Threat Intelligence
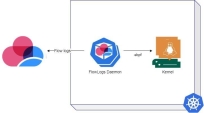
CloudGuard Threat Intelligence for Kubernetes allows you to visualize and analyze clusters for East- West and North-South network activity, regardless of the cluster's location, on-premises or cloud.
Threat Intelligence analyzes network flow logs generated by the CloudGuard Agents to visualize your cluster's activity and uses queries to show you traffic of interest.
Threat Intelligence combines cloud inventory and configuration information with real-time monitoring data.
The result is an enhanced visualization that highlights suspicious traffic from legitimate traffic.
Threat Intelligence can give you close to real-time views of network activity. You can also view and analyze past network activity.
You can configure Threat Intelligence to send you real-time alerts for specific events or event types that occur in your cloud environment so that you will be aware and able to respond immediately.
Architecture
Instructions
|
Step |
Instructions |
||||||||
|---|---|---|---|---|---|---|---|---|---|
|
1 |
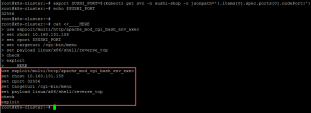
Install web server on the Kubernetes Server : Copy
|
||||||||
|
2 |
Copy & Paste the following commands on the Kubernetes Server : Copy
|
||||||||
|
3 |
Save the script output , We will use it on the next steps : |
||||||||
|
4 |
From the CloudGuard Portal , Navigate to CDR> Threat Monitoring > Policies , Make sure that the Kubernetes CloudGuard Best Practices ruleset is attached to your cluster. |
||||||||
|
5 |
Connect to the Attacker VM via SSH Client, You can either connect to it from the Windows-Console VM (Putty Client) or Click on the VM on the Environment Viewer page.
|
||||||||
|
6 |
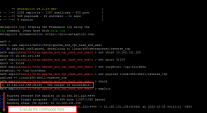
Start the attack on your website by launching Metasploit with the following command: Copy
|
||||||||
|
7
|
Paste the output saved on step 3 :
Execute the following commands that will run in the context of the webserver :
|
||||||||
|
8 |
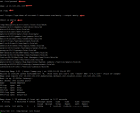
Use Ctrl+C to exit the remote shell and choose yes when prompt. |
||||||||
|
9 |
Execute the command 'exit' to exit Metasploit. |
||||||||
|
10 |
From the CloudGuard Portal: Navigate to the Events > Threat & Security Events and review the generated events : |