Network Security for IoT Devices
Introduction
The complexity of using IoT devices in the modern work environment such as hospitals, industries, and smart-buildings has, at cost, exposed them to ill-natured and harmful cyber attacks. Malicious cyber invasions into IoT devices have caused considerable financial loss to a number of enterprises. In addition to monetary loss and physical damage, these attacks can lead to data breaches, data tampering, ransomware, and even denial of service.
Common IoT devices susceptible to attack:
|
Smart Buildings/Offices |
Healthcare |
Industry |
|---|---|---|
|
HVAC |
HVAC |
HVAC |
|
Printers, copiers, fax machines |
Printers, copiers, fax machines |
Printers, copiers, fax machines |
|
Elevators |
Elevators |
Elevators |
|
Surveillance Cameras |
Surveillance Cameras |
Surveillance Cameras |
|
Unhardened kiosk connected to a LAN |
Unhardened kiosk connected to a LAN |
Unhardened kiosk connected to a LAN |
|
Access control points |
Access control points |
Access control points |
|
Programmable logic controllers (PLCs) |
Programmable logic controllers (PLCs) |
Programmable logic controllers (PLCs) |
|
Thermostats |
Thermostats |
Thermostats |
|
Lighting |
Lighting |
Lighting |
|
Residential smart meters |
MRI machines |
-- |
|
Fire alarms |
Fire alarms |
Fire alarms |
|
N/A |
Ultrasound machines |
-- |
|
-- |
C-arms |
-- |
|
-- |
Infusion pumps |
-- |
|
-- |
Blood glucose meter |
-- |
|
-- |
Patient monitor |
-- |
What makes IoT devices so vulnerable:
-
Outdated software, legacy OS, or no OS
-
Basic Micro Controllers
-
No Security-by-Design
-
Lack of device management
-
Shadow Devices
-
Operational Limitations
Check Point's Infinity for IoT provides comprehensive network security for enterprise IT and IoT devices, smart building devices, industrial IoT, and connected medical equipment in these ways:
-
Prevent malicious intents and unauthorized access to IoT devices by analyzing multiple threat indicators from various resources.
-
Prevent infected devices from compromising other network elements.
-
Minimize the attack surface through internal network segmentation.
-
Provide deep insight information per IoT device.
-
Uses 3rd party discovery engine for IoT assets discovery.
-
Create separated IoT policy layer, using the discovered IoT device's attributes.
|
|
Notes:
|
Prerequisites
-
Check Point certified IoT Discovery Service installed on the network with a connection to the Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server..
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server.. -
Discovery Service
-
Industrial / Enterprise:
-
Armis
-
Claroty
-
Indegy
-
Ordr
-
SAM
-
SCADAfence
-
-
Medical:
-
Medigate
-
CyberMDX
-
Cynerio
-
-
-
Identity Awareness
 Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Web API must be activated on the enforcing Security Gateway
Check Point Software Blade on a Security Gateway that enforces network access and audits data based on network location, the identity of the user, and the identity of the computer. Acronym: IDA. Web API must be activated on the enforcing Security Gateway Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. (the configuration is done automatically).
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. (the configuration is done automatically). -
Security Gateway version R80.10 and above
|
|
Note - Enforcement of IoT assets in the Access Control policy is not supported on Centrally Managed Quantum Spark appliances running Gaia Embedded operating system. |
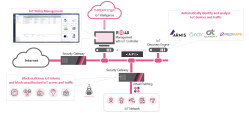
Network Overview
Check Point's Infinity for IoT delivers comprehensive IoT cyber-security by applying granular IoT-based policies. Check Point's IoT protection solution mobilizes hospitals, industries, smart buildings and offices to reduce and even eliminate IoT attacks.
-
Identify and analyze IoT devices and traffic
-
Deploy IoT policy enforcement points
-
Identify and block IoT malicious intents
Network Diagram
Configuring the IoT Controller
Before Check Point Infinity for IoT can protect IoT devices from malicious attacks, you must configure the IoT Third Party Discovery Service. The IoT Third Party Discovery Service configures a connection between the Check Point Management Server and the IoT Third Party Discovery Engines.
The IoT Third Party Discovery Engines:
-
Discover the connected IoT assets (mainly in the Industrial and Healthcare sectors).
-
Group the discovered assets into zones.
-
Share the discovered assets and the recommended policies with the Check Point Management Server.
|
Step |
Instructions |
|---|---|
|
1 |
Go to SmartConsole > Objects > New > More > IoT Discovery Service. |
|
2 |
To configure the General tab:
Infinity for IoT utilizes the Identity Awareness API. For easy activation, select the gateways where IoT enforcement will be done. To configure the Gateways tab:
To configure the Policies tab:
|
|
3 |
Publish the SmartConsole |
|
4 |
Install Policy. |
Configuring a new IoT Third Party Discovery Service generates a new IoT policy layer on the selected profiles, a new Threat Prevention profile, and a new rule![]() Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. in the Threat Prevention policy.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. in the Threat Prevention policy.
Adding IoT Assets to the Policy
After setting up the IoT policy, you can add IoT assets to the policy manually.
The policy is divided into three categories:
|
Category |
Description |
|---|---|
|
User-Defined |
Used by administrators. |
|
Auto-Generated |
Rules generated from network traffic and IoT network patterns. |
|
Cleanup |
A set of rules for detected anomalies. |
|
Step |
Instructions |
|---|---|
|
1 |
From Security Policies > Access Control, select the IoT Layer. |
|
2 |
Click User-Defined Section, and then click the plus sign. |
|
3 |
In the Source and/or Destination field, click the plus sign > Add new item.... |
|
4 |
Select Import > IoT Controllers, and then select the IoT asset to add to the rule. |
Infinity for IoT Logs
Using Check Point's IoT Security Manager, security teams can see detailed IoT device information. With a thorough log they gain a clearer, contextual understanding about the device's behavior and forensics for event investigation.
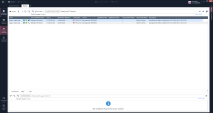
Example 1 - Log Search by IoT Asset Information
Advanced log search using the enriched log data to simplify log filtering.
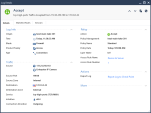
Example 2 - Extended Log Data
IoT log data contains enriched information that helps identify the IoT assets in the log.