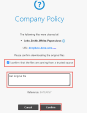
8 |
It will open a user check portal: Approve by checking the checkbox and add a short justification. (Justification is an optional field that doesn’t have to appear in the user check, but will appear in the log if it exists.) |
||||||||
|
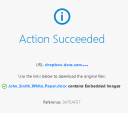
9 |
Notice that the downloaded file is scanned by Threat Emulation and found benign : |
||||||||
|
10 |
Navigate back to the Jump server , Open R81.20 SmartConsole, navigate to the LOGS & MONITOR tab.
|
||||||||
|
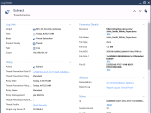
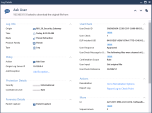
11 |
Demonstrate the administrator experience by reviewing the event logs of what has happened. Focus on the Threat Extraction and showing the user request to receive the original file. |