Use Case
You can use the ICAP technology to communicate HTTPS content.
You are a system administrator, who manages a network that includes a third party gateway/proxy and a Check Point Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources..
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources..
The Check Point Security Gateway enforces the Threat Emulation![]() Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Anti-Virus
Check Point Software Blade on a Security Gateway that monitors the behavior of files in a sandbox to determine whether or not they are malicious. Acronym: TE. and Anti-Virus![]() Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. blades.
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. blades.
The third party gateway/proxy has HTTPS Inspection![]() Feature on a Security Gateway that inspects traffic encrypted by the Secure Sockets Layer (SSL) protocol for malware or suspicious patterns. Synonym: SSL Inspection. Acronyms: HTTPSI, HTTPSi. enabled, but the Check Point Security Gateway does not.
Feature on a Security Gateway that inspects traffic encrypted by the Secure Sockets Layer (SSL) protocol for malware or suspicious patterns. Synonym: SSL Inspection. Acronyms: HTTPSI, HTTPSi. enabled, but the Check Point Security Gateway does not.
With the ICAP Client![]() The ICAP Client functionality in your Security Gateway or Cluster (in versions R80.40 and higher) enables it to interact with an ICAP Server responses (see RFC 3507), modify their content, and block the matched HTTP connections. and Check Point ICAP Server
The ICAP Client functionality in your Security Gateway or Cluster (in versions R80.40 and higher) enables it to interact with an ICAP Server responses (see RFC 3507), modify their content, and block the matched HTTP connections. and Check Point ICAP Server![]() The ICAP Server functionality in your Security Gateway or Cluster (in versions R80.40 and higher) enables it to interact with an ICAP Client requests, send the files for inspection, and return the verdict. enabled and configured to work together, the ICAP Client can send the decrypted traffic to the ICAP Server for inspection. This way, the Check Point Security Gateway can read the HTTPS content for the Threat Emulation and Anti-Virus blades, even if no HTTPS Inspection is enabled on the Check Point Security Gateway.
The ICAP Server functionality in your Security Gateway or Cluster (in versions R80.40 and higher) enables it to interact with an ICAP Client requests, send the files for inspection, and return the verdict. enabled and configured to work together, the ICAP Client can send the decrypted traffic to the ICAP Server for inspection. This way, the Check Point Security Gateway can read the HTTPS content for the Threat Emulation and Anti-Virus blades, even if no HTTPS Inspection is enabled on the Check Point Security Gateway.
|
Item No. |
Description |
|---|---|
|
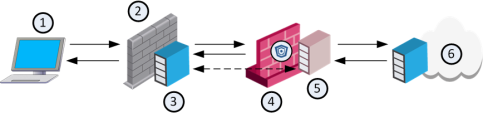
1 |
HTTPS client |
|
2 |
Third party gateway or proxy |
|
3 |
ICAP Client |
|
4 |
Check Point Security Gateway |
|
5 |
Check PointICAP Server |
|
6 |
Web server |
Workflow:
|
Step |
Instructions |
|---|---|
|
1 |
The HTTPS client initiates an HTTPS connection, which is sent to the proxy server. |
|
2 |
Proxy server forwards the HTTPS connection to the Check Point Security Gateway. |
|
3 |
The Check Point Security Gateway forwards the HTTPS connection to the web server. |
|
4 |
The web server sends the requested data over HTTPS to the Check Point Security Gateway. |
|
5 |
The Check Point Security Gateway forwards the HTTPS connection to the proxy server. |
|
6 |
The ICAP Client decrypts the HTTPS connection (the ICAP Client is configured to work in RESPMOD). |
|
7 |
The ICAP Client sends the decrypted HTTPS content to the ICAP Server for a verdict. |
|
8 |
The ICAP Server returns a verdict to the ICAP Client. |
|
9 |
Based on the verdict, the proxy server allows or blocks the requested HTTPS data. |