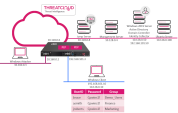
Identity Awareness
The R81.20 Security Gateway is running instance called “PDP” learning identities and logon events from the Identity Collector. The Identity Collector is the instance running on the Windows admin client learning the identities from the Active Directory Domain Controller (Windows Server 2019 Standard) . The Domain Controller sends Logon Event notifications to the Identity Collector. The Identity Collector will send this event to the PDP instance, which then sends an LDAP Group Membership query to the Domain Controller. Once the group membership is known to the PDP it calculates which Access Role object is matching and sends this information to the PEP instances on the R81.20 Security Gateway. The PEP instances will then be able to enforce the security policy on the traffic passing the gateway.
Whenever a user logs on to a computer the Domain Controller issues a Login Event notification to the Identity Collector. This notification includes the UserID, the name of the machine and the IP address.
The communication between the Domain Controller and the Identity Collector is based on the Microsoft API using an HTTPS connection.
The Identity Collector forwards the information learned from the Login Event to the PDP instance.
The PDP instance issues an LDAP group membership query to the Domain Controller learning the group membership of the user who just logged in.
Once the group membership is learned the PDP starts calculating which Access Role object will match the information learned.
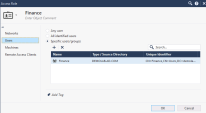
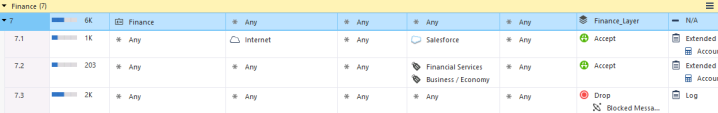
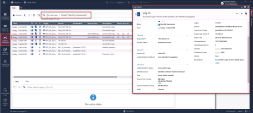
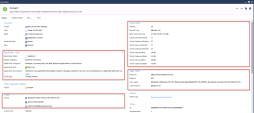
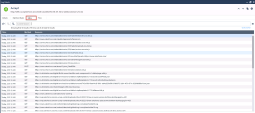
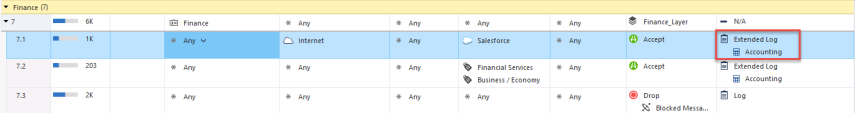
In the below screenshot you see the Access Role object matching all users that belong to the Finance group defined in the Active Directory.
In case an Access Role object is matching the PDP instance will share this information with the PEP instance.
The PEP instance running on the gateway performs the enforcement blocking or allowing relevant traffic base on the security policy defined.
Instructions
|
Step |
Instructions |
|---|---|
|
1 |
From Jump-Server VM Desktop , Open MobaXterm application |
|
2 |
Double Click on the saved session : Windows Client (Local administrator) |
|
3 |
Sign out all the logged users : |
|
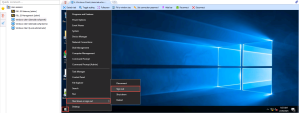
4 |
Right Click on the Windows button > Shut down or sign out > Sign out : |
Background Story
Anna Smit (asmith) is manager on the finance department.
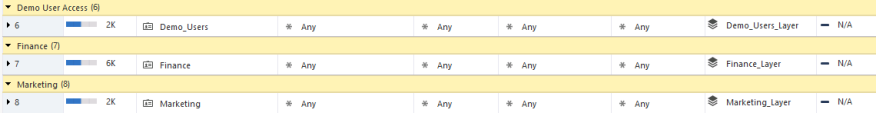
According to the company policy, finance department can only access finance applications & services.
Instructions
|
Step |
Instructions |
|||
|---|---|---|---|---|
|
1 |
From Jump-Server VM Desktop , Open MobaXterm application |
|||
|
2 |
Double Click on the saved session : Windows Client (demolab-ad\asmith) to login in with Anna Smith :
|
|||
|
3 |
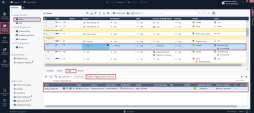
Once the Remote Desktop connection is established , Open SmartConsole from the Jump-Server VM and navigate to Logs & Monitoring tab to verify the “Log In” log message. |
|||
|
4 |
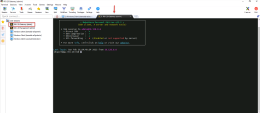
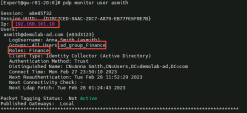
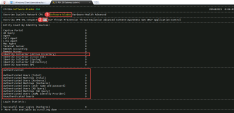
Verify the identity has been learned by the PDP : |
|||
|
5 |
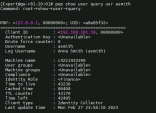
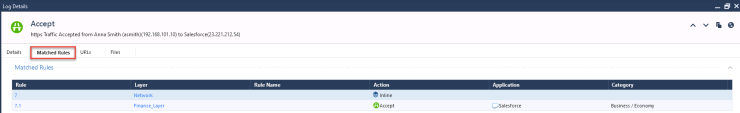
Verify the identity has been shared with PEP : Run this command on the internal gateway to see if the PEP has all information to perform security on the traffic :
|
|||
|
6 |
Run cpview command on R81.20 Security Gateway and explore the options for Identity Awareness : Software-blades > IDA Example output : |
|||
|
7 |
User “Anna Smith” is accessing applications :
|
|||
|
8 |
Open a new Chrome browser tab and try to access YouTube (saved bookmark) : |
|||
|
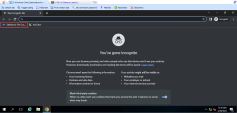
9 |
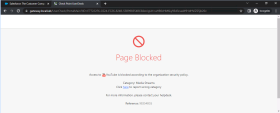
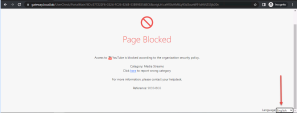
You will see that access to this application is blocked by policy:
|
|||
|
10 |
You can repeat the above steps with the user : Joe Roberts from Marketing Department using the saved RDP session on Mobaxterm :
Marketing department can only access the following application: Facebook & YouTube.
|