5. Cloud Intelligence & Threat Hunting
In order to detect threats in the cloud and to be able to understand what happened with speed and accuracy, you need to have a lot of context.
Otherwise, either you will be too slow or you will have too many false positives.
CloudGuard Threat Intelligence collects more data that brings you more context to make decisions than any other solution out there.
It correlates information from network configurations, user activity, traffic logs, and cloud logs to bring you an accurate full picture that is precise and prevents alert fatigue
Instructions
|
Step |
Instructions |
||
|---|---|---|---|
|
1 |
Navigate to CDR tab.
|
||
|
2 |
Navigate to Traffic Explorer. |
||
|
3 |
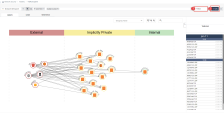
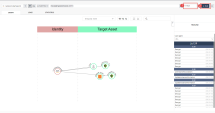
Change timeline to 7 Days and click Run. The Traffic Explorer tab shows you a visualization of network traffic in your cloud environment using AWS VPC Flow Logs. Flow Logs is a feature that enables you to capture information about the IP traffic going to and from network interfaces. You can use this to identify traffic from unwanted sources. |
||
|
4 |
Click on a circle in the Implicitly Private section. Clicking on any of these nodes shows you relevant information about it on the right. The arrows represent the related traffic. |
||
|
5 |
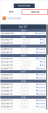
Click on TIMELINE on the right. In the TIMELINE you can see a breakdown of all the related traffic to the node you clicked on. This is summarizing the information you can find in LOGS. |
|
Step |
Instructions |
|---|---|
|
1 |
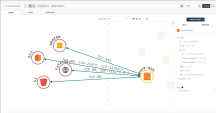
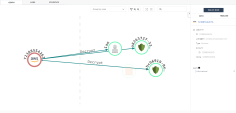
Click back to CDR and then click on Activity Explorer. The Activity Explorer shows a visualization of events in your cloud environments using AWS CloudTrail logs. CloudTrail tracks recent events and AWS API calls for your account. CloudTrail helps enable things like governance, compliance, auditing, and risk analysis for your account |
|
2 |
Change timeline to 1 Hour and click Run. |
|
3 |
Click on node under the Identity column, This view shows you which identity accessed a Target Asset. There are three methods for accessing an account or target asset:
|
|
4 |
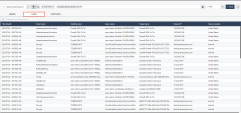
Click on LOGS. You can drill down further to understand which method issued the permissions for that Identity to access the Target Asset through the logs. |
|
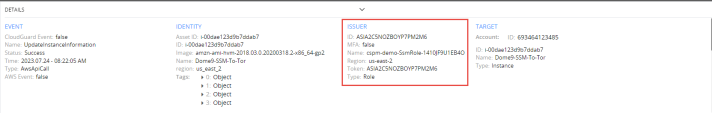
5 |
Click on any of the logs and highlight the ISSUER section in DETAILS at the bottom. |