VPN Domain Advanced Configuration
Advanced configuration of a VPN Domain is granular.
The procedures below provide the required steps in SmartConsole![]() Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on..
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on..
Excluding the VPN Gateway's External IP Addresses from the VPN Domain
If a third-party peer VPN Gateway excludes its external IP address from the VPN Domain, you must configure the Check Point VPN Gateway to exclude its own external IP addresses from the VPN Domain.
-
From the left navigation panel, click Gateways & Servers.
-
Double-click the Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. / Cluster
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. / Cluster Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. object.
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. object. -
From the left tree, expand Network Management and click VPN Domain.
-
In the Advanced section, select Exclude gateway's external IP addresses from the VPN Domain.
-
Click OK.
-
Install the Access Control policy on all Security Gateways, that participate in the same VPN Communities as this VPN Gateway / Cluster object.
Specific VPN Domain for Gateway Communities
|
|
Important - The Specific VPN Domain for Gateway Communities feature requires Security Gateways R80.40 and higher. |
If a Security Gateway participates in more than one VPN Community, you can configure a different VPN Domain for this Security Gateway for each VPN Community, in which it participates.
By default, a Security Gateway's Encryption Domain is shared with all the VPN Communities, in which this Security Gateway participates.
Access to different resources within the Encryption Domain is implemented using the Access Control Rule Base![]() All rules configured in a given Security Policy. Synonym: Rulebase..
All rules configured in a given Security Policy. Synonym: Rulebase..
In some cases you may need to configure the Encryption Domain in a granular way.
You can configure the VPN domain of a Security Gateway for each VPN Community, which makes it safer and easier to control the VPN Communities that are logically separated.
In SmartConsole, you can configure a specific VPN Domain for a Security Gateway in these objects:
-
In the Security Gateway object.
-
In the VPN Community object (to override the configuration from the Security Gateway object).
- From the left navigation panel, click Gateways & Servers.
-
Double-click the Security Gateway / Cluster object.
-
From the left tree, expand Network Management and click VPN Domain.
All IP Addresses behind Gateway based on Topology information is marked by default.
-
To set the VPN Domain manually, click User defined.
-
Click the three dots on the right of the selection window and select an existing network/group or create a new one for the VPN domain.
-
To exclude the Security Gateway’s external IP address from the VPN domain, in the Advanced section, check the check box: Exclude gateway’s external IP Address from the VPN domain.
-
To set an explicit VPN domain to a specific VPN community, click the Set button next to the line: Set Specific VPN Domain for Gateway Communities.
-
Select the applicable VPN Community and click Set.
For example:
-
Select the applicable option:
-
According to the gateway
This configuration option uses the VPN Domain that is configured in the Security Gateway object > in the Network Management folder > on the VPN Domain page > in the VPN Domain section.
-
User defined
Select the applicable Network or Network Group object (you can create a new object in this picker window).
-
-
Click OK to close the Set Specific VPN Domain for Gateway Communities window.
-
Click OK to close the Communities Specific VPN Domain window.
- Click OK to close the Security Gateway / Cluster object.
-
Install the Access Control policy on all Security Gateways that participate in the same VPN Communities as this Security Gateway / Cluster object.
-
In the top right corner, in the Objects pane, click VPN Communities.
-
Double-click the applicable VPN Community object.
-
On the Participating Gateways tab, double-click the applicable Security Gateway object (or create a new object).
-
In the VPN Domain section, select the applicable option:
-
Based on the Security Gateway object configuration
This configuration option uses the VPN Domain that is configured in the Security Gateway object > in the Network Management folder > on the VPN Domain page > in the VPN Domain section.
-
Override
Select the applicable Network or Network Group object (you can create a new object in this picker window).
-
-
Click OK to close the VPN Domain configuration window.
-
Click OK to close the VPN Community configuration window.
-
Install the Access Control policy on all Security Gateways that participate in this VPN Community.

-
"Security Gateway A" ("Partner A") is part of "Community-1".
-
"Security Gateway B" ("Partner B") is part of "Community-2".
-
"Security Gateway C" (Corporate Branch) is part of "Community 1" and "Community 2".
-
The network behind "Security Gateway C" - 10.2.2.0 is split into 2 networks using the 255.255.255.128 subnet mask.
In this scenario, the administrator limits the access from "Security Gateway A" in "Community 1" to some of the resources behind Security Gateway C, which is also part of "Community 1".
To allow access to the required resources from "Security Gateway A" to resources protected by "Security Gateway C", the administrator configures an Encryption Domain per the specific VPN Community.
For "Security Gateway C", the administrator must configure two Encryption Domains - one for "Community 1" and one for "Community 2".
The access is limited to the specific Encryption Domain - network 10.2.2.0/25.
Required configuration:
-
Open the Start VPN Community object.
-
From the left tree, click Gateways.
-
In the Center Gateways section, double-click the center Security Gateway that participates in more than one VPN community.
In this example, "Security Gateway C".
-
In the VPN Domain section, select the Override.
Select (or create) the Network object that represents the network that we allow "Security Gateway B" ("Partner B") to access.
In this example, Network address is 10.2.2.0 and Net Mask is 255.255.255.18
-
Click OK.
Using the same setup, you can use the Encryption Domain per Community configuration to allow access between "Host 1" and "Host 2" in both directions.
The configuration changes are applied to the Encryption Domain of "Security Gateway C" for each relevant VPN Communities. In this example, "Community 1" and "Community 2".
Required configuration:
|
Community |
Encryption Domain |
Install On |
|---|---|---|
|
"Community 1" |
Network behind "Security Gateway C" "Host 2" |
"Security Gateway C" "Security Gateway A" |
|
"Community 2" |
Network behind "Security Gateway C" "Host 1" |
"Security Gateway C" "Security Gateway B" |
-
Create a new host ("Host 2" behind "Security Gateway B") to represent the Encryption Domain of "Security Gateway C" to publish for "Security Gateway A".
-
Create a new host ("Host 1" behind "Security Gateway A") to represent the Encryption Domain of "Security Gateway C" to publish for "Security Gateway B".
-
Create a new Network Group to include the current Encryption Domain of "Security Gateway C" and the additional host ("Host 2") for "Community 1".
-
Create a new Network Group to include the current Encryption Domain of "Security Gateway C" and the additional host ("Host 1") for "Community 2".
-
For "Community 1", change the Encryption Domain for "Security Gateway C", use the new Network Group created in step 3.
-
For "Community 2", change the Encryption Domain for "Security Gateway C", use the new Network Group created in step 4.
This type of configuration "tricks" the satellite Security Gateways to think that the destination host is part of "Security Gateway C" Encryption Domain. Therefore, the satellite Security Gateways encrypt the packets that they send to the center Security Gateway. The center Security Gateway decrypts the packets, re-encrypts them, and then re-routes them to the other satellite Security Gateways.
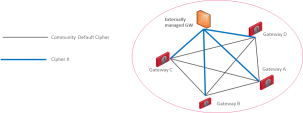
Granular Encryption for Externally Managed Gateways
|
|
Note - The Granular Encryption for an Externally Managed VPN Gateway feature requires Security Gateways R81 and higher. |
When you add an Externally Managed VPN Gateway to a VPN Community, the Externally Managed VPN Gateway may use a different encryption suite than the VPN Community.
With Granular Encryption, you can add an Externally Managed VPN Gateway that uses a different encryption suite to participate in an existing community without the need to change the encryption methods in use or split the VPN community.
|
|
Note - Make sure to create a Interoperable Device object that represents the External Gateway. In the top right corner, in the Objects pane, click New > More > Network Object > More > Interoperable Device. |
-
Open the VPN Community object.
-
From the left tree, click Encryption.
-
In the section Override Encryption for Externally Managed Gateways, click the + button.
The Granular Encryption window opens.
-
In the Encryption Context section:
The Security Gateways you select in this section use Granular Encryption.
-
In the Internal Gateway field, select one of these:
-
*Any - All locally managed Security Gateways that participate in this VPN Community use Granular Encryption to communicate with the External Gateway.
-
Specific Security Gateway / Cluster object - The selected Security Gateway / Cluster uses Granular Encryption to communicate with the External Gateway.

Note - This field shows only the Security Gateways that are already added to this VPN Community object. You can add a Security Gateway to this VPN Community on the Gateways page.
-
-
In the External Gateway field, select an Interoperable Device that represents the External Gateway.

Note - If Granular Encryption is set for a specific locally managed Security Gateway in addition to the use of "* Any" in a different Encryption Context, then the Granular Encryption settings apply.
-
-
In the Encryption Settings section, configure the required settings for the VPN communication between the selected peers.
-
Click OK to close the Granular Encryption window.
-
Click OK to close the VPN Community object.
-
Install the Access Control policy on all Security Gateways, that participate in this VPN Community.