VSX Management Overview
VSX![]() Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. supports two Check Point management models: Security Management Server
Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. supports two Check Point management models: Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. and Multi-Domain Server
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. and Multi-Domain Server![]() Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS..
Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS..
Both models provide central configuration, management and monitoring for multiple VSX Gateways and Virtual Systems.
The choice of management model depends on several factors, including:
-
The scale of the current deployment and anticipated expansion
-
Administrative requirements
-
Physical and operational requirements
-
Licensing restrictions
You can use either management model to manage a "physical" Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. together with a VSX Gateway
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. together with a VSX Gateway![]() Physical server that hosts VSX virtual networks, including all Virtual Devices that provide the functionality of physical network devices. It holds at least one Virtual System, which is called VS0. and Virtual Systems.
Physical server that hosts VSX virtual networks, including all Virtual Devices that provide the functionality of physical network devices. It holds at least one Virtual System, which is called VS0. and Virtual Systems.
You can also manage VPN communities and remote connections with either model.
|
|
Note - According to the Check Point EULA (End User License Agreement), a Security Gateway can only manage security policies |
Security Management Server Model
The Security Management Server model is for enterprise deployments with many Virtual Systems, but one domain.
SmartConsole![]() Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. connects to the VSX Gateway, which contains the Virtual Systems, and directly manages each Virtual System
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. connects to the VSX Gateway, which contains the Virtual Systems, and directly manages each Virtual System![]() Virtual Device on a VSX Gateway or VSX Cluster Member that implements the functionality of a Security Gateway. Acronym: VS..
Virtual Device on a VSX Gateway or VSX Cluster Member that implements the functionality of a Security Gateway. Acronym: VS..
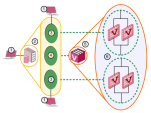
Multi-Domain Security Management Model
With Multi-Domain Security Management, you centrally manage multiple networks, typically of different Domains, divisions, or branches.
The Multi-Domain Server is the central management node that controls the policy databases for each of these networks.
Each Domain network is managed by a Domain Management Server, which provides the full functionality of a Security Management Server and can host multiple Virtual Systems, virtual and physical devices.
The Domain Management Server that manages a VSX Gateway or VSX Cluster![]() Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. is the Main Domain Management Server.
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. is the Main Domain Management Server.
A VSX Gateway or VSX Cluster can host Virtual Systems that are managed by different Domain Management Servers.
The Domain Management Server that manages a VSX Virtual System or VSX Virtual Router![]() Virtual Device on a VSX Gateway or VSX Cluster Member that functions as a physical router. Acronym: VR. is the Target Domain Management Server.
Virtual Device on a VSX Gateway or VSX Cluster Member that functions as a physical router. Acronym: VR. is the Target Domain Management Server.
|
Item |
Description |
|---|---|
|
1 |
SmartConsole |
|
2 |
Multi-Domain Server |
|
3 |
Domain Management Server |
|
4 |
Main Domain Management Server |
|
5 |
VSX Gateway |
|
6 |
Virtual Systems in Domain Management Servers |
From a SmartConsole connected to a Multi-Domain Server, provision and configure Domains and Domain Management Servers.
Each Domain Management Server uses its own SmartConsole instance to provision and configure its Virtual Systems, Virtual Devices, and policies.
Management Model Comparison
The following table summarizes the capabilities and differences between the two management models.
The capacity figures shown for Multi-Domain Server represent estimated, practical limits that will sustain acceptable performance levels under normal conditions.
Actual performance is dependent on many factors, including deployed hardware, network topology, traffic load and security requirements.
Management Server Communication - SIC
All communication between the Management Server and the VSX Gateway is accomplished by means of Secure Internal Communication (SIC![]() Secure Internal Communication. The Check Point proprietary mechanism with which Check Point computers that run Check Point software authenticate each other over SSL, for secure communication. This authentication is based on the certificates issued by the ICA on a Check Point Management Server.), a certificate based channel that authenticates communication between Check Point components.
Secure Internal Communication. The Check Point proprietary mechanism with which Check Point computers that run Check Point software authenticate each other over SSL, for secure communication. This authentication is based on the certificates issued by the ICA on a Check Point Management Server.), a certificate based channel that authenticates communication between Check Point components.
The Management Server uses SIC for provisioning Virtual Devices, policy installation, logging, and status monitoring.
SIC trust is initially established using a one-time password during configuration of the VSX Gateway or VSX Cluster Members.
For Multi-Domain Security Management deployments, SIC trust is established between the Domain Management Server associated with the VSX Gateway or VSX Cluster (Main Domain Management Server).
The Virtual Devices establish trust in a different manner than their physical counterparts.
When you create a Virtual Device![]() Logical object that emulates the functionality of a type of physical network object. Virtual Device can be on of these: Virtual Router, Virtual System, or Virtual Switch., VSX automatically establishes SIC trust using the secure communication channel defined between the Management Server and the VSX Gateway.
Logical object that emulates the functionality of a type of physical network object. Virtual Device can be on of these: Virtual Router, Virtual System, or Virtual Switch., VSX automatically establishes SIC trust using the secure communication channel defined between the Management Server and the VSX Gateway.
The VSX Gateway uses its management interface for Secure Internal Communication between the Management Server and all Virtual Devices.