Multiple Entry Point (MEP) VPNs
Overview of MEP
Multiple Entry Point (MEP) is a feature that provides a High Availability and Load Sharing solution for VPN connections. The VPN module is installed on a Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. that provides a single point of entry to the internal network. This Security Gateway makes the internal network "available" to peer Security Gateways. If the Security Gateway becomes unavailable, then peer Security Gateways cannot access the internal network.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. that provides a single point of entry to the internal network. This Security Gateway makes the internal network "available" to peer Security Gateways. If the Security Gateway becomes unavailable, then peer Security Gateways cannot access the internal network.
A MEP environment has two or more Security Gateways that enable access to the same VPN domain. In a MEP environment, peer Security Gateways provide redundancy for uninterrupted access to the internal network.
VPN High Availability Using MEP or Clustering
Both MEP and Clustering are ways of achieving High Availability and Load Sharing.
However:
-
Unlike the members of a ClusterXL Security Gateway Cluster
 Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing., there is no physical restriction on the location of MEP Security Gateways. MEP Security Gateways can be geographically separated machines. In a cluster, the clustered Security Gateways need to be in the same location, directly connected via a sync interface.
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing., there is no physical restriction on the location of MEP Security Gateways. MEP Security Gateways can be geographically separated machines. In a cluster, the clustered Security Gateways need to be in the same location, directly connected via a sync interface. -
MEP Security Gateways can be managed by different Security Management Servers. Cluster members must be managed by the same Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server..
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server.. -
In a MEP configuration there is no "state synchronization" between the MEP Security Gateways. In a cluster, all of the Security Gateways hold the "state" of all the connections to the internal network. If one of the Security Gateways fails, the connection passes seamlessly over (performs failover) to another Security Gateway, and the connection continues. In a MEP configuration, if a Security Gateway fails, the current connection is lost and one of the backup Security Gateways picks up the next connection.
-
In a MEP environment, the decision which Security Gateway to use is taken on the remote side; in a cluster, the decision is taken on the Security Gateway side.
MEP is implemented using RDP for Check Point Security Gateways and DPD for 3rd party Gateways / Cloud vendors.
-
RDP is a proprietary Probing Protocol (PP) that sends special UDP RDP packets to port 259 to discover whether an IP is reachable. This protocol is proprietary to Check Point and does not conform to RDP as specified in RFC 908 / RFC 1151.
Note - These UDP RDP packets are not encrypted, and only test the availability of a peer. -
DPD is a different method that discovers whether an IP is reachable. It supports third-party Security Gateways / Cloud vendors based on IKEv1/IKEv2.
|
|
Note -In an MEP environment, a Security Gateway determines which protocol to use automatically. |
The peer continuously probes or polls all MEP Security Gateways in order to discover which of the Security Gateways are "up", and chooses a Security Gateway according to the configured selection mechanism. Since RDP/DPD packets are constantly being sent, the status of all Security Gateways is known and updated when changes occur. As a result, all Security Gateways that are "up" are known.
There are two available methods to implement MEP:
|
MEP Method |
Description |
|---|---|
|
Explicit MEP |
Only Star communities with more than one central Security Gateway can enable explicit MEP. This MEP method provides multiple entry points to the network behind the Security Gateways. When available, Explicit MEP is the recommended method. |
|
Implicit MEP |
This MEP method is supported in all scenarios, where fully or partially overlapping encryption domains exist, or where Primary-Backup Security Gateways are configured. |
Known Limitation
-
If you configured Multiple Entry Point (MEP) and Legacy Link Selection with a Static NAT IP Address, then to use RDP probing with this NATed IP address, you must add this NATed IP address to the MEP Encryption Domain
 The networks that a Security Gateway protects and for which it encrypts and decrypts VPN traffic..
The networks that a Security Gateway protects and for which it encrypts and decrypts VPN traffic..
Explicit MEP
In a Site to Site VPN![]() An encrypted tunnel between two or more Security Gateways. Synonym: Site-to-Site VPN. Contractions: S2S VPN, S-to-S VPN. community of type Star, explicit MEP is configured in the VPN Community
An encrypted tunnel between two or more Security Gateways. Synonym: Site-to-Site VPN. Contractions: S2S VPN, S-to-S VPN. community of type Star, explicit MEP is configured in the VPN Community![]() A named collection of VPN domains, each protected by a VPN gateway. object. When MEP is enabled, the satellites consider the "unified" VPN domain of all the Security Gateways as the VPN domain for each Security Gateway. This unified VPN domain is considered the VPN domain of each Security Gateway:
A named collection of VPN domains, each protected by a VPN gateway. object. When MEP is enabled, the satellites consider the "unified" VPN domain of all the Security Gateways as the VPN domain for each Security Gateway. This unified VPN domain is considered the VPN domain of each Security Gateway:

In the figure, a Star VPN Community has two center Security Gateways, M1 and M2 (for which MEP has been enabled), and three satellite Security Gateways - S1, S2, and S3. When S2 opens a connection with Host-1 (which is behind M1 and M2), the session is initiated through either M1 or M2. Priority among the MEP Security Gateways is determined by the MEP entry point selection mechanism.
If M2 is the selected entry point and becomes unavailable, the connection to Host-1 fails over to M1. Returning packets will be rerouted with RIM or IP Pool NAT. For more information about returning packets, see the section "Routing Return Packets".
There are four methods used to choose which of the Security Gateways will be used as the entry point for any given connection:
|
Method |
Description |
|---|---|
|
Select the closest Security Gateway to source |
First to respond |
|
Select the closest Security Gateway to destination |
By VPN domain |
|
Random selection |
For Load distribution |
|
Manually set priority list |
MEP rules |
If you select either By VPN domain , or Manually set priority list, then Advanced options provide additional granularity.
MEP Selection Methods
|
MEP Selection Method |
Description |
|---|---|
|
First to Respond |
The first Security Gateway to reply to the peer Security Gateway is chosen. An organization would choose this option if, for example, the organization has two Security Gateways in a MEP configuration - one in London, the other in New York. It makes sense for VPN peers located in England to try the London Security Gateway first and the NY Security Gateway second. Being geographically closer to the peers in England, the London Security Gateway will be the first to respond, and becomes the entry point to the internal network. |
|
VPN Domain |
If the destination IP address belongs to a particular VPN domain, the Security Gateway of that domain becomes the chosen entry point. This Security Gateway becomes the Primary Security Gateway, while other Security Gateways in the MEP configuration become its Backup Security Gateways. |
|
Random Selection |
The remote peer randomly selects a Security Gateway, with which to open a VPN connection. For each source/destination IP address pair, a new Security Gateway is randomly selected. An organization might have a number of Security Gateways with equal performance abilities. In this case, it makes sense to enable load distribution to use these Security Gateways in a random and equal way. |
|
Manually set priority list |
Priorities of Security Gateways can be set manually for the entire VPN Community, or for individual satellite Security Gateways. |
When there is no primary Security Gateway, all Security Gateways share "equal priority".
When all Security Gateways share equal priority:
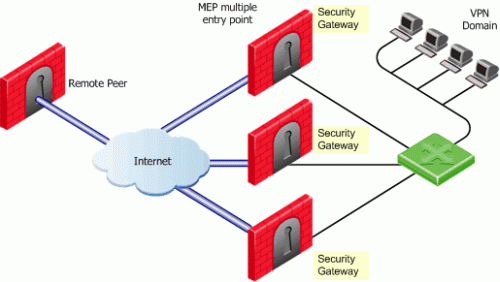
-
Remote peers send RDP/DPD packets to all the Security Gateways in the MEP configuration.
-
The first Security Gateway to respond to the probing RDP/DPD packets gets chosen as the entry point to network.
The idea behind first to respond is proximity. The Security Gateway, which is "closer" to the remote peer, responds first.
-
A VPN tunnel is opened with the first to respond. All subsequent connections pass through the chosen Security Gateway.
-
If the Security Gateway ceases to respond, a new Security Gateway is chosen.
Before you enable MEP, each IP address belongs to a specific VPN domain. With By VPN Domain, the Security Gateway of that domain becomes the chosen entry point.
In the example figure below, the VPN Star community has two central MEP Security Gateways (M1 and M2, each with its own VPN domain), and remote satellite S1.

Host-2 (in the VPN domain of satellite S1 initiates a connection with Host-1. The connection can be directed through either M1 or M2. However, Host-1 is within M2's original VPN domain. For this reason, M2 is considered the Security Gateway "closest" to the destination IP address. M2 is therefore considered the primary Security Gateway and M1 the backup Security Gateway for Host-1. If there were additional Security Gateways in the center, these Security Gateways would also be considered as backup Security Gateways for M2.
If the VPN domains have fully or partially overlapping encryption domains, then more than one Security Gateway will be chosen as the "closest" entry point to the network. As a result, more than one Security Gateway will be considered as "primary." When there are more than one primary or backup Security Gateways available, the Security Gateway is selected with an additional selection mechanism. This advanced selection mechanism can be either (see the section "Advanced Settings"):
-
First to Respond
-
Random Selection (for load distribution)
For return packets you can use RIM on the center Security Gateways. If RIM is also enabled, set a metric with a lower priority value for the leased line than the VPN tunnel. The satellite S1 might simultaneously have more than one VPN tunnel open with the MEP Security Gateways, for example M2 as the chosen entry point for Host-1 and M1 as the chosen entry point for Host-3. While both M1 and M2 will publish routes to Host-1 and Host-3, the lower priority metric will ensure the leased line is used only when one of the Security Gateways goes down.
With this method, a different Security Gateway is randomly selected as an entry point for incoming traffic. Evenly distributing the incoming traffic through all the available Security Gateways can help prevent one Security Gateway from becoming overwhelmed with too much incoming traffic.
The Security Gateways are probed with RDP/DPD packets, as in all other MEP configurations, to create a list of responding Security Gateways. A Security Gateway is randomly chosen from the list of responding Security Gateways. If a Security Gateway stops responding, another Security Gateway is (randomly) chosen.
A new Security Gateway is randomly selected for every source/destination IP addresses pair. While the source and destination IP addresses remain the same, the connection continues through the chosen Security Gateway.
In such a configuration, RIM is not supported. IP Pool NAT must be enabled to ensure return packets are correctly routed through the chosen Security Gateway.
The Security Gateway that will be chosen (from the center Security Gateways in the Star VPN Community) as the entry point to the core network can be controlled by manually setting a priority per source Security Gateway.
Each priority constitutes a MEP Rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session..
In the figure below, three MEP members (M1, M2, M3) provide entry points to the network for three satellite Security Gateways (S1, S2, S3). Satellite S1 can be configured to try the Security Gateways in the following order: M1, M2, M3, giving the highest priority to M1, and the lowest priority to M3. Satellite S2 can be configured to try the Security Gateways in the following order: M2, M3 (but not to try M1).
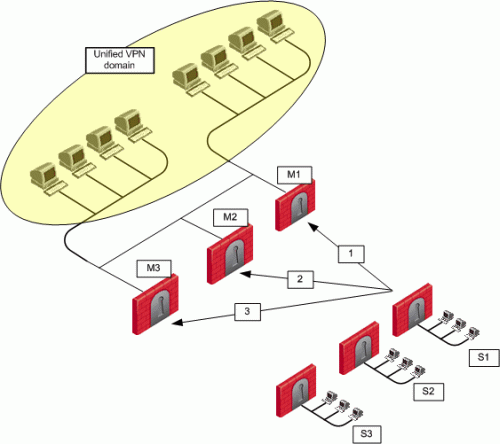
Each of these priorities constitutes a MEP rule in the MEP manual priority list window:
|
Item |
Description |
|---|---|
|
1 |
Default MEP Rule |
|
2 |
First MEP Rule |
|
3 |
Second MEP Rule |
The MEP manual priority list window is divided into the default rule, and rules which provide exceptions to the default rule. The default MEP rule takes effect when:
-
No MEP rules are defined
-
When the source of the connection cannot be found in the Exception priority rules
The Exception priority rules section contains three priority levels: primary, secondary, and tertiary. While there are only three priority levels,
-
The same priority can be assigned to several central Security Gateways
-
The same rule can be assigned to several satellite Security Gateways
-
A priority level can be left blank
In the second MEP rule below:
Central Security Gateways M3 and M1 have equal priority. The same rule is being applied to satellites S2 and S3.
When more than one Security Gateway is assigned the same priority level, which Security Gateway will be chosen is resolved according to the Advanced settings.
In some instances, more than one Security Gateway is available in the center with no obvious priority between them. For example - as shown in the second example of the second MEP rule, above - more than one Security Gateway is assigned "second" priority. In this scenario, Advanced options are used to decide which Security Gateway is chosen: First to Respond, or Random Selection. (Choose Random Selection to enable load balancing between the Security Gateways.)
When "manually set priority list" is the MEP selection mechanism, RIM is supported. RIM can be configured with "manually set priority list" because the "random selection" mechanism available on the Advanced button is different from the random selection mechanism used for MEP.
For the "random selection" mechanism employed for MEP, a different Security Gateway is selected for each source/destination IP addresses pair. For the random selection mechanism available from the Advanced button, a single MEP entry point is randomly selected and then used for all connections, and does not change according to source/destination pair. Load distribution is therefore achieved since every satellite Security Gateway is randomly assigned a Security Gateway as its entry point. This makes it possible to enable RIM at the same time.
If the Tracking option is enabled for MEP, this information is logged by each satellite Security Gateway:
-
The resolved peer Security Gateway (a Security Gateway in the MEP)
-
The priority of the resolved Security Gateway (primary, secondary, tertiary)
-
Whether the resolved Security Gateway is responding
For example, in the scenario shown in the section "Manually Set Priority List", satellite S1 opens a connection to the VPN domain that includes Security GatewaysM1, M2, and M3. M1 is the resolved peer. If tracking is enabled, the log reads:
|
|
Implicit MEP
These are the methods to implement implicit MEP:
|
Method |
Description |
||
|---|---|---|---|
|
First to Respond |
The first Security Gateway to reply to the peer Security Gateway is chosen. An organization would choose this option if, for example, the organization has two Security Gateways in a MEP configuration - one in London, the other in New York. It makes sense for VPN peers located in England to try the London Security Gateway first and the NY Security Gateway second. Being geographically closer to the peers in England, the London Security Gateway will be the first to respond, and becomes the entry point to the internal network.
|
||
|
Primary-Backup |
One or multiple backup Security Gateways provide "high availability" for a primary Security Gateway. The remote peer is configured to work with the primary Security Gateway, but switches to the backup Security Gateway if the primary goes down. An organization might decide to use this configuration if it has two Security Gateways in a MEP environment, one of which is stronger than the other. It makes sense to configure the stronger Security Gateway as the primary. Or perhaps both Security Gateways are the same in terms of strength of performance, but one has a cheaper or faster connection to the Internet. In this case, the Security Gateway with the better Internet connection should be configured as the primary. SeeOverview of the "Implicit Primary-Backup Security Gateways" method and Configuring the "Implicit Primary-Backup" method. |
||
|
Load Distribution |
The remote peer randomly selects a Security Gateway, with which to open a VPN connection. For each source/destination IP address pair, a new Security Gateway is randomly selected. An organization might have a number of Security Gateways with equal performance abilities. In this case, it makes sense to enable load distribution to use these Security Gateways in a random and equal way. See Overview of the "Implicit Load Distribution" method and Configuring the "Implicit Load Distribution" method. |
Implicit MEP is supported, if the Security Gateways with overlapping encryption domains are in the same community. If they are located in different communities, only one of the Security Gateways will be used for this encryption domain.
When there is no primary Security Gateway, all Security Gateways share "equal priority".
When all Security Gateways share "equal priority":
-
Remote VPN peers send RDP/DPD packets to all the Security Gateways in the MEP configuration.
-
The first Security Gateway to respond to the probing RDP/DPD packets gets chosen as the entry point to network.
The idea behind first to respond is "proximity". The Security Gateway which is "closer" to the remote VPN peer responds first.
-
A VPN tunnel is opened with the first to respond. All subsequent connections pass through the chosen Security Gateway.
-
If the Security Gateway ceases to respond, a new Security Gateway is chosen.
In a star VPN Community, RDP/DPD packets are sent to the Security Gateways and the first to respond is used for routing only when:
-
There is more than one center Security Gateway
-
One of the following VPN routing options was selected:
-
To center and to other satellites through center
-
To center, or through the center to other satellites, to internet and other VPN targets
This setting is found on the Community Properties > VPN Advanced > VPN Routing page.
-
In this example scenario:
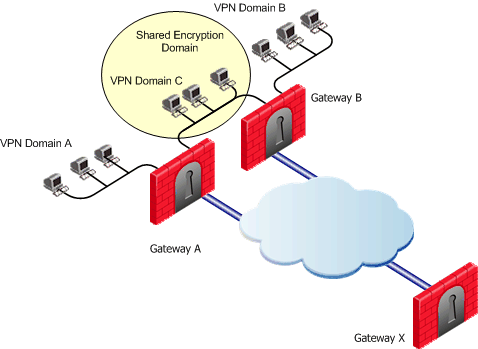
-
MEP is not enabled on the VPN Community
-
First to respond method is used
-
Security Gateway X accesses VPN domain A through Security Gateway A
-
Security Gateway X accesses VPN domain B through Security Gateway B
-
Security Gateway X accesses VPN domain C through Security Gateway A or B
Backup Security Gateways provide redundancy for primary Security Gateways.
The first Security Gateway is configured as the "primary," and the second Security Gateway as the "backup." If the primary Security Gateway fails, for whatever reason, the remote VPN peer detects that the link has gone down and works through the backup Security Gateway. The backup Security Gateway inherits the complete VPN domain of the primary Security Gateway. Failover within an existing connection is not supported; the current connection is lost.
When the primary Security Gateway is restored, new connections go through the primary Security Gateway, while connections that already exist will continue to work through the backup Security Gateway.
Important - When you use the Primary-Backup Security Gateways method, the encryption domains should not overlap.
To prevent any one Security Gateway from being flooded with connections, the connections can be evenly shared amongst all the Security Gateways to distribute the load. When all Security Gateways share equal priority (no primary) and are MEP to the same VPN domain, it is possible to enable load distribution between the Security Gateways. The Security Gateways are probed with RDP/DPD packets, as in all other MEP configurations, to create a list of responding Security Gateways. A Security Gateway is randomly chosen from the list of responding Security Gateways. If a Security Gateway stops responding, a new Security Gateway is (randomly) chosen.
A new Security Gateway is randomly selected for every source/destination IP addresses pair. While the source and destination IP addresses remain the same, the connection continues through the chosen Security Gateway.
Routing Return Packets
To make sure return packets are routed correctly, the MEP Security Gateway can make use of either of these:
-
IP Pool NAT (Static NAT)
-
Route Injection Mechanism (RIM)
IP Pool NAT is a type of NAT, in which source IP addresses from remote VPN domains are mapped to an IP address drawing from a pool of registered IP addresses. In order to maintain symmetric sessions with MEP Security Gateways, the MEP Security Gateway performs NAT with a range of IP addresses dedicated to that specific Security Gateway and should be routed within the internal network to the originating Security Gateway. When the returning packets reach the Security Gateway, the Security Gateway restores the original source IP address and forwards the packets to the source.
Route Injection Mechanism (RIM) enables a Security Gateway to use a dynamic routing protocol to propagate the encryption domain of a VPN peer Security Gateway to the internal network. When a VPN tunnel is created, RIM updates the local routing table of the Security Gateway to include the encryption domain of the VPN peer.
When a tunnel to a MEP Security Gateway goes down, the Security Gateway removes the applicable "return route" from its own local routing table. This change is then distributed backwards to the routers behind the Security Gateway.
RIM is based both on the ability of the Security Gateway to update its local routing table, and the presence of a dynamic routing protocol to distribute the change to the network behind the Security Gateway. There is little sense in enabling RIM on the Security Gateway if a dynamic routing protocol is not available to distribute changes.
When MEP is enabled, RIM can be enabled only if permanent tunnels are enabled for the whole community. In a MEP configuration RIM is available when you use the First to Respond, Manual set priority list, and VPN Domain mechanisms. In the first two options, satellite Security Gateways "see" the center Security Gateways as unified as if one tunnel is connecting them. As a result, only the chosen MEP Security Gateway will inject the routes. In VPN Domain MEP, it could be that all MEP Security Gateways will inject the routes, which requires configuring the routers behind the MEP Security Gateways to return packets to the correct Security Gateway.
RIM is not available when Random Selection is the selected entry point mechanism.
For more information, see Route Injection Mechanism.
Special Considerations
-
If one of the central Security Gateways is an externally managed Security Gateway:
-
The VPN domain of the central Security Gateways will not be automatically inherited by an externally managed Security Gateway
-
The RIM configuration will not be automatically downloaded
-
-
DAIP Security Gateways require DNS resolving in order to be configured as MEP Security Gateways.
Configuring MEP
To configure MEP, decide on:
-
The MEP method:
-
Explicit MEP.
-
Implicit MEP.
-
-
If required, method for returning reply packets:
-
IP Pool NAT
-
Route Injection Mechanism (see Route Injection Mechanism).
-
Configuring Explicit MEP
Explicit MEP is only available in Site to Site VPN Communities of type Star where multiple center Security Gateways are defined.
-
In SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., click Objects menu > Object Explorer.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., click Objects menu > Object Explorer. -
From the left tree, select VPN Communities.
-
Open the Star VPN Community object.
-
From the left tree, click MEP.
-
Select Enable center gateways as MEP.
-
Select the applicable entry point mechanism:
-
First to respond
-
By VPN domain
-
Random selection
-
Manual priority list
Notes:
-
If you select By VPN domain or Manually set priority list, then in the Advanced section choose First to respond or Random selection to resolve how more than one Security Gateway with equal priority should be selected.
-
If you select Manually set priority list, then click Set to create a series of MEP rules.
-
-
Select a Tracking option, if required.
-
Click OK.
-
Install the Access Control Policy.
Configuring Implicit MEP
Configure the VPN Domain that includes the Primary Security Gateway and another VPN Domain that includes only the Backup Security Gateways.
Configure each Security Gateway as either the Primary Security Gateway, or a Backup Security Gateway.
Procedure:
|
Step |
Instructions |
|---|---|
|
1 |
Enable the Backup Gateway options in Global properties:
|
|
2 |
Configure a Network Group object:
|
|
3 |
Configure the Primary Security Gateway object:
This Security Gateway is now the Primary Security Gateway for this VPN domain. |
|
4 |
Define the VPN for the Backup Security Gateways. Backup Security Gateways do not always have a VPN Domain of their own. They simply back up the Primary Security Gateway. |
|
5 |
If the Backup Security Gateway does not have a VPN Domain of its own, the VPN Domain should include only the Backup Security Gateway itself:
|
|
6 |
If the Backup Security Gateway does have a VPN Domain of its own:
Important - There must be no overlap between the VPN Domain of the Primary Security Gateway and the VPN Domain of the Backup Security Gateways - no IP address can belong to both VPN Domains. |
To configure implicit MEP for random Security Gateway selection in SmartConsole:
|
Step |
Instructions |
|---|---|
|
1 |
Enable load distribution for MEP configurations:
|
|
2 |
Configure a Network Group object:
|
|
3 |
Define the same VPN Domain for all the Security Gateways:
|
|
4 |
Install the Access Control Policy on all the Security Gateways. |
Configuring IP Pool NAT
|
Step |
Instructions |
|---|---|
|
1 |
Enable IP Pool NAT in the Global Properties:
|
|
2 |
For eachSecurity Gateway, configure an object that represents the IP Pool NAT addresses for that Security Gateway:
|
|
3 |
In eachSecurity Gateway, configure IP Pool NAT settings:
|
|
4 |
Install the Access Control Policy on all Security Gateways. |
|
5 |
Edit the routing table for each internal router, so that packets with an IP address assigned from the IP Pool NAT are routed to the applicable Security Gateway. |

