Users that Received Malicious Emails (Prevented Attacks)
Description
In the main Cyber Attack View, in the Prevented Attacks section, double-click Users that Received Malicious Emails.
|
|
Note - Select the report period in the top left corner of this view. For example, Last 7 Days, This Month, and so on. |
The email vector is the common vector used to deliver a malicious payload.
This drill-down view shows a summary of email attack attempts.
The IPS![]() Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System)., Anti-Virus
Check Point Software Blade on a Security Gateway that inspects and analyzes packets and data for numerous types of risks (Intrusion Prevention System)., Anti-Virus![]() Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV., Threat Emulation
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV., Threat Emulation![]() Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Threat Extraction
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Threat Extraction![]() Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX.Software Blades work in parallel to determine if an email is malicious and provide multi-layer protection.
Check Point Software Blade on a Security Gateway that removes malicious content from files. Acronym: TEX.Software Blades work in parallel to determine if an email is malicious and provide multi-layer protection.
Drill-Down View
This is an obfuscated example of the drill-down view:
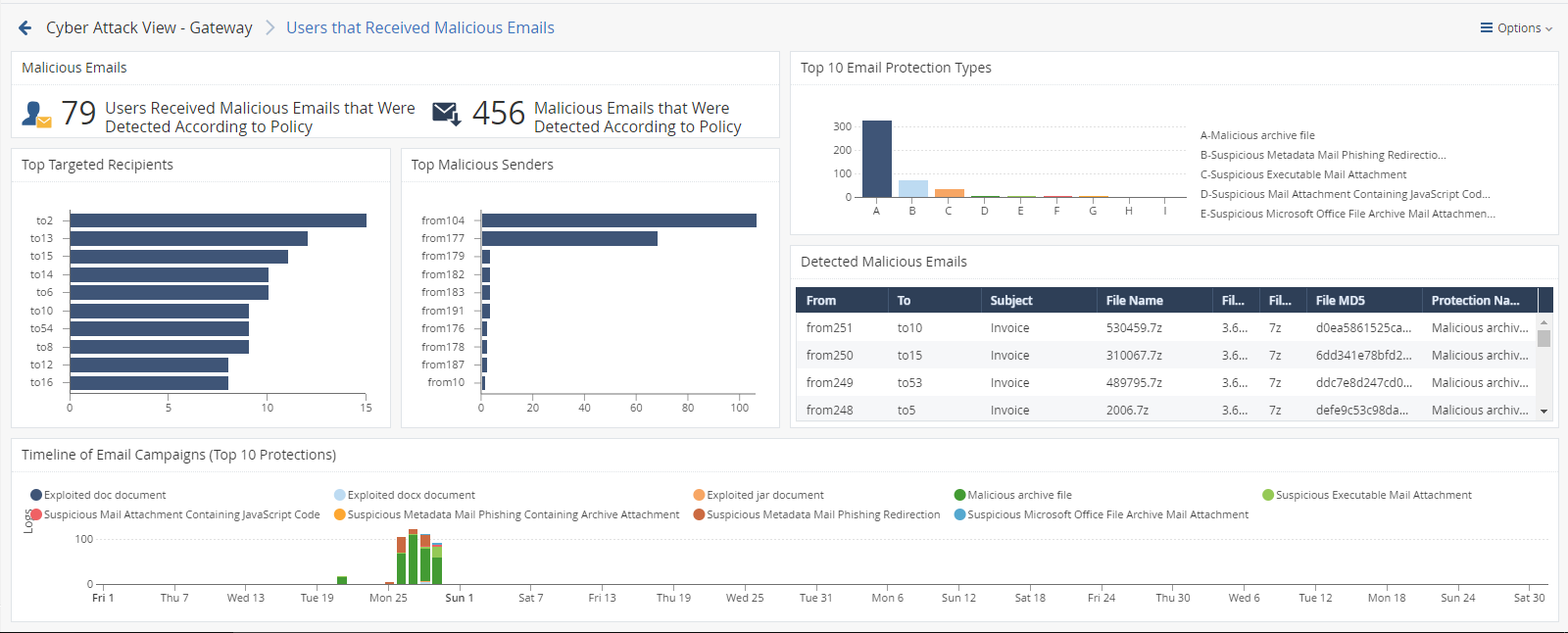
To see the applicable logs (the next drill-down level), double-click a value.
Available Widgets
Widgets available in the drill-down view:
|
Widget |
Type |
Description |
|---|---|---|
|
Malicious Emails |
Infographic |
Shows the total number of emails with content that the Security Gateway |
|
Top 10 Email Protection Types |
Chart |
Shows top Check Point protections that found malicious emails. Shows:
Different colors show different protection types. |
|
Top Targeted Recipients |
Chart |
Shows the recipients of malicious emails sorted by the number of emails they received. Shows:
Different colors show different recipients. |
|
Top Malicious Senders |
Chart |
Shows the senders of malicious emails sorted by the number of emails they sent. Shows:
Different colors show different senders. |
|
Detected Malicious Emails |
Table |
Shows malicious emails. Shows this information about the detected malicious emails:
|
|
Timeline of Email Campaigns (Top 10 Protections) |
Timeline |
Shows the number of detected malicious emails and their timeline. The timeline is divided into different protection types. Different colors show different campaigns. |
Widget Query
In addition to the Default Query, the widget runs this query:
|
|
|
|
Best Practices
Best practices against malicious emails:
-
Examine the Timeline of Email Campaigns (Top 10 Protections) to see email attack trends against your organization.
-
To fine-tune your email protection policy, examine the Top 10 Email Protection Types to see the top attack types.
For example, if you see that the top protection that detected malicious emails is Malicious archive file, you need to decide if your Security Policy
 Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. needs to allow archives in emails.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. needs to allow archives in emails.If you need to allow archives in emails, change your policy accordingly to prevent malicious files and not detect them. This includes enabling more Software Blades, if needed (such as Threat Emulationand Threat Extraction).
-
Examine the Top Targeted Recipients to understand:
-
Why are these internal email addresses exposed outside of your organization?
-
Should these internal email addresses be known outside of your organization from a business perspective?
-

