Configuring a Security Gateway to Access the Management Server or Log Server at its NATed IP Address
Starting from R81 Jumbo Hotfix Accumulator Take 13, you can configure a Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. to access the Security Management Server
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. to access the Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. or Log Server
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. or Log Server![]() Dedicated Check Point server that runs Check Point software to store and process logs. at the server's NATed IP address for fetching policy or sending logs.
Dedicated Check Point server that runs Check Point software to store and process logs. at the server's NATed IP address for fetching policy or sending logs.
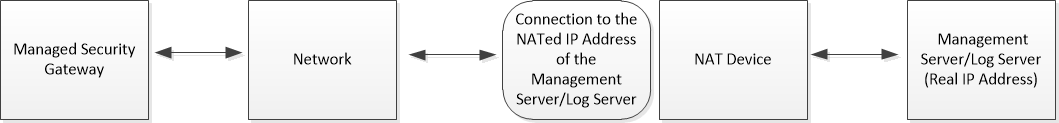
This diagram describes the flow of this process:
Procedure:
-
Connect to the command line on the Security Gateway / each Cluster Member
 Security Gateway that is part of a cluster..
Security Gateway that is part of a cluster.. -
Log in to the Expert mode.
-
On a VSX Gateway
 Physical server that hosts VSX virtual networks, including all Virtual Devices that provide the functionality of physical network devices. It holds at least one Virtual System, which is called VS0. / each VSX
Physical server that hosts VSX virtual networks, including all Virtual Devices that provide the functionality of physical network devices. It holds at least one Virtual System, which is called VS0. / each VSX Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. Cluster
Virtual System Extension. Check Point virtual networking solution, hosted on a computer or cluster with virtual abstractions of Check Point Security Gateways and other network devices. These Virtual Devices provide the same functionality as their physical counterparts. Cluster Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. Member, go to the context of the applicable Virtual System:
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. Member, go to the context of the applicable Virtual System:vsenv <VSID> -
Run the applicable command (this change survives reboot):
-
To force the Security Gateway / Cluster Member to connect only to the public (NATed) IP address (this is the default behavior) of the Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. or Log Server, run:
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. or Log Server, run:ckp_regedit -a SOFTWARE\\CheckPoint\\FW1 FORCE_NATTED_IP -n 1 -
To force the Security Gateway / Cluster Member to connect only to the real IP address of the Management Server or Log Server, run:
ckp_regedit -a SOFTWARE\\CheckPoint\\FW1 FORCE_NATTED_IP -n 0

Notes:
-
This change survives reboot.
-
In a Cluster, you must configure all the Cluster Members in the same way.
-
-
Restart the FWD process:
See the instructions in sk97638 > section Infrastructure Processes.
