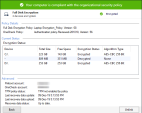
Configuring a Check Point Full Disk Encryption Policy
You can use the default Full Disk Encryption rule Default Full Disk Encryption settings for the entire organization. Edit the actions of the rule to your requirements. and install the policy.
Alternatively, use the following procedure to create a new Check Point Full Disk Encryption policy rule and configure actions for a specific organizational unit. After you install the Full Disk Encryption policy, make sure the policy is installed on the client.
-
Open SmartEndpoint and go to the Policy tab.
-
In the Policy toolbar, click the Create a Rule button
 .
.The Create Rule Wizard opens.
-
Select Full Disk Encryption
- Click Next.
-
In the Select Entities page, select the computers for which you want to configure Check Point Full Disk Encryption.
-
Click Next.
-
In the Change rule action settings page, select Encryption Engine: Use Check Point Full Disk Encryption .
-
Optionally, make changes to the default action settings.
-
Click Next.
-
In the Enter rule name and comment page, fill in the details.
-
Click Finish.
-
In the main toolbar, click Save rule, and Install the Policy.