Account Units
An Account Unit represents branches of user information on one or more LDAP servers. The Account Unit is the interface between the LDAP servers and the Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. and Security Gateways.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. and Security Gateways.
You can have a number of Account Units representing one or more LDAP servers. Users are divided among the branches of one Account Unit, or between different Account Units.
Working with LDAP Account Units
Use the LDAP Account Unit Properties window in SmartConsole to create a new or to edit an existing Account Unit or to create a new one manually.
To create or edit an existing LDAP Account Unit:
-
-
Create: In the Objects tab, click New > More > User/Identity > LDAP Account unit.
-
Edit: In SmartConsole, open the Object Explorer (press the CTRL+E keys) > Users/Identities > LDAP Account Units > Right-click the LDAP Account Unit and select Edit.
The LDAP Account Unit Properties window opens.
-
-
Edit the settings in these tabs:
-
 General
General
Configure how the Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. uses the Account Unit
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server. uses the Account UnitThese are the configuration fields in the General tab:
-
Name - Name for the Account Unit
-
Comment - Optional comment
-
Color - Optional color associated with the Account Unit
-
Profile - LDAP vendor
-
Domain - Domain of the Active Directory servers, when the same user name is used in multiple Account Units (this value is also necessary for AD Query and SSO)
-
Prefix - Prefix for non-Active Directory servers, when the same user name is used in multiple Account Units
-
Account Unit usage - Select applicable options:
-
CRL retrieval - The Security Management Server manages how the CA sends information about revoked licenses to the Security Gateways
-
User Management - The Security Management Server uses the user information from this LDAP server (User Directory
 Check Point Software Blade on a Management Server that integrates LDAP and other external user management servers with Check Point products and security solutions. must be enabled on the Security Management Server).
Check Point Software Blade on a Management Server that integrates LDAP and other external user management servers with Check Point products and security solutions. must be enabled on the Security Management Server).
Note - LDAP SSO (Single Sign On) is only supported for Account Unit objects that use User Management.
-
Active Directory Query - This Active Directory server is used as an Identity Awareness source.

Note - This option is only available if the Profile is set to Microsoft_AD.
-
-
Enable Unicode support - Encoding for LDAP user information in non-English languages
-
Active Directory SSO configuration - Click to configure Kerberos
 An authentication server for Microsoft Windows Active Directory Federation Services (ADFS). SSO for Active Directory - Domain Name, Account Name, Password, and Ticket encryption method
An authentication server for Microsoft Windows Active Directory Federation Services (ADFS). SSO for Active Directory - Domain Name, Account Name, Password, and Ticket encryption method
-
-
 Servers
Servers
Manage LDAP servers that are used by this Account Unit. You can add, edit, or delete LDAP server objects.
To configure an LDAP server for the Account Unit
-
To add a new server, click Add. To edit an existing one, select it from the table and click Edit.
The LDAP Server Properties window opens.
-
From the Host drop-down menu, select the server object.
If necessary, create a new SmartConsole server object:
-
Click New.
-
In the New Host window opens, enter the settings for the LDAP server.
-
Click OK.
-
-
Enter the login credentials and the Default priority.

Note - If you create the LDAP account unit to submit group queries, no special permissions are needed.
If you create the LDAP account unit to submit Active Directory queries, you must have the permissions provided in sk93938.
-
Select access permissions for the Check Point Gateways:
-
Read data from this server
-
Write data to this server
-
-
In the Encryption tab, configure the optional SSL encryption settings. To learn about these settings, see the Help. Click ? or press F1 in the Encryption tab.
-
Click OK.
To remove an LDAP server from the Account Unit:
-
Select a server from the table.
-
Click Remove.
If all the configured servers use the same login credentials, you can modify those simultaneously.
To configure the login credentials for all the servers simultaneously:
-
Click Update Account Credentials.
The Update Account to All Servers window opens.
-
Enter the login credentials.
-
Click OK.
-
-
 Objects Management
Objects Management
Configure the LDAP server for the Security Management Server to query and the branches to use

Note - Make sure there is LDAP connectivity between the Security Management Server and the LDAP Server that holds the management directory.
To configure LDAP query parameters:
-
From the Manage objects on drop-down menu, select the LDAP server object.
-
Click Fetch branches.
The Security Management Server queries and shows the LDAP branches.
-
Configure Branches in use:
-
To add a branch, click Add and in the LDAP Branch Definition window that opens, enter a new Branch Path
-
To edit a branch, click Edit and in the LDAP Branch Definition window that opens, modify the Branch Path
-
To delete a branch, select it and click Delete
-
-
Select Prompt for password when opening this Account Unit, if necessary (optional).
-
Configure the number of Return entries that are stored in the LDAP database (the default is 500).
-
-
 Authentication
Authentication
Configure the authentication scheme for the Account Unit. These are the configuration fields in the Authentication tab:
-
Use common group path for queries - Select to use one path for all the LDAP group objects (only one query is necessary for the group objects)
-
Allowed authentication schemes - Select one or more authentication schemes allowed to authenticate users in this Account Unit - Check Point Password, SecurID, RADIUS, OS Password, or TACACS
-
Users' default values - The default settings for new LDAP users:
-
User template - Template that you created
-
Default authentication scheme - one of the authentication schemes selected in the Allowed authentication schemes section
-
-
Limit login failures (optional):
-
Lock user's account after - Number of login failures, after which the account gets locked
-
Unlock user's account after - Number of seconds, after which the locked account becomes unlocked
-
-
IKE pre-shared secret encryption key - Pre-shared secret key for IKE users in this Account Unit
-
-
-
Click OK.
-
Install the Access Control Policy.
Configuring LDAP query parameters
-
From the Manage objects on drop-down menu, select the LDAP server object.
-
Click Fetch branches.
The Security Management Server queries and shows the LDAP branches.
-
Configure Branches in use:
-
To add a branch, click Add and in the LDAP Branch Definition window that opens, enter a new Branch Path
-
To edit a branch, click Edit and in the LDAP Branch Definition window that opens, modify the Branch Path
-
To delete a branch, select it and click Delete
-
-
Select Prompt for password when opening this Account Unit, if necessary (optional).
-
Configure the number of Return entries that are stored in the LDAP database (the default is 500).
Modifying the LDAP Server
-
On the LDAP Account Unit Properties > Servers tab, double-click a server.
The LDAP Server Properties window opens.
-
On the General tab, you can change:
-
Port of the LDAP server
-
Login DN
-
Password
-
Priority of the LDAP server, if there are multiple servers
-
Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. permissions on the LDAP server
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. permissions on the LDAP server
-
-
On the Encryption tab, you can change the encryption settings between Security Management Server / Security Gateways and LDAP server.
If the connections are encrypted, enter the encryption port and strength settings.

Note - User Directory connections can be authenticated by client certificates from a Certificate Authority (CA). To use certificates, the LDAP server must be configured with SSL strong authentication. See Authenticating with Certificates.
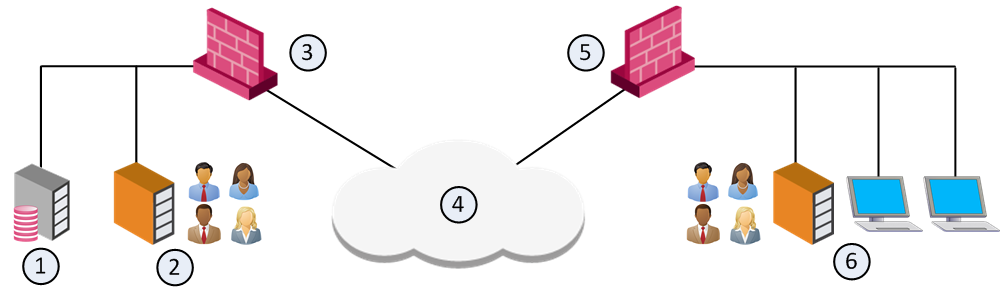
Account Units and High Availability
With User Directory replications for High Availability, one Account Unit represents all the replicated User Directory servers. For example, two User Directory server replications can be defined on one Account Unit, and two Security Gateways can use the same Account unit.
|
Item |
Description |
|---|---|
|
1 |
Security Management Server. Manages user data in User Directory. It has an Account Unit object, where the two servers are defined. |
|
2 |
User Directory server replication. |
|
3 |
Security Gateway. Queries user data and retrieves CRLs from nearest User Directory server replication (2). |
|
4 |
Internet |
|
5 |
Security Gateway. Queries user data and retrieves CRLs from nearest User Directory server replication (6). |
|
6 |
User Directory server replication. |
Setting High Availability Priority
With multiple replications, define the priority of each LDAP server in the Account Unit. Then you can define a server list on the Security Gateways.
Select one LDAP server for the Security Management Server to connect to. The Security Management Server can work with one LDAP server replication. All other replications must be synchronized for standby.
-
Open the LDAP Account Unit Properties window.
-
Open the Servers tab.
-
Add the LDAP servers of this Account Unit in the order of the priority that you want.
Authenticating with Certificates
The Security Management Server and Security Gateways can use certificates to secure communication with LDAP servers. If you do not configure certificates, the management server, Security Gateways, and LDAP servers communicate without authentication.
-
Close all SmartConsole windows connected to the Management Server.
-
On each Account Unit, to which you want to authenticate with a certificate, set the
ldap_use_cert_authattribute totrue:-
Connect with Database Tool (GuiDBEdit Tool) (see sk13009) to the Management Server.
-
In the left pane, browse to Table > Managed Objects > servers.
-
In the right pane, select the Account Unit object.
-
In the bottom pane, search for the
ldap_use_cert_authattribute, and set it to true. -
Save the changes and close Database Tool (GuiDBEdit Tool).
-
-
Connect with SmartConsole to the Management Server.
-
Add a CA object:
-
In the Object Explorer (F11), click New > More > Server > More > Trusted CA.
The Certificate Authority Properties window opens.
-
In Certificate Authority Type, select External Check Point CA.
-
Set the other options of the CA.
-
-
For all necessary network objects (such as Security Management Server, Security Gateway, Policy Server) that require certificate-based User Directory connections:
-
On the IPSec VPN page of the network object properties, click Add in the Repository of Certificates Available list.

Note - A management-only server does not have an IPSec VPN
 Check Point Software Blade on a Security Gateway that provides a Site to Site VPN and Remote Access VPN access. page. The User Directory on a management-only server cannot be configured to authenticate to an LDAP server using certificates.
Check Point Software Blade on a Security Gateway that provides a Site to Site VPN and Remote Access VPN access. page. The User Directory on a management-only server cannot be configured to authenticate to an LDAP server using certificates. -
In the Certificate Properties window, select the defined CA.
-
-
Test connectivity between the Security Management Server and the LDAP Server.