2. Phishing protection and credential reuse
Goal
-
Demonstration of Harmony Browse real time phishing prevention capabilities and credential reuse protection.
Discussion points
-
Harmony Browse zero-phishing real time scanning and prevention capabilities protecting organizations from the most common attack vector.
-
Harmony Browse credential reuse protection, alerting from potential corporate credential theft.
Instructions
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
From the Jump-Server machine, on the desktop, use the remote desktop link to connect to the Windows-Attacker machine. |
||
|
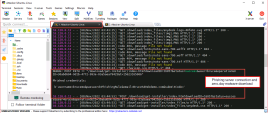
2 |
On the Windows-Attacker machine , run the following :
|
||
|
3 |
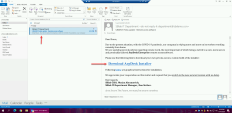
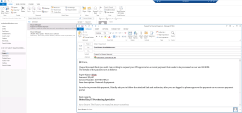
On the Windows-Attacker machine , Open the Outlook client from the taskbar and send the targeted credential theft email named “URGENT: Policy update – Remote access software” for Bruce Morgan the CFO The email is at the drafts folder of the SBlab IT Department section. |
||
|
4 |
Minimize the remote desktop window and open a connection to the Windows10-Protected machine, use the remote desktop link from the desktop to connect. |
||
|
5 |
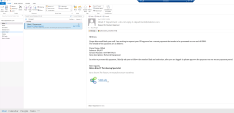
On the Windows10-Protected machine , Open the outlook client from the taskbar and review the targeted email…… looks legitimate, right?.
|
||
|
6 |
Click the download AnyDesk Installer link, and it will open in the chrome browser. |
||
|
7 |
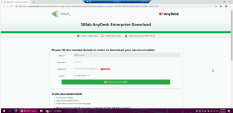
Notice that Bruce’s details are already filled in to build trust with the user, and all that is left for him is to fill in his (Bruce’s) password. |
||
|
8 |
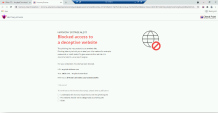
Press the password textbox to fill in any password you would like and notice that zero-phishing scans and detects the site as a phishing site preventing the user from exposing their credentials to the attacker. |
||
|
9 |
Don’t close the user notification tab, and move back to the previous tab to show that the user is now blocked from handing his credentials to the attacker. |
||
|
10 |
We have added in the policy the ability for the user to proceed even after phishing prevention is done in order to progress the scenario and show what happens in case zero-phishing is not implemented. |
||
|
11 |
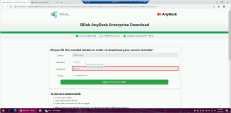
Go back to the user notification tab and press the “visit this infected site” link. |
||
|
12 |
Now you will be able to fill in any password you want and click download your installer. Suggestion: use a funny password like “I@mComporm!zed” or “PhishingRulz” |
||
|
13 |
Show that the installer is blocked by the web download protection. |
||
|
14 |
Navigate back to the Windows-Attacker machine to demonstrate that Bruce’s password was successfully stolen and can be used to launch a large scale attack on that organization.
|
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
From the Jump-Server machine use the remote desktop link to connect to the Windows-Server-Protected machine. |
||
|
2 |
You can explore Total Cyber Protection tool of Check Point and share with your potential customers, examples of recent relevant threats, detected by Check Point security products, compared to other security products. You can use this tool to get insights and demos using actual phishing URLs found in the wild. Tool is available on PartnerMap: |
||
|
3 |
You can also try and browse to OpenPhish URL using the Chrome bookmark https://openphish.com.
|
||
|
4 |
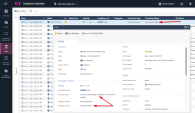
You can review logs and events from the Harmony Browse Management portal. |
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
From the Jump-Server machine use the remote desktop link to connect to the Windows-Server-Protected machine. |
||
|
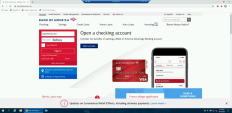
2 |
Open the chrome browser and browser to a safe site with username and password fields We recommend using Bank of America : https://www.bankofamerica.com/ site or similar site that has both fields visible.
|
||
|
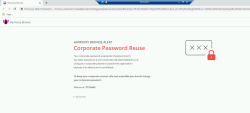
3 |
You will see a notification that alerts the users that their corporate password might be exposed to hackers and that they need to change it immediately. It will also create a log in the Harmony Browse management portal for administrators. |
|
Step |
Instructions |
|
|---|---|---|
|
1 |
From the Jump server machine, on the desktop, use the remote desktop link to connect to the windows attacker machine. |
|
|
2 |
Open the Outlook client from the taskbar and send the targeted phishing email “Request for Payment Approval” for Bruce Morgan the CFO. The email is at the drafts folder of the SBlab IT Department section. |
|
|
3 |
Minimize the window and open a connection to the Windows 10 Protected machine, use the remote desktop link from the desktop to connect. |
|
|
4 |
Open the outlook client from the taskbar and review the targeted email…… looks legitimate, right?. This is how easy it is to perform a social engineering and credential theft attack, and this scenario demonstrates why it is so successful and the critical need for real-time phishing prevention. |
|
|
5 |
Click and open html attachment - it will open in the chrome browser. |
|
|
6 |
Notice that the opened local HTML page looks like valid authentication portal and Bruce’s details are already filled in to build trust with the user, and all that is left for him is to fill in his (Bruce’s) password. |
|
|
7 |
Press the password textbox to fill in any password you would like and notice that zero-phishing scans and detects the local HTML page site as a phishing site preventing the user from exposing their credentials to the attacker. |
|
|
8 |
Don’t close the user notification tab, and move back to the previous tab to show that the user is now blocked from handing his credentials to the attacker. |
|
|
9 |
Navigate back to the Jump server and login to the Infinity portal through the chrome browser (Environment Information). |
|
|
10 |
Verify you choose chkp-demodays.xyz account and Harmony Browse application. |
|
|
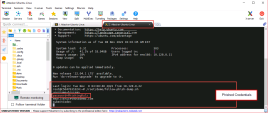
11 |
Navigate to the LOGS tab and run the following search to show detection log for ZeroPhishing:
|