Firmware Risk Assessment
Whether you develop IoT devices or deploy them in your organization, with Check Point's Quantum IoT Protect - Firmware Risk Assessment, you can reduce your exposure to IoT risk in advance.
As devices increasingly connect to the cloud and internet over 5G networks, network-level security may not even be available as a first line of defense, making firmware security even more imperative as a powerful line of defense for your embedded device.
And when it comes to IoT firmware, the risks are many—from 3rd party supply-chain components, through outdated firmware, to device misconfigurations and state-sponsored backdoors. To remove uncertainty, you need to know the underlying firmware security posture of your IoT product offering, and you need to know it now.
By the end of the assessment, you will receive a comprehensive report that includes insights on:
-
Discovered vulnerabilities (CVEs databases)
-
Known/weak Credentials
-
Operating system misconfigurations
-
Insecure private keys and certificates
-
Suspicious domains
-
Key recommendations to mitigate security flaws
You can review the Firmware Risk Assessment on the demo tenant :
-
Click on the IOT tab > Firmware Scan:
-
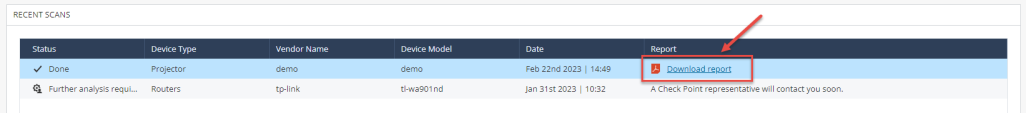
Download the report to get a preview of the scope of information you will receive :
Additional information