1. Web download protection scenarios
Goals
-
Demonstrate Harmony Browse solution, web download protection with SandBlast Threat Emulation and Threat Extraction technologies.
-
Demonstrate having the same level of protection when outside the organizational network.
Discussion points
-
Threat Emulation and Threat Extraction technologies as the core technologies through all Harmony Solutions.
-
Having the same level of protection for users that leave the network protection and work remotely.
-
Practical prevention where users receive a safe and sanitized copy of files in seconds while original file is emulated. Original files are self-catered by the users if they are not malicious.
|
|
Important - Before you start, make sure that the Harmony Browse browser extension is installed. |
Instructions
Locally hosted web server to demonstrate user experience with benign files and known malicious files.
|
Step |
Instructions |
||||||||
|---|---|---|---|---|---|---|---|---|---|
|
1 |
From the Jump server machine use the remote desktop link to connect to the Windows-Server-Protected machine. |
||||||||
|
2 |
Open the chrome browser and browse to John Smith Dropbox using the bookmark http://www.dropbox-docs.com/, The following files will be demonstrate:
|
||||||||
|
3 |
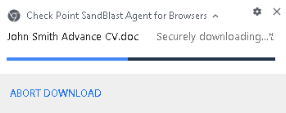
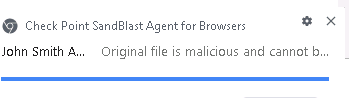
Click on the first file “John smith CV” to download it The file is sent to the cloud for emulation and extraction. If the file is known as malicious by ThreatCloud and TE it will be blocked. In cases where the file is not known it will be extracted and the access to the original file will be blocked after emulation is finished since the file is malicious. You can view the notifications from the browser extension: |
||||||||
|
4 |
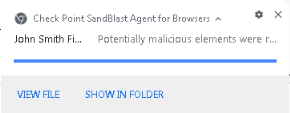
The following 2 files are benign files that will demonstrate Threat Extraction ability to proactively clean a file and provide a user with a safe copy of the file in seconds. We will demonstrate 2 scenarios:
|
||||||||
|
5 |
The policy is set to clean, which means that the file will be cleaned and reconstructed using the same file format (the user will receive a safe copy in excel format) Download the “John Smith finance report”. |
||||||||
|
6 |
Open the downloaded file and click the “view chart” button to show that the macro is not working. |
||||||||
|
7 |
The policy is set to convert documents, which means that the file will be converted to a flat pdf without any active content. Download the “John Smith white paper”. |
||||||||
|
8 |
Press the browser extension icon (in the upper right corner of the extension bar) and download the original files to show that the cleaned files content are the same, but without the active content.
|