VoIP Security Deployments
This section offers several use cases for deployment:
-
Enterprises
-
Perimeter VoIP gateway
-
LAN segmentation
-
-
Managed service providers
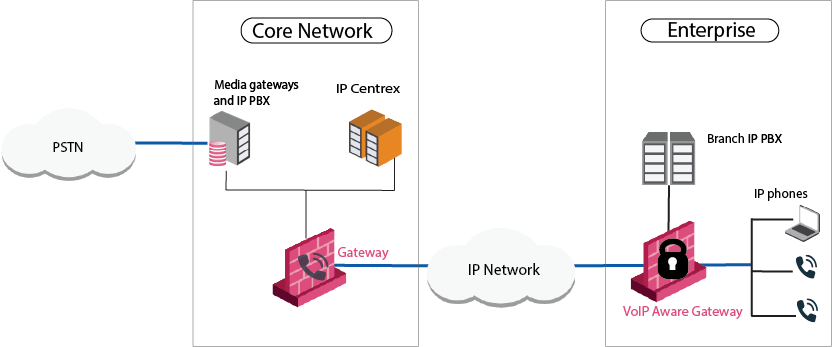
Use Case 1: Enterprise Deployment - Perimeter VoIP Gateway
In this enterprise environment, remote users and branch offices make VoIP calls to and from the protected enterprise network. The Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. is used to set up IPsec encrypted VPNs.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. is used to set up IPsec encrypted VPNs.
For example, a VPN can be set up between the main office and branch offices. Security capabilities for VoIP include:
-
Protecting servers and PBXs in the enterprise LAN against Denial of Service (DOS) attacks.
-
Preventing unauthorized phone calls by means of Media Admission Control. Only Configured servers can set up calls.
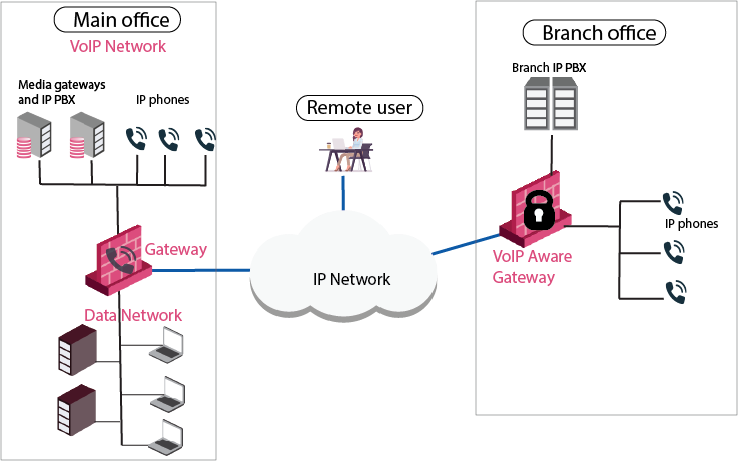
Use Case 2: Enterprise Deployment - LAN Segmentation
In this enterprise deployment, the Security Gateway is used for internal LAN segmentation of VoIP and data traffic.
Dedicated Security Gateways are deployed for VoIP security. Security is required to protect the availability of VoIP equipment such as servers and PBXs in the enterprise LAN.
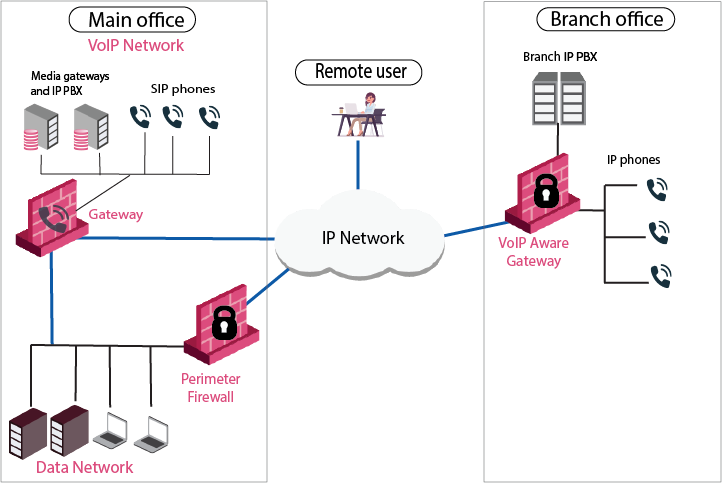
Use Case 3: Service Provider Deployment
A service provider environment enables secure enterprise services. The Security Gateway also makes it possible to implement strong security measures that are necessary for a high quality of service.