Threat Emulation
Goal
Demonstrate that traditional signature based solutions are no longer sufficient to prevent today’s sophisticated attacks.
We need a more advanced threat prevention solution - SandBlast.
Discussion points
-
It is a fact that more than 50% of attacks evade traditional security solutions and show how easy it is to create an unknown variant and evade detection with a simple password-protected archive.
-
Don’t focus on the methods used. Focus on the principle and idea of evading detection.
Instructions
The procedure below describes all steps to demonstrate the scenario.
|
Step |
Instructions |
|---|---|
|
1 |
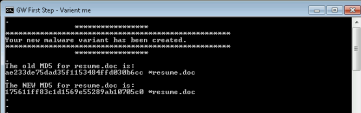
Connect to the Windows-Attacker VM and execute the GW First Step - Varient me shortcut (we are going to change the MD5 of a malicious file, so the file will be uploaded for emulation). |
|
2 |
Type the file name: resume.doc and Click Enter. |
|
3 |
Enter a few random characters and Click Enter. |
|
|
You will see the old MD5 and the new MD5 |
|
4 |
On the Windows-Attacker machine browse to Virustotal using Chrome. (Once Chrome is open use the bookmark in the bookmark bar.) |
|
5 |
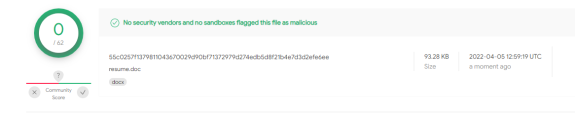
Upload the resume.doc file with the new MD5 from directory C:\inetpub\wwwroot\resume.doc. The file acts as our unknown malware, and we will use Virustotal to test it. This scenario demonstrates and emphasizes how easily an attacker can bypass traditional and signature-based solutions with minimal sophistication |
Additional information
We have seen that it is very easy to create a variant of known malware and turn it into unknown.
It can even be a simple change to the file’s MD5 hash.
|
|
Important - The malware resume.doc that we are using is a password protected archive with a real malicious document inside. The .zip file extension was manually changed to .doc. This technique is used to bypass traditional detections by manipulating the file extension |
While Traditional signature based solutions such as AV can help with known malware, they cannot adequately protect against modern attacks and unknown malware.
We see that there is no detection for our new malware variant, and we are ready to test it with SandBlast Threat Emulation.
We will see how Threat Emulation will detect the true file type and be able to open the password-protected archive and scan the file.
We are only using these simple techniques to prove the point where not all content can be inspected in the network level.
Goal
-
Demonstrate prevention with a range of capabilities using the SandBlast Threat Emulation module.
Previously created unknown malware and a potentially unsafe document will be used for the demonstration.
Discussion points
-
Check Point SandBlast Threat Emulation technologies and solution.
-
Leveraging existing Infrastructure (GWs), adding SandBlast licensing, and using Check Point Cloud for Sandboxing.
-
The advantages of our threat emulation solution such as: CPU Level emulation, OS-level inspection, advanced anti-evasion techniques, prevention of multistage attacks, ‘push forward’ for Flash and CADET that automatically train machine learning algorithms using an AI with all the data analyzed by Threat Cloud.
-
Check Point’s simple and easy way to deploy SandBlast by using our learning mode to best practice deployment instructions.
Instructions
The procedure below describes all steps to demonstrate the scenario.
|
Step |
Instructions |
||||||||
|---|---|---|---|---|---|---|---|---|---|
|
1 |
From the Windows-Attacker VM, Change the MD5SUM of the file on the 'dropbox' server : resume.doc by Execute the GW First Step - Varient me shortcut:
|
||||||||
|
2 |
From Jump server, Click on the RDP shortcut Windows-Client to Connect to the Windows-Client machine with the saved credentials of user : demolab-ad\bruce
|
||||||||
|
3 |
On the Windows-Client VM, open Chrome bookmark John Smith Dropbox: |
||||||||
|
4 |
Click on the Dan CV link to download the document: |
||||||||
|
5 |
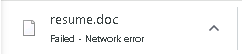
The downloads will fail :
|
||||||||
|
6 |
Navigate back to the Jump server , Open R81.20 SmartConsole, navigate to the LOGS & MONITOR tab.
|
||||||||
|
7 |
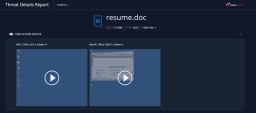
Open (double click on) the log and review the log details. Pay attention to the file type field. If the Summary report doesn’t appear, close the log, press refresh logs, and open it again. |
||||||||
|
8 |
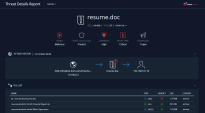
You can see that there are three files in the archive. Only one is malicious with the name resume.doc (the actual malicious document). By clicking on the resume.doc file you can view the emulation report for it. With archives you will be able to see all the files in the archive and their verdicts. You will also have an emulation report for the malicious verdict. Show the emulation report details and the video of the emulation. |