Hosts that Accessed Malicious Sites (Attacks Allowed By Policy)
Description
In the main Cyber Attack View, in the Attacks Allowed By Policy section, double-click Hosts that Accessed Malicious Sites.
The drill-down view summarizes access attempts to malicious sites from the internal network.
Drill-Down View
This is an obfuscated example of the drill-down view:
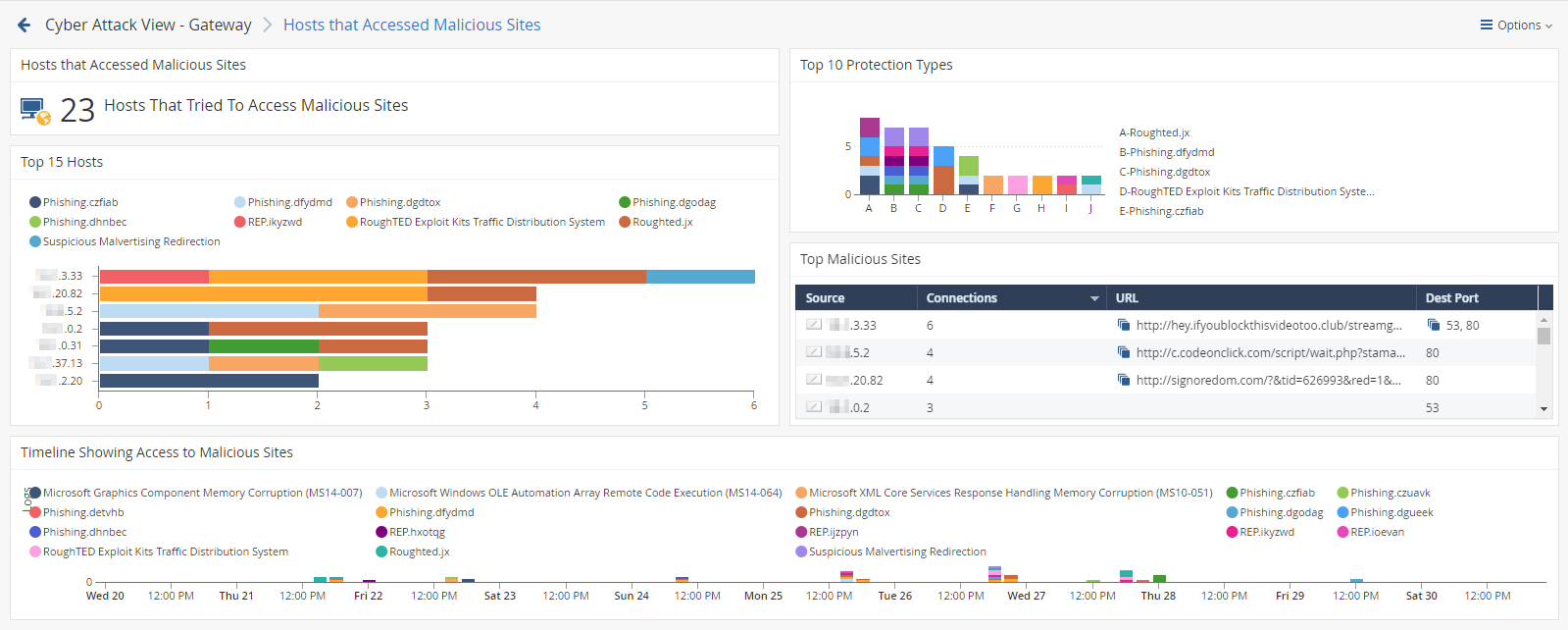
To see the applicable logs (the next drill-down level), double-click on a value.
Available Widgets
Widgets available in the drill-down view:
|
Widget |
Type |
Description |
|---|---|---|
|
Hosts that Accessed Malicious Sites |
Infographic |
Shows the number of internal hosts that accessed malicious websites. |
|
Top 10 Protection Types |
Chart |
Shows the number of events reported by web attack protections for the detected malware families (based on Check Point ThreatWiki and Check Point Research). Different colors show different malware families. |
|
Top 15 Hosts |
Chart |
Shows the internal hosts that accessed malicious websites. The chart is ordered by the number of connections from each host. Shows:
Different colors show different malware families. |
|
Top Malicious Sites |
Table |
Shows the information about malicious websites. Shows:
|
|
Timeline Showing Access to Malicious Sites |
Timeline |
Shows the detected malware families and their timeline. The timeline is divided into protection types. Different colors show different malware families. |
Widget Query
In addition to the Default Query, the widget runs this query:
|
|
|
|
Best Practices
Best practices against malicious sites:
-
Examine the Threat Prevention logs to determine how much data (if at all) your internal hosts sent to and received from malicious websites.
If these logs show extremely low, or zero, amount of data, read sk74120: Why Anti-Bot and Anti-Virus connections may be allowed even in Prevent mode.
-
In the Threat Prevention logs from the Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., examine the Description field (see Log Fields) to see if the Anti-Virus
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources., examine the Description field (see Log Fields) to see if the Anti-Virus Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. Software Blade
Check Point Software Blade on a Security Gateway that uses real-time virus signatures and anomaly-based protections from ThreatCloud to detect and block malware at the Security Gateway before users are affected. Acronym: AV. Software Blade Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. work is in the Background or Hold mode.
Specific security solution (module): (1) On a Security Gateway, each Software Blade inspects specific characteristics of the traffic (2) On a Management Server, each Software Blade enables different management capabilities. work is in the Background or Hold mode.In addition, read sk74120: Why Anti-Bot and Anti-Virus connections may be allowed even in Prevent mode.
