Proper Subset
When:
-
The encryption domain of Gateway B is fully contained in the encryption domain of Gateway A,
-
But Gateway A also has additional hosts that are not in Gateway B,
Then Gateway B is a proper subset of Gateway A.
For example, in the picture below, Gateway B is a proper subset of Gateway A.
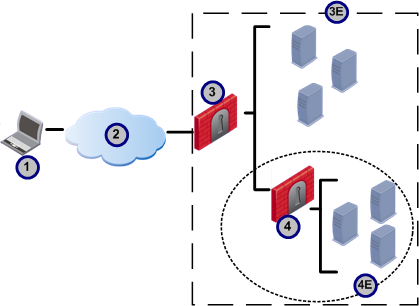
|
Item |
Description |
|---|---|
|
1 |
Remote Access client |
|
2 |
Internet |
|
3 |
Gateway A |
|
3E |
Encryption Domain for Gateway A |
|
4 |
Gateway B |
|
4E |
Encryption Domain for Gateway B |
Remote Access Clients support overlapping encryption domains of this type using Secondary Connect. The client creates an encrypted connection with the Security Gateway closest to the host (the innermost gateway). In the picture above, the client creates an encrypted connection with Gateway B for hosts in Gateway B's encryption domain, and with Gateway A for all other hosts.
In the figure below, three encrypted domains are nested inside each other.
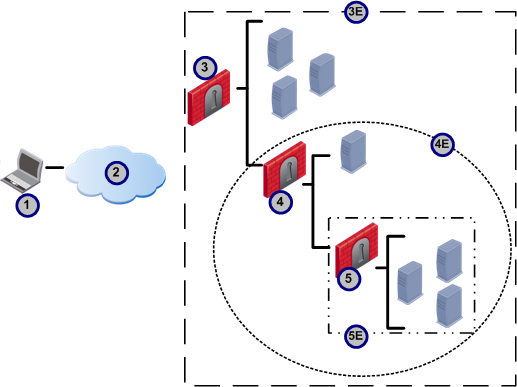
|
Item |
Description |
|---|---|
|
1 |
Remote Access client |
|
2 |
Internet |
|
3 |
Gateway A |
|
3E |
Encryption Domain for Gateway A |
|
4 |
Gateway B |
|
4E |
Encryption Domain for Gateway B |
|
5 |
Gateway C |
|
5E |
Encryption Domain for Gateway C |
The client creates encrypted connections according to these rules:
|
Host |
Connect to: |
|---|---|
|
Hosts in Gateway C's encryption domain |
Gateway C |
|
Host only in gateway B's encryption domain and not in another encryption domain |
Gateway B |
|
All other hosts |
Gateway A |
