Enhanced Link Selection
Overview of Enhanced Link Selection
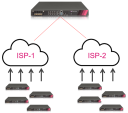
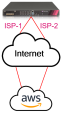
Enhanced Link Selection improves interoperability by enabling the configuration of multiple external interfaces for VPN connections. This feature supports redundancy and Load Sharing without relying on Check Point's proprietary VPN Link Selection protocol (RDP). It enhances compatibility with third-party and cloud-based Site-to-Site (S2S) IPsec vendors, overcoming limitations of previous configurations.
When multiple Site to Site VPN![]() An encrypted tunnel between two or more Security Gateways. Synonym: Site-to-Site VPN. Contractions: S2S VPN, S-to-S VPN. connections are established, the Security Gateway
An encrypted tunnel between two or more Security Gateways. Synonym: Site-to-Site VPN. Contractions: S2S VPN, S-to-S VPN. connections are established, the Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. monitors each connection to ensure it is operational. The Security Gateway use the primary connections when they are active. If none are available, the system switches to backup connections based on their configured priority.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. monitors each connection to ensure it is operational. The Security Gateway use the primary connections when they are active. If none are available, the system switches to backup connections based on their configured priority.
-
VPN Link Redundancy: Provides redundancy with third-party and cloud vendors.
-
Granular Link Selection: Configure link selection per gateway or per community.
-
Enhanced VPN Link Reliability: Improves link reliability by addressing vulnerabilities, such as "out-of-window" drops in tunnels serving multiple links.
-
Infrastructure for SD-WAN: Serves as the foundation for SD-WAN, which gives capabilities for modern networking needs.
-
Security Gateways with a Dynamically Assigned IP Address (DAIP)
-
Quantum Spark Gateways
-
Configurations with more than one IPv6 address per interface
-
Large Scale VPN (LSV)
-
ElasticXL
-
Security Group interfaces with more than one IPv6 address assigned (in Maestro and Scalable Chassis)
Configuration Steps for Enhanced Link Selection
The steps are used to configure enhanced link selection with the use of standard tunnels within a Site to Site VPN Star of Meshed community. Specifically, this configuration is meant to set up and manage VPN connections between multiple Security Gateways to ensure secure communication and efficient traffic management across different network interfaces.
|
|
Best Practice - If a Security Gateway participates in several VPN Communities, then we recommend to configure the required interfaces for the Enhanced Link Selection. |
You can configure the required interfaces in these ways (you can always override the current configuration):
|
Scenario |
Recommended Configuration |
|---|---|
|
In all VPN Communities, it is necessary to use the same interfaces on this Security Gateway. |
Select the required interfaces in the Security Gateway object > IPsec VPN section > Enhanced Link Selection page > Interfaces section. When you add this Security Gateway object in the VPN Community |
|
|
| In different VPN Communities is necessary to use different interfaces on this Security Gateway. | In each VPN Community object, in the Security Gateway object, override the default configuration to select the required interfaces. |
To configure Enhanced Link Selection within a Site to Site VPN Star or Meshed community, follow these steps in SmartConsole:
-
Create a VPN Community.
Create a Star VPN Community or a Meshed VPN Community object.
See Getting Started with Site to Site VPN.

Note - If you edit an existing VPN Community object, then on the Gateways page, in the Link Selection Mode, make sure to select Enhanced (Recommended).
-
Add the required Security Gateways to the VPN Community.
-
In a Meshed VPN Community, on the Gateways page, add the required Security Gateways in the section Participating Gateways.
-
In a Star VPN Community, on the Gateways page, add the required Security Gateways in the sections Center Gateways and Satellite Gateways.
By default, when you add a Security Gateway to a VPN Community, it uses the interfaces based on the Security Gateway object configuration.
 To select different Security Gateway interfaces in a VPN Community
To select different Security Gateway interfaces in a VPN Community
-
On the Gateways page, in the applicable section, select the Security Gateway object.
-
Click the pencil icon from the toolbar.
The "VPN configuration for <Name of Security Gateway Object> in <Name of VPN Community Object> community" window opens.
-
In the VPN Domain section, select the applicable option.
If you selected Override, then select the applicable Network or Network Group object.
In the picker window, you can configure a new required object.
-
In the Interfaces section, select Override.
-
Click the [+] icon.
-
Select the required interface and configure the required settings:
-
In the External Interface field, select the required interface.
-
Optional: In the Next Hop IP Address field, configure the IP address of the Next Hop.
If you do not configure an IP address, then the Security Gateway calculates it automatically based on the operating system routing table.
-
Optional: If this interface connects to a NAT device, configure the IP address in the Static NAT IP Address field to reflect the address after NAT.
-
In the Redundancy Mode field, select the required mode.
-
To configure VPN Load Sharing, select Active in all interfaces.
-
To configure VPN High Availability, set one interface to Active and the remaining interfaces to Backup.
 Use Case: What happens when you configure four interfaces and set all of them to Active?
Use Case: What happens when you configure four interfaces and set all of them to Active?
When you configure a Site to Site VPN with four interfaces set to Active, the IPsec traffic is distributed across four distinct tunnels.
Each tunnel uses a different external interface as its source IP address, while it connects to the designated peer IP address.
If the peer gateway is also configured with two active interfaces, the local gateways will establish a total of eight tunnels for VPN Load Sharing.
This configuration enhances redundancy and optimizes bandwidth usage by allowing simultaneous traffic distribution across multiple tunnels.
 Use Case: What happens when you configure four interfaces, with two set to Active and two set to Backup?
Use Case: What happens when you configure four interfaces, with two set to Active and two set to Backup?
IPsec traffic is distributed between the two active interfaces.
If both active interfaces fail, the backup interface with the highest priority becomes Active .
If the first-priority backup interface is also non-operational, the backup interface the next highest priority becomes Active .

Important - VPN Load Sharing decisions are made on a per-connection basis rather than per-packet basis.
-
-
If you selected Backup in the Redundancy Mode field, configure the desired priority in the Priority field.
This priority determines which Backup interface is selected if all Active interfaces are considered down. For example, if the next hop becomes unreachable due to an issue with an ISP.
-
Click OK to close the Interface Settings window.
-
-
Repeat steps e-f to add and configure additional interfaces as necessary.
-
Click OK to close the VPN configuration window.
-
Click OK to close the VPN Community object.
-
-
Configure Peer Gateways.
Repeat the configuration process for other Security Gateways in this VPN Community.
-
Verify Interface Availability.
-
The Security Gateway uses Dead Peer Detection (DPD) to monitor the status of the interface.
-
Ensure that DPD packets are being sent and received correctly to maintain the active status of the tunnel.
The Enhanced Link Selection uses DPD through IKE messages for tunnel resolution, and all Gateway vendors support this feature. DPD also serves to maintain tunnel activity continuously. But this is not its primary purpose, as a permanent tunnel can always be activated for that function. You can monitor the IKE session, including DPD activity, with the "
ikeview" tool.
-
-
Handle Failover.
-
Ensure the VPN connection can survive link failovers by automatically switching to backup tunnels.
Monitor the external interfaces, preferably with the "
fw monitor" tool. Alternatively, you can use "tcpdump" tool to identify the source of the ESP data during link failover.
Note - There may be a brief downtime during the transition of the VPN tunnel to the Backup interface.
-
Verify the failover functionality by monitoring DPD responses and IPsec tunnel renegotiation.
Verify that during failover, there is no DPD response on the failed Active tunnel. A new tunnel (IKE session) should establish with the backup peer IP address.
-
|
|
Important - When Enhanced Link Selection is enabled and you configure the interface of one of the Security Gateways with only one IP protocol version (IPv4 or IPv6), a tunnel negotiation that starts with the other protocol version falls back to Legacy Link Selection. |