Deploying VSX - Organizational Deployment Strategies
This section presents deployment scenarios for different types of large organizations and illustrates how VSX![]() Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. provides security both internally and at the perimeter.
Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. provides security both internally and at the perimeter.
The discussion covers the following types of organizations:
-
Large Enterprises
-
Managed Service Providers
-
Data Centers
Enterprise Deployments
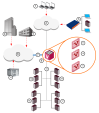
Large enterprise network environments typically have a variety of diverse networks, distributed over multiple locations around the world. These networks often have different security and access requirements for various departments and branches. The ability to centrally manage cyber security, and to maintain throughput, is a critical requirement.
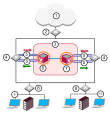
Core Network Security
Many Enterprise environments are based on core networks. Situated adjacent to core network backbone switches, VSX protects the internal network by providing security at Layer 2, Layer 3 or both. VSX communicates with the core network using the existing infrastructure. With Virtual Systems in the Bridge Mode![]() Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology., VSX can protect departmental networks, while simultaneously preventing network segmentation. In this case, switches are located at the entrance to each department's network.
Security Gateway or Virtual System that works as a Layer 2 bridge device for easy deployment in an existing topology., VSX can protect departmental networks, while simultaneously preventing network segmentation. In this case, switches are located at the entrance to each department's network.
VSX ensures connectivity between the core network and the Internet or external networks, while providing perimeter security.
Security can be configured on a per VLAN basis.
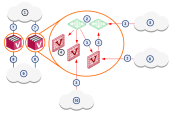
Dynamic Routing
In an enterprise network with dynamic routing protocols (OSPF/BGP), VSX secures the DMZ services, VPN peers, Domains and partner networks.
In this example, BGP neighbor updates in the routed core network are selectively redistributed to application networks.
OSPF provides connectivity between Virtual Routers, Virtual Systems, the core network and application networks.
Perimeter Security
For example, security is enforced on each VLAN. The OSPF and BGP Dynamic routing protocols provide connectivity to multiple security zones along the perimeter.
Notes to this scenario:
-
Partners access network resources remotely via Virtual Systems
-
Each Virtual System
 Virtual Device on a VSX Gateway or VSX Cluster Member that implements the functionality of a Security Gateway. Acronym: VS. has its own security policy
Virtual Device on a VSX Gateway or VSX Cluster Member that implements the functionality of a Security Gateway. Acronym: VS. has its own security policy Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. based on its requirements
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. based on its requirements -
Logs and audit information for each partner are collected separately, and saved to a private database
-
Applications and services are segregated by private Virtual Systems
-
Multiple Virtual Routers / Virtual Switches are used to control the access paths
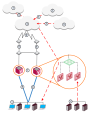
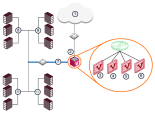
Managed Service Providers Using Multi-Domain Server
Managed service providers give connectivity and security services for Domain networks.
Some of these Domains require remote access capabilities.
In this service oriented environment, VSX and Multi-Domain Server![]() Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS. provide central management and make connectivity and security easier, without affecting the existing IP topology.
Dedicated Check Point server that runs Check Point software to host virtual Security Management Servers called Domain Management Servers. Synonym: Multi-Domain Security Management Server. Acronym: MDS. provide central management and make connectivity and security easier, without affecting the existing IP topology.
In this scenario, a VSX Cluster is in a Point of Presence (POP) deployment for a service provider.
VSX consolidates hardware for the service provider and ensures privacy and secure connectivity solutions (VPN) for users.
This scenario is appropriate for High Availability and Virtual System Load Sharing![]() VSX Cluster technology that assigns Virtual System traffic to different Active Cluster Members. Acronym: VSLS. cluster modes.
VSX Cluster technology that assigns Virtual System traffic to different Active Cluster Members. Acronym: VSLS. cluster modes.
VSX and Multi-Domain Server provide a centralized, granular provisioning system for a number of Domains.
Applications and services are separated by discrete Virtual Systems.
Access to these services and applications is based on need.
|
Item |
Description |
|---|---|
|
1 |
Internet. Routers are between the VSX Cluster Members and the Internet. |
|
2 |
VSX Cluster. One VSX Cluster Member |
|
3 |
Core IP VPN Network. |
|
4 |
Multi-Domain Server at the Network Operation Center monitors POP and connects to VSX Gateway The Multi-Domain Log Server |
|
5 |
Multi-Domain Server at the NOC and the VSX Gateway make the Local Exchange. |
|
6 |
Domain A web servers. |
|
7 |
Domain B DMZ. |
|
8 |
Domain C mail servers. |
|
9 |
PE Router. |
|
10, 11, 12 |
Domain A, B, and C. Each Domain manages its own security and cannot define Virtual Systems or other network components. Domains have secure VPN connectivity. |
|
13 |
Remote access |
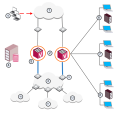
Data Centers
Data center providers supply external hosting services for Domain servers and databases.
The service typically includes infrastructure, connectivity, and security for multiple Domains.
For example, you can have a scenario such as:
-
Multiple Domain networks sharing a common physical infrastructure.
-
Backbone that provides connectivity between each Domain and the data center.
-
Domain A connects to its web hosting servers.
-
Domain B connects to its mail servers.
-
Domain C connects to its database servers.
For cyber security and management, the data center provider deploys a VSX Gateway with one Virtual System for each Domain.
This scenario offers a cost effective scalability solution for network expansion by means of remote connectivity.
In this example, a VPN connection between a Domain Virtual System and a Check Point appliance that protects a remote network, integrates that network in the MPLS core.
A Virtual System can give access to remote users who connect intermittently.
Data Centers in an Enterprise
This example scenario illustrates how VSX provides security management for enterprise data centers.
By assigning Layer 2 connections to Virtual Systems, VSX reduces the number of physically managed devices within a data center while providing the same high level of security.
For example, a VSX Gateway allows authorized users to access data center resources.
The objective here is to protect shared resources with differing access permissions and security requirements, while implementing network granularity.
For example, one Virtual System protects databases against SQL vulnerabilities.
Another Virtual System protects Web Servers using IPS![]() Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System)..
Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System)..
When new applications and services are added to the enterprise data center, new Virtual Systems are easily created to secure them according to their specific requirements.