Configuring Infinity Threat Prevention
To configure Infinity Threat Prevention in your environment, follow these steps:
-
 Create an Infinity Threat Prevention Policy
Create an Infinity Threat Prevention Policy
Step
Instructions
1
In SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., go to Security Policies > Infinity Threat Prevention > Policy.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., go to Security Policies > Infinity Threat Prevention > Policy.2
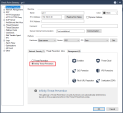
Click the drop-down arrow to see the list of profiles, and select the required profile.
If you are not sure which profile to select, click the Help me decide button from the drop-down list:
A table which specifies the differences between the profiles opens:
Based on the table, select the profile which best suits your needs.
3
Click OK.

Note - Each profile shows a list of the technologies that it uses.
-
 Install the Infinity Threat Prevention Policy
Install the Infinity Threat Prevention Policy
Step
Instructions
1
In SmartConsole, from the toolbar, select Install Policy.
The Install Policy window opens.
2
Select Threat Prevention.
3
Select the gateway targets for Policy installation.
Note - The Infinity Threat Prevention Policy will be installed on gateways with Infinity Threat Prevention enabled. Gateways with no Infinity Threat Prevention enabled will receive the traditional Threat Prevention Policy.
4
Click Install.
-
 Using different Infinity Threat Prevention profiles on different gateways
Using different Infinity Threat Prevention profiles on different gateways
Step
Instructions
1
In SmartConsole, create a new policy package.
From the main menu, click the drop-down arrow and select Manage policies and layers. The Manage policies and layers window opens. Click New and configure the new policy package. For more information on policy packages, see the R81 Security Management Administration Guide.
2
3
Select the required Infinity Threat Prevention profile. See Create an Infinity Threat Prevention Policy.
4
Install policy on the applicable gateway. See Install the Infinity Threat Prevention Policy.
|
|
Note - - MTA ( Mail Transfer Agent |
Exceptions
Global exceptions are available for use by gateways configured as Infinity Threat Prevention or by gateways configured with the traditional Threat Prevention policy. Global exceptions that existed prior to the migration to Infinity Threat Prevention are enforced in Infinity Threat Prevention without any action needed.
To add global exceptions to the Infinity Threat Prevention policy:
-
Go to the Security Policies view > Threat Prevention > Exceptions > Global Exceptions.
-
Add the applicable exceptions.
-
In the Install On column, select the gateways to which each exception applies.
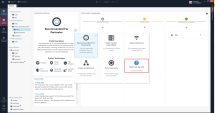
Deployment Dashboard
The Deployment Dashboard lets you gradually deploy Threat Prevention policy in your networks. The Deployment Dashboard includes three protection modes: No Protection, Detect Only and According to Profile.
According to profile - The settings of the Threat Prevention profile apply to the object. By default any traffic is protected according to Profile and this is the recommendation. If gradual deployment is needed, you can put specific network objects in "Detect![]() UserCheck rule action that allows traffic and files to enter the internal network and logs them. only". We recommend to move these object to According to Profile after a short trial period.
UserCheck rule action that allows traffic and files to enter the internal network and logs them. only". We recommend to move these object to According to Profile after a short trial period.
No Protection - The object is not protected by the selected Threat Prevention profile. Traffic is allowed and is not logged.
Detect only - Traffic is allowed, but it is logged according to the Threat Prevention profile settings.
 Note - You can easily drag and drop objects from any of the protection modes to any other protection mode
Note - You can easily drag and drop objects from any of the protection modes to any other protection mode
By default, the No Protection and Detect Only columns are empty, and the According to Profile column has one object: Any. When you add an object to the No Protection column or the Detect Only column, the object in the According to Profile column changes from Any to All Other.
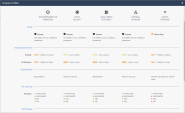
File Protections
In the File Protections page, you can:
-
View the protected file types and protection types for the selected Infinity Threat Prevention profile.
-
Override the recommended file protections according to profile and select different protections.
To configure file protections
-
Go to Threat Prevention > Infinity Threat Prevention > File Protections
-
Click on the + sign and configure the required protection.
These are the available protections:
-
Inspect - These technologies are operated: File Reputation, ThreatCloud
 The cyber intelligence center of all of Check Point products. Dynamically updated based on an innovative global network of threat sensors and invites organizations to share threat data and collaborate in the fight against modern malware. and Sandbox. You can see Sandbox is enabled in the Sandbox column.
The cyber intelligence center of all of Check Point products. Dynamically updated based on an innovative global network of threat sensors and invites organizations to share threat data and collaborate in the fight against modern malware. and Sandbox. You can see Sandbox is enabled in the Sandbox column. -
Inspect & Clean - These technologies are operated: File Reputation, ThreatCloud, Sandbox and Sanitization (CDR). You can see Sandbox is enabled in the Sandbox column..
-
Block - Block the file.
-
Bypass - Do not inspect the file.
You cannot override the protections for file types which are not on the list. File types which are not on the list will be inspected in all profiles.
-