Switching Between Check Point Full Disk Encryption and BitLocker Management
You can switch the encryption engine for selected clients from Check Point Full Disk Encryption to BitLocker Management, or from BitLocker Management to Full Disk Encryption.
|
|
Best Practice - When you change the encryption engine of a client from Check Point Full Disk Encryption to BitLocker Management, or from BitLocker Management to Check Point Full Disk Encryption, the disk on the client is decrypted and then encrypted. This causes the disk to be in an unencrypted state for some time during the process. We recommend that you do not change the entire organization to BitLocker in one operation. Make the change for one group of users at a time. |
-
Open SmartEndpoint and go to the Policy tab.
-
In the rule for Check Point Full Disk Encryption, in the Actions column, change the Encryption Engine action:
From Use Check Point Full Disk Encryption
To Use BitLocker Management.
-
In the main toolbar, click Save rule
 , and Install the Policy
, and Install the Policy 
-
On the client computers of the clients in the rule, this message shows:
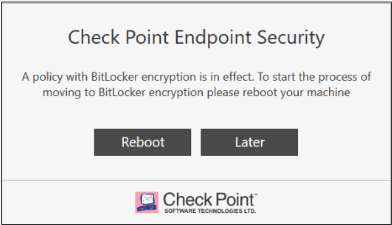
-
The user must click Reboot.
Decryption starts on the disk that is encrypted with Check Point Full Disk Encryption.
When the decryption is complete, the message shows a second time on the client computer.
-
The user must click Reboot.
Encryption of the disk starts with BitLocker Management.
BitLocker Management with encryption is now active on the Endpoint Security client computers in the rule.
-
Open SmartEndpoint and go to the Policy tab.
-
In the rule for Check Point Full Disk Encryption, in the Actions column, change the Encryption Engine action:
From Use BitLocker Management
To Use Check Point Full Disk Encryption.
-
In the main toolbar, click Save rule
 , and Install the Policy
, and Install the Policy  .
.Decryption of the BitLocker managed disks starts on the Endpoint Security client computers in the rule.
Encryption with Check Point Full Disk Encryption starts.
-
On the client computers this message shows:
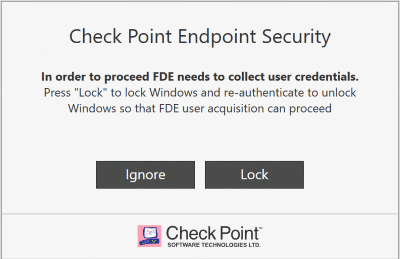
-
To allow Full Disk Encryption to collect the credentials of the user, the user must click Lock.
Check Point Full Disk Encryption is now active on the Endpoint Security client computer in the rule.

