7. Cloud Infrastructure Entitlement Management (CIEM)
Introduction
-
CIEM helps you comply with the principle of least privilege, CIEM makes sure that your cloud assets, human or non-human (e.g. Lambda functions), receive the smallest set of permissions necessary to do their tasks.
-
CIEM provides visibility into cloud entitlements through a permissions map and calculates the effective permissions. In addition, CIEM identifies and alerts about misconfigurations and suspicious activities related to IAM.
-
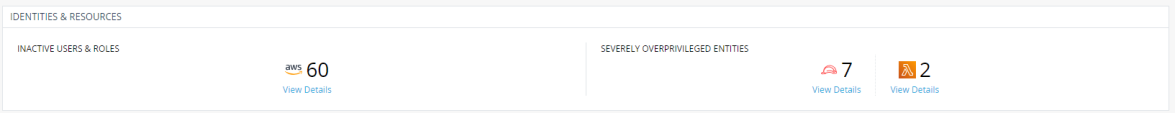
Finally, CIEM automatically identifies overprivileged entities and recommends right-sized policies.
Discussion points
-
Give visibility into cloud entitlements and effective permissions.
-
Identify & alert about inactive and misconfigured entities and anomalous behavior.
-
Automatically finds overprivileged entities policies based on actual use and recommends the right privileges.
Instructions
|
Step |
Instructions |
|---|---|
|
1 |
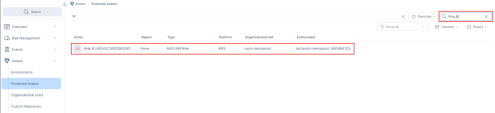
Navigate to Assets > Protected Assets. The very first thing in CIEM is getting visibility into cloud entitlements. Permissions can be defined in different ways and at different levels. For example, Organizations SCPs (Service Control Policies) are inherited within the organization and act as a mask to limit permissions granted elsewhere. So, understanding what permissions are granted to a cloud asset is a challenge on its own and a mandatory step before optimizing them. |
|
2 |
When you open an asset, a tab called Permissions allows you to review the permissions granted to the entity.
Open the following examples and navigate to the tab Permissions:
In AWS, it is possible to define trust relationships between roles. This is called role chaining and it practically means that a role can grant permissions from other roles to the entities that assume it. CloudGuard shows policies obtained via trust and takes them into account when calculating the effective policy of the role.
|
|
3 |
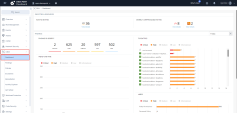
Navigate to CIEM > Dashboard: |
|
4 |
Click on the View Details of IamRole entities. |
|
5 |
Change the time-frame to All. |
|
6 |
Select the finding S3FullAccessRoleDemo.
|
|
7 |
Click on the Permissions tab. |