Check Point VPN
IPsec VPN
The IPsec VPN![]() Check Point Software Blade on a Security Gateway that provides a Site to Site VPN and Remote Access VPN access. solution lets the Security Gateway
Check Point Software Blade on a Security Gateway that provides a Site to Site VPN and Remote Access VPN access. solution lets the Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. encrypt and decrypt traffic to and from other gateways and clients. Use SmartConsole
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. encrypt and decrypt traffic to and from other gateways and clients. Use SmartConsole![]() Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to easily configure VPN connections between Security Gateways and remote devices.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. to easily configure VPN connections between Security Gateways and remote devices.
For Site to Site Communities, you can configure Star and Mesh topologies for VPN networks, and include third-party gateways.
The VPN tunnel guarantees:
-
Authenticity - Uses standard authentication methods
-
Privacy - All VPN data is encrypted
-
Integrity - Uses industry-standard integrity assurance methods
IKE and IPsec
The Check Point VPN solution uses these secure VPN protocols to manage encryption keys, and send encrypted packets. IKE (Internet Key Exchange) is a standard key management protocol that is used to create the VPN tunnels. IPsec is protocol that supports secure IP communications that are authenticated and encrypted on private or public networks.
Remote Access VPN
If employees remotely access sensitive information from different locations and devices, system administrators must make sure that this access does not become a security vulnerability. Check Point's Remote Access VPN![]() An encrypted tunnel between remote access clients (such as Endpoint Security VPN) and a Security Gateway. solutions let you create a VPN tunnel between a remote user and the internal network. The Mobile Access
An encrypted tunnel between remote access clients (such as Endpoint Security VPN) and a Security Gateway. solutions let you create a VPN tunnel between a remote user and the internal network. The Mobile Access![]() Check Point Software Blade on a Security Gateway that provides a Remote Access VPN access for managed and unmanaged clients. Acronym: MAB. Software Blade
Check Point Software Blade on a Security Gateway that provides a Remote Access VPN access for managed and unmanaged clients. Acronym: MAB. Software Blade![]() Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. extends the functionality of Remote Access solutions to include many clients and deployments.
Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. extends the functionality of Remote Access solutions to include many clients and deployments.
VPN Connectivity Modes
The IPsec VPN Software Blade lets the Firewall overcome connectivity challenges for remote clients. Use VPN connectivity modes to make sure that remote users can connect to the VPN tunnels. These are some examples of connectivity challenges:
-
The IP addresses of a remote access client might be unknown
-
The remote access client can be connected to a hotel LAN with internal IP addresses
-
It is necessary for the remote client to use protocols that are not supported
Office Mode
Remote users can be assigned the same or non-routable IP addresses from the local ISP. Office Mode solves these routing problems and encapsulates the IP packets with an available IP address from the internal network. Remote users can send traffic as if they are in the office and do not have VPN routing problems.
Visitor Mode
Remote users can be restricted to use HTTP and HTTPS traffic only. Visitor Mode lets these users tunnel all protocols with a regular TCP connection on port 443.
Sample Remote Access VPN Workflow
Use SmartDashboard![]() Legacy Check Point GUI client used to create and manage the security settings in versions R77.30 and lower. In versions R80.X and higher is still used to configure specific legacy settings. to enable and configure the Security Gateway for remote access VPN connections. Then add the remote user information to the Security Management Server
Legacy Check Point GUI client used to create and manage the security settings in versions R77.30 and lower. In versions R80.X and higher is still used to configure specific legacy settings. to enable and configure the Security Gateway for remote access VPN connections. Then add the remote user information to the Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server.: create and configure an LDAP Account Unit or enter the information in the SmartDashboard user database. You can also configure the Firewall to authenticate the remote users. Define the Firewall access control and encryption rules. Create the LDAP group or user group object that is used for the Firewall rules. Then create and configure the encryption settings for the VPN community object. Add the access rules to the Firewall Rule Base
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server.: create and configure an LDAP Account Unit or enter the information in the SmartDashboard user database. You can also configure the Firewall to authenticate the remote users. Define the Firewall access control and encryption rules. Create the LDAP group or user group object that is used for the Firewall rules. Then create and configure the encryption settings for the VPN community object. Add the access rules to the Firewall Rule Base![]() All rules configured in a given Security Policy. Synonym: Rulebase. to allow VPN traffic to the internal networks.
All rules configured in a given Security Policy. Synonym: Rulebase. to allow VPN traffic to the internal networks.
VPN Components
VPN is composed of:
-
VPN endpoints, such as Security Gateways, Security Gateway clusters, or remote clients (such as laptop computers or mobile phones) that communicate over a VPN.
-
VPN trust entities, such as a Check Point Internal Certificate Authority (ICA
 Internal Certificate Authority. A component on Check Point Management Server that issues certificates for authentication.). The ICA is part of the Check Point suite used for creating SIC
Internal Certificate Authority. A component on Check Point Management Server that issues certificates for authentication.). The ICA is part of the Check Point suite used for creating SIC Secure Internal Communication. The Check Point proprietary mechanism with which Check Point computers that run Check Point software authenticate each other over SSL, for secure communication. This authentication is based on the certificates issued by the ICA on a Check Point Management Server. trusted connection between Security Gateways, authenticating administrators and third party servers. The ICA provides certificates for internal Security Gateways and remote access clients which negotiate the VPN link.
Secure Internal Communication. The Check Point proprietary mechanism with which Check Point computers that run Check Point software authenticate each other over SSL, for secure communication. This authentication is based on the certificates issued by the ICA on a Check Point Management Server. trusted connection between Security Gateways, authenticating administrators and third party servers. The ICA provides certificates for internal Security Gateways and remote access clients which negotiate the VPN link. -
VPN Management tools, such as Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. and SmartConsole. The SmartConsole lets organizations define and deploy Intranet, and remote Access VPNs.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. and SmartConsole. The SmartConsole lets organizations define and deploy Intranet, and remote Access VPNs.
Understanding the Terminology
-
VPN - Virtual Private Network. A secure, encrypted connection between networks and remote clients on a public infrastructure, to give authenticated remote users and sites secured access to an organization's network and resources.
-
VPN Domain - A group of computers and networks connected to a VPN tunnel by one VPN gateway that handles encryption and protects the VPN Domain members.
-
VPN Community - A named collection of VPN domains, each protected by a VPN gateway.
-
VPN Security Gateway - The gateway that manages encryption and decryption of traffic between members of a VPN Domain, typically located at one (Remote Access VPN) or both (Site to Site VPN
 An encrypted tunnel between two or more Security Gateways. Synonym: Site-to-Site VPN. Contractions: S2S VPN, S-to-S VPN.) ends of a VPN tunnel.
An encrypted tunnel between two or more Security Gateways. Synonym: Site-to-Site VPN. Contractions: S2S VPN, S-to-S VPN.) ends of a VPN tunnel. -
Site to Site VPN - An encrypted tunnel between two gateways, typically of different geographical sites.
-
Remote Access VPN - An encryption tunnel between a Security Gateway and remote access clients, such as Endpoint Security VPN, and communities.
-
Remote Access Community - A group of computers, appliances, and devices that access, with authentication and encryption, the internal protected network from physically remote sites.
-
IKE (Internet Key Exchange) - An Encryption key management protocol that enhances IPSec by providing additional features, flexibility, and ease of configuration.
-
IPsec - A set of secure VPN protocols that manage encryption keys and encrypted packet traffic, to create a standard for authentication and encryption services.
Establishing a Connection between a Remote User and a Security Gateway
A VPN tunnel establishment process is initiated to allow the user to access a network resource protected by a Security Gateway. An IKE negotiation takes place between the peers.
During IKE negotiation, the peers' identities are authenticated. The Security Gateway verifies the user's identity and the client verifies that of the Security Gateway. The authentication can be performed using several methods, including digital certificates issued by the Internal Certificate Authority (ICA). It is also possible to authenticate using third-party PKI solutions and pre-shared secrets.
After the IKE negotiation ends successfully, a secure connection (a VPN tunnel) is established between the client and the Security Gateway. All connections between the client and the Security Gateway VPN domain (the LAN behind the Security Gateway) are encrypted inside this VPN tunnel, using the IPsec standard. Except for when the user is asked to authenticate in some manner, the VPN establishment process is transparent.
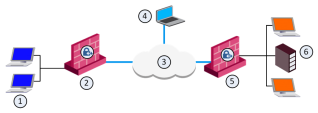
|
Item |
Description |
|---|---|
|
1 |
Host 1. Part of VPN Site 1. |
|
2 |
VPN Gateway 1. Part of VPN Site 1. |
|
3 |
Internet |
|
4 |
Remote Client |
|
5 |
VPN Gateway 2. Part of VPN Site 2. |
|
6 |
LDAP Server. Part of VPN Site 2. |
In the figure:
-
The remote user initiates a connection to Security Gateway 1.
-
User management is not performed via the VPN database, but by LDAP server belonging to VPN Site 2.
-
Authentication takes place during the IKE negotiation.
-
Security Gateway 1 verifies that the user exists by querying the LDAP server behind Security Gateway 2.
-
After the user's existence is verified, the Security Gateway authenticates the user, for example by validating the user's certificate.
-
After IKE is successfully completed, a tunnel is created and the remote client connects to Host 1.
-
If the client is behind the Security Gateway (for example, if the user accesses the corporate LAN from a company office), connections from the client to destinations that are also behind the LAN Security Gateway are not encrypted.