3. Posture Management & Compliance
At the heart of Cloud Security Posture Management is the detection of cloud misconfigurations and vulnerabilities that can lead to compliance violations and data breaches.
The only way to do this at cloud scale and speed is to automate in order to achieve “continuous compliance” for multiple public cloud environments.
Automation should extend beyond detection to auto-remediation as well.
Customers need broad out of the box set of industry standards and compliance checks.
They also need the ability to customize and create their own baselines and set of rules.
Use the Compliance tool to ensure you are meeting various compliance standards and create custom policies for unique governance needs.
What you see here are the default rulesets built into the platform.
Experts have mapped out the rules in each of these rulesets to the relevant sections in the compliance standard.
We not only have a huge number of industry compliance rulesets, we also have built in Best Practice rulesets.
This is important for customers who don’t necessarily have to follow an industry compliance framework but want to follow Cloud Best Practice Policies to keep their environment’s secure.
Instructions
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
Under CSPM tab , Navigate to Rulesets. |
||
|
2 |
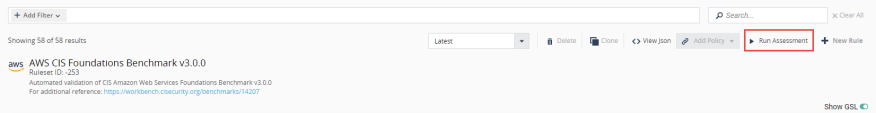
Search for "AWS CIS Foundations" (use the more recent version). |
||
|
3 |
Click Run Assessment. |
||
|
4 |
Click on Select All and Click Run.
|
||
|
5 |
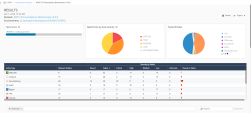
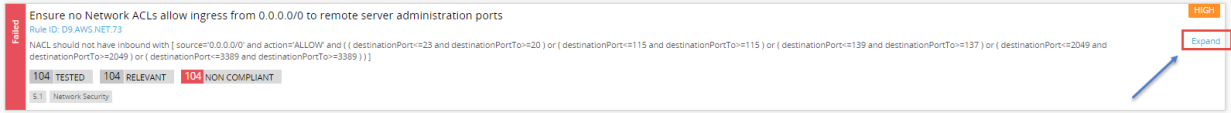
Review the results.
|
||
|
6 |
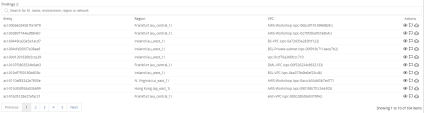
Press on Expand on a rule to review the description of the rule (why it is important for security) and specific remediation steps that need to taken in order to pass the rule in the future. And most importantly – a list of the specific assets which have failed this rule. Meaning if I run the remediation steps on all the assets listed here, next time this rule is run, it will pass. |
||
|
7 |
There are a few actions that can be taken in regards to these findings.
CloudBots Video
|
||
|
8 |
Click on the Export button on top right corner. All of these reports can be exported and scheduled. You can create many alert settings for these compliance rulesets. Notifications can be through the console, by email, or integrated with many leading SIEM products and ticketing systems. To ensure continuous compliance, you can be notified any time something new in your environment fails a rule. |
Watch Video for How to Run a Compliance Assessment on Azure
in addition to the rulesets that CloudGuard Cloud Security Posture Management (CSPM) manages for you, we allow you to create your own custom policies and rules using the GSL Builder. This allows you to easily create rules to test in your environment, without needing to learn APIs or SDKs for each and every service. Custom rules can be built for AWS, Azure, GCP, Kubernetes clusters and Terraform templates.
Instructions
|
Step |
Instructions |
|---|---|
|
1 |
Under CSPM tab , Navigate to GSL Builder. |
|
2 |
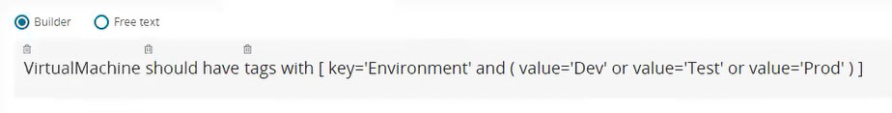
Let’s say, for example, my organization has a specific tagging policy they want to enforce in their Azure environment. Change tab to Microsoft Azure at top and make sure you are on Builder. |
|
3 |
You can start building out the rule just by clicking on an object in the rule builder and it will show me the next actions you can take. Build out rule so it looks exactly like below (Do not forget the parenthesis around the Values!). This rule can be run run against any accounts connected to CloudGuard CSPM for that cloud platform. These rules function exactly like the rules we saw in the managed rulesets where you can test your assets and receive the same kind of reporting. |
For additional examples of various cloud vendors , please use the following rules:
|
Cloud Platform |
Example Rule |
Link to GSL Knowledge base |
|---|---|---|
|
AWS |
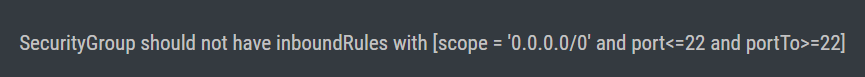
Ensure no security groups allow ingress from 0.0.0.0/0 to SSH (TCP:22) |
|
|
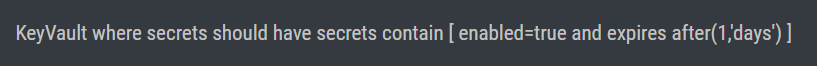
Azure |
Ensure that all Secrets in Azure Key Vault have an expiry time set |
|
|
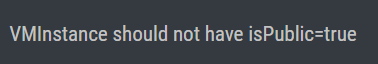
GCP |
Ensure no Google Instance has a Public IP (public facing services should be behind WAF, ELB, or other protection mechanisms) |
|
|
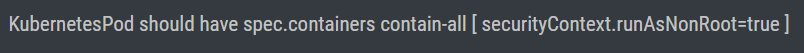
Kubernetes |
Do not permit containers to be run as the root user |
Watch Video for Creating Customized Rules with GSL