IP Pool NAT
Overview
An IP Pool is a range of IP addresses that are routable to the Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources..
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources..
IP Pool NAT ensures proper routing for encrypted connections in these VPN connection scenarios:
-
Remote Access Client to MEP (Multiple Entry Point) Security Gateways
-
Security Gateway to MEP Security Gateways
When a connection is opened from a Remote Access Client or a client behind a Security Gateway, to a server behind the MEP Security Gateways, the packets are routed through one of the MEP Security Gateways.
Return packets in the connection must be routed back through the same Security Gateway in order to maintain the connection.
To ensure that this occurs, each of the MEP Security Gateways maintains a pool of IP addresses that are routable to the Security Gateway.
When a connection is opened to a server, the Security Gateway substitutes an IP address from the IP pool for the source IP address.
Reply packets from the server return to the Security Gateway, which restores the original source IP address and forwards the packets to the source.
NAT Priorities
IP Pool NAT can be used both for encrypted (VPN) and non-encrypted (decrypted by the Security Gateway) connections.
|
|
Note - To enable IP Pool NAT for clear connections through the Security Gateway, it is necessary to configure the required INSPECT settings in the applicable user.def file (see Location of 'user.def' Files on the Management Server). Contact Check Point Support for assistance. |
For non-encrypted connections, IP Pool NAT has the following advantages over Hide NAT:
-
New back connections (for example, X11) can be opened to the NATed host.
-
User-to-IP server mapping of protocols that allow one connection per IP can work with a number of hosts instead of only one host.
-
IPsec, GRE, and IGMP protocols can be NATed using IP Pool NAT (and Static NAT). Hide NAT works only with TCP, UDP, and ICMP protocols.
Because of these advantages, you can specify that IP Pool NAT has priority over Hide NAT, if both match the same connection. Hide NAT is only applied if the IP pool is used up.
The order of NAT priorities:
-
Static NAT
-
IP Pool NAT
-
Hide NAT
Because Static NAT has all of the advantages of IP Pool NAT and more, it has a higher priority than the other NAT methods.
IP Pool Per Interface
You can define a separate IP address pool on one or more of the Security Gateway interfaces instead of defining a single pool of IP addresses for the Security Gateway.
Defining an IP pool per interface solves routing issues that occur when the Security Gateway has more than two interfaces.
Sometimes it is necessary that reply packets return to the Security Gateway through the same Security Gateway interface.
Example:
This example diagram shows one of the MEP Security Gateways in a Remote Access Client to a MEP Security Gateway deployment:
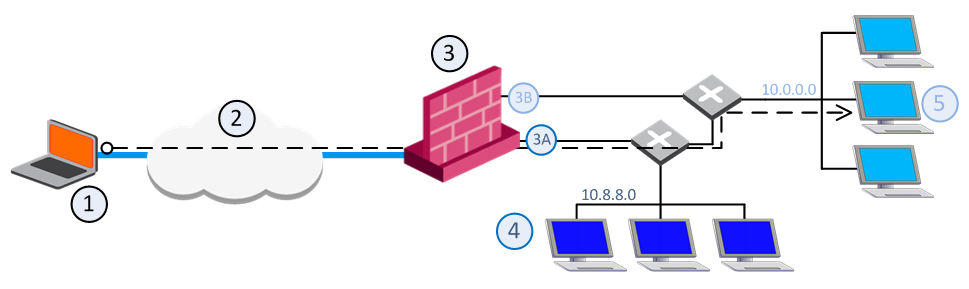
|
Item |
Description |
|---|---|
|
1 |
Packets from source host: Source: Original |
|
2 |
VPN tunnel through the Internet |
|
3 |
MEP Security Gateway |
|
3A |
IP Pool 1 packets: Source: 10.55.8.x |
|
3B |
IP Pool 2 packets: Source: 10.55.10.x |
|
4 |
Internal network 10.8.8.0 |
|
5 |
Target host in internal network 10.10.10.0 |
If a remote client opens a connection to the internal network, reply packets from hosts inside the internal networks are routed to the correct Security Gateway interface through the use of static IP pool NAT addresses.
The remote client's IP address is NATed to an address in the IP pool on one of the Security Gateway interfaces. The addresses in the IP pool can be routed only through that Security Gateway interface so that all reply packets from the target host are returned only to that interface. Therefore, it is important that the IP NAT pools of the interfaces do not overlap.
When the packet returns to the Security Gateway interface, the Security Gateway restores the remote peer's source IP address.
The routing tables on the routers that lie behind the Security Gateway must be edited so that addresses from a Security Gateway IP pool are returned to the correct Security Gateway interface.
Switching between IP Pool NAT per Security Gateway and IP Pool NAT per interface and then installing the security policy![]() Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. deletes all IP Pool allocation and all NATed connections.
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. deletes all IP Pool allocation and all NATed connections.
Reusing IP Pool Addresses For Different Destinations
IP Pool addresses can be reused for different destinations, which makes more efficient use of the addresses in the pool. If a pool contains N addresses, then any number of clients can be assigned an IP from the pool as long as there are no more than N clients per server.
Using IP Pool allocation per destination, two different clients can receive the same IP from the pool as long as they communicate with different servers (connections 1 and 2). When reusing addresses from the IP Pool, back connections are supported from the original server only (connection 3). This means that connections back to the client can be opened only from the specific server to which the connection was opened.
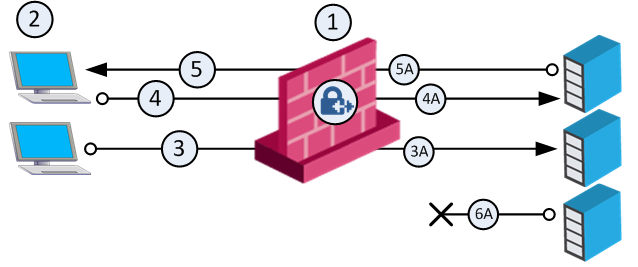
|
Item |
Description |
|---|---|
|
1 |
Security Gateway with IP Pool addresses A to Z |
|
2 |
Clients. Source: Original |
|
3A |
NATed packet from connection 3. Source: A |
|
4A |
NATed packet from connection 4. Source: A |
|
5A |
NATed packet from reply connection 5. Source: Original |
|
6A |
This server cannot open a connection with Destination A back to the client. |
The default Do not reuse IP Pool NAT behavior means that each IP address in the IP Pool is used once (connections 1 and 2 in the following illustration). In this mode, if an IP pool contains 20 addresses, up to 20 different clients can be NATed and back connections can be opened from any source to the client (connection 3).
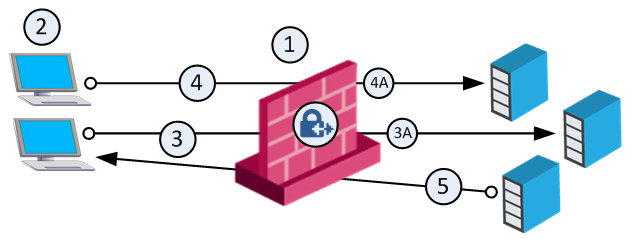
|
Item |
Description |
|---|---|
|
1 |
Security Gateway with IP Pool addresses A to Z. |
|
2 |
Clients. Source: Original |
|
3A |
NATed packet from connection 3. Source: A |
|
4A |
NATed packet from connection 4. Source: Z |
|
5 |
Connection. Source: Original |
Switching between the Reuse and Do not reuse modes and then installing the security policy, deletes all IP Pool allocations and all NATed connections.
IP Pool Configuration Procedure
-
 Enable IP Pool NAT in Global Properties
Enable IP Pool NAT in Global Properties
-
From the SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. , click Global properties.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. , click Global properties. -
In the Global properties > NAT page, select Enable IP Pool NAT and the required tracking options.
-
Click OK.
-
-
 For each Security Gateway or Security Gateway interface, create an object that represents its IP pool NAT addresses
For each Security Gateway or Security Gateway interface, create an object that represents its IP pool NAT addresses
This object can be a Network, Network Group, or Address Range.

Important:
-
In a Cluster
 Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing., you must configure separate IP Pool for each Cluster Member
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing., you must configure separate IP Pool for each Cluster Member Security Gateway that is part of a cluster..
Security Gateway that is part of a cluster.. -
It is not possible to configure a separate IP Pool for each Cluster Member interface.
For example, for an Address Range, do the following:
-
From the Objects Bar (F11), In the network objects tree, select New > More > Network Object > Address Range > Address Range.
-
In the General tab, enter the first and last IP addresses of the range.
-
Click OK.
-
-
 Enable and configure IP Pool NAT in the Security Gateway object
Enable and configure IP Pool NAT in the Security Gateway object
-
From the left navigation panel, click Gateways & Servers.
-
Double-click the Security Gateway / Cluster object.
-
From the left, expand NAT and click IP Pool NAT.
-
In the IP Pool NAT page, select one of these options:
In a Security Gateway object:
-
Allocate IP Addresses from and then select the address range you created to configure IP Pool NAT for the whole Security Gateway.
-
Define IP Pool NAT on Gateway interfaces to configure IP Pool NAT per interface.
In a Cluster object:
-
Define IP Pool NAT on each cluster member
-
Define IP Pool NAT on cluster member interfaces to configure IP Pool NAT per interface.
-
-
Optional: Select one or more of these options:
-
Use IP Pool NAT for VPN client connections
-
Use IP Pool NAT for gateway to gateway connections
-
Prefer IP Pool NAT over Hide NAT to specify that IP Pool NAT has priority over Hide NAT, if both match the same connection. Hide NAT is only applied if the IP pool was used up.
-
-
Optional: Configure the applicable advanced settings.
Click Advanced and configure:
-
Return unused addresses to IP Pool after
Addresses in the pool are reserved for 60 minutes (default), even if the user logs off. If the user disconnects from their ISP and then redials and reconnects, there will be two Pool NAT addresses in use for the user until the first address from the IP Pool times out. If users regularly lose their ISP connections, you may want to decrease the time-out to prevent the IP Pool from being depleted.
-
Reuse IP addresses from the pool for different destinations
This is a good option unless it is necessary to allow back connections to be opened to clients from any source, rather than just from the specific server to which the client originally opened the connection.
-
-
Click OK to close the Advanced IP Pool NAT Configuration window.
-
In a cluster object:
-
From the left, click Cluster Members.
-
Double-click each Cluster Member.
-
From the top, click the IP Pool NAT tab.
-
Select Use IP Pool NAT.
-
In the Allocate IP addresses from field, select the applicable object for this Cluster Member.

Important - In a Cluster, you must configure separate IP Pool for each Cluster Member. It is not possible to configure a separate IP Pool for each Cluster Member interface.
-
Click OK to close the Cluster Member Properties window.
-
-
Click OK to close the Security Gateway / Cluster object.
-
-
 Install the Security Policy
Install the Security Policy
-
Connect with the SmartConsole to the Security Management Server
 Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server..
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server.. -
Install the Access Control Policy on the remote Security Gateway / Cluster.
-
-
 Edit the routing table of each internal router
Edit the routing table of each internal router
Configure the applicable routes so that packets with an IP address assigned from the NAT pool are routed to the appropriate Security Gateway or, if using IP Pools per interface, the appropriate Security Gateway interface.

