VPN Routing - Remote Access
The Need for VPN Routing
There are a number of scenarios in which a Security Gateway![]() Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. or remote access clients cannot connect directly to another Security Gateway (or clients). Sometimes, a given Security Gateway or client is incapable of supplying the required level of security. For example:
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. or remote access clients cannot connect directly to another Security Gateway (or clients). Sometimes, a given Security Gateway or client is incapable of supplying the required level of security. For example:
-
Two Security Gateways with dynamically assigned IP addresses (DAIP Security Gateways). Hosts behind either Security Gateway need to communicate; however, the changing nature of the IP addresses means the two DAIP Security Gateways cannot open VPN tunnels. At the moment of tunnel creation, the exact IP address of the other is unknown.
-
Remote access client users wish to have a private conversation using Voice-over-IP (VoIP) software or utilize other client-to-client communication software such as Microsoft NetMeeting. Remote access clients cannot open connections directly with each other, only with configured Security Gateways.
In all cases, a method is needed to enhance connectivity and security.
Check Point Solution for Greater Connectivity and Security
VPN routing provides a way of controlling how VPN traffic is directed. VPN routing can be implemented with Security Gateway modules and remote access clients. Configuration for VPN routing is performed either directly through SmartConsole![]() Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. (in simple cases) or by editing the VPN routing configuration files on the Security Gateways (in more complex scenarios).
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on. (in simple cases) or by editing the VPN routing configuration files on the Security Gateways (in more complex scenarios).

|
Item |
Description |
|---|---|
|
1 |
Host machines |
|
2 |
Security Gateway A |
|
3 |
Internet |
|
4 |
Security Gateway B |
|
5 |
Host machines |
|
6 |
|
|
7 |
Security Gateway C |
|
8 |
Host machines |
In the figure above, one of the host machines behind Security Gateway A needs to connect with a host machine behind Security Gateway B. For either technical or policy reasons, Security Gateway A cannot open a VPN tunnel with Security Gateway B. However, both Security Gateways A and B can open VPN tunnels with Security Gateway C, so the connection is routed through Security Gateway C.
As well as providing enhanced connectivity and security, VPN routing can ease network management by hiding a complex network of Security Gateways behind a single Hub.
Hub Mode (VPN Routing for Remote Clients)
VPN routing for remote access clients is enabled via Hub Mode. In Hub mode, all traffic is directed through a central Hub. The central Hub acts as a kind of router for the remote client. Once traffic from remote access clients is directed through a Hub, connectivity with other clients is possible as well as the ability to inspect the subsequent traffic for content.
When using Hub mode, enable Office mode. If the remote client is using an IP address supplied by an ISP, this address might not be fully routable. When Office mode is used, rules can be created that relate directly to Office mode connections.
Note - Office mode is not supported in SecuRemote.
Allowing Clients to Route all Traffic Through a Security Gateway
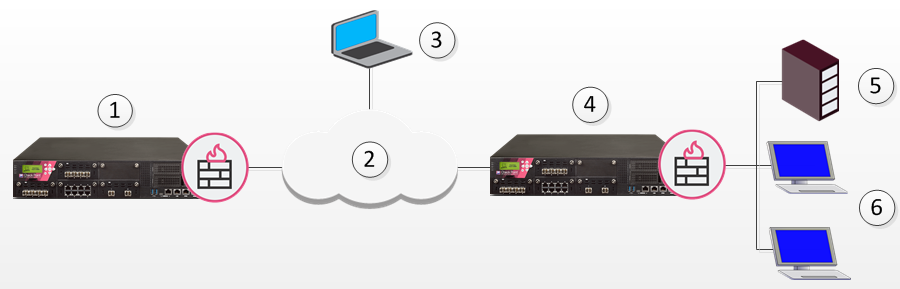
In the following figure, the remote client needs to connect with a server behind Security Gateway 2. Company policy states that all connections to this server must be inspected for content. For whatever reason, Security Gateway 2 cannot perform the required content inspection. When all the traffic is routed through Security Gateway 1, connections between the remote client and the server can be inspected.
|
Item |
Description |
|---|---|
|
1 |
Security Gateway 1 |
|
2 |
Internet |
|
3 |
Remote client |
|
4 |
Security Gateway 2 |
|
5 |
Server |
|
6 |
Hosts |
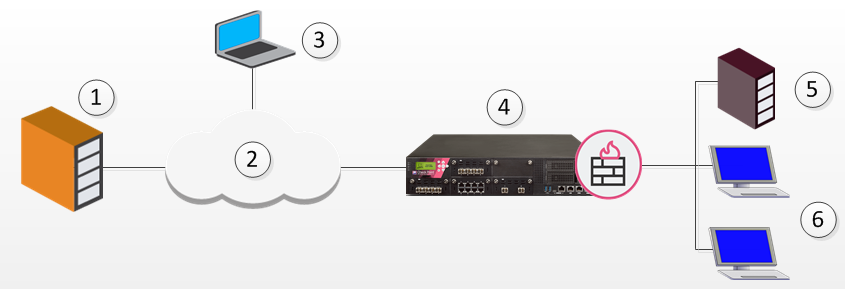
Suppose the same remote client needs to access an HTTP server on the Internet. The same company policy regarding security still applies.
|
Item |
Description |
|---|---|
|
1 |
HTTP Server |
|
2 |
Internet |
|
3 |
Remote client |
|
4 |
Security Gateway |
|
5 |
OSPEC Certified UFP server |
|
6 |
Hosts |
The remote client's traffic is directed to the Security Gateway where it is directed to the UFP (URL Filtering![]() Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF. Protocol) server to check the validity of the URL and packet content, since the Security Gateway does not possess URL-checking functionality. The packets are then forwarded to the HTTP server on the Internet.
Check Point Software Blade on a Security Gateway that allows granular control over which web sites can be accessed by a given group of users, computers or networks. Acronym: URLF. Protocol) server to check the validity of the URL and packet content, since the Security Gateway does not possess URL-checking functionality. The packets are then forwarded to the HTTP server on the Internet.
NATing the address of the remote client behind the Security Gateway prevents the HTTP server on the Internet from replying directly to the client. If the remote client's address is not NATed, the remote client will not accept the clear reply from the HTTP server.
Remote Client to Client Communication
Remote client to client connectivity is achieved in two ways:
-
By routing all the traffic through the Security Gateway
-
Including the Office Mode range of addresses in the VPN domain of the Security Gateway
Routing all Traffic through the Security Gateway
Two remote users use VoIP software to hold a secure conversation. The traffic between them is directed through a central Hub, as shown in the following figure.

|
Item |
Description |
|---|---|
|
1 |
Security Gateway |
|
2 |
Internet |
|
3 |
Remote Client VoIP |
|
4 |
Remote Client VoIP |
For this to work:
-
Allow VPN clients to route traffic through this Security Gateway must be enabled on the Security Gateway.
-
The remote client must be configured with a profile that enables all traffic to be routed through the Security Gateway.
-
Remote clients are working in connect mode.
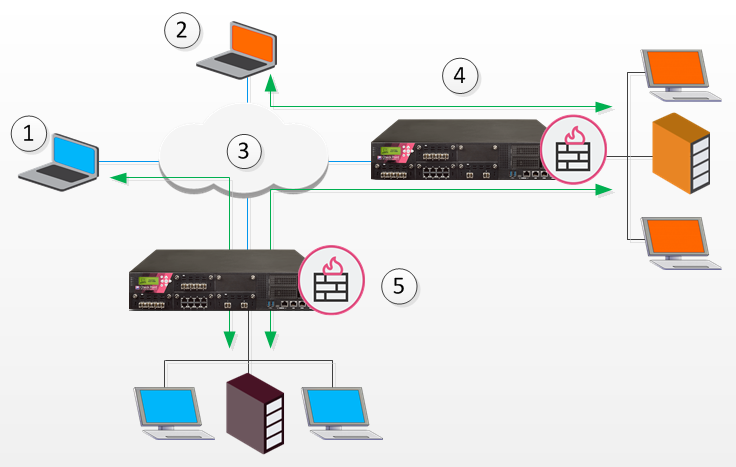
If the two remote clients are configured for Hub mode with different Security Gateways, the routing takes place in three stages - each remote client to its designated Security Gateway, then between the Security Gateways:
|
Item |
Description |
|---|---|
|
1 |
Remote Client 1 |
|
2 |
Remote Client 2 |
|
3 |
Internet |
|
4 |
Security Gateway A |
|
5 |
Security Gateway B |
In the figure above, remote client 1 is configured for Hub mode with Security Gateway B. Remote client 2 is configured for Hub mode with Security Gateway A. For the connection to be routed correctly:
-
Office mode must be enabled.
-
VPN configuration files on both Security Gateways must include the Office Mode address range used by the other. The VPN configuration file on Security Gateway A directs all traffic aimed at an Office Mode IP address of Security Gateway B towards Security Gateway B. A connection leaves Remote Client1 and is sent to Security Security Gateway B. From Security Gateway B the connection is passed to Security Security Gateway A. Security Security Gateway A once more redirects the traffic towards Remote Client 2. The reply from Remote Client2 follows the same path but in reverse.
-
Office mode addresses used by both Security Gateways must be non-overlapping.
Configuring VPN Routing for Remote Access VPN
Common VPN routing scenarios can be configured through a VPN star community, but not all VPN routing configuration is handled through SmartConsole. VPN routing between Security Gateways (star or mesh) can be also be configured by editing the configuration file $FWDIR/conf/vpn_route.conf
VPN routing cannot be configured between Security Gateways that do not belong to a VPN community.
Hub Mode for Remote Access Clients
To enable Hub Mode for Remote Access clients:
-
Click Gateways & Servers and double-click the Security Gateway.
The Security Gateway window opens and shows the General Properties page.
-
From the navigation tree, click VPN Clients > Remote Access.
-
In the Hub Mode configuration section, click Allow VPN clients to route all traffic through this Security Gateway.
-
Click OK.
-
From the Objects Bar, click VPN Communities.
-
Double-click the Remote Access community object.
-
From the Participating Gateways page, make sure that the Hub Security Gateway is in the window.
-
On the Participant User Groupspage, select the remote access users or user groups.
-
Click OK.
-
Create the access control rule
 Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. in the Access Control Policy.
Set of traffic parameters and other conditions in a Rule Base (Security Policy) that cause specified actions to be taken for a communication session. in the Access Control Policy.VPN routing traffic is handled in the Security Policy
 Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. Rule Base
Collection of rules that control network traffic and enforce organization guidelines for data protection and access to resources with packet inspection. Rule Base All rules configured in a given Security Policy. Synonym: Rulebase. as a single connection, matched to one rule only.
All rules configured in a given Security Policy. Synonym: Rulebase. as a single connection, matched to one rule only. -
Click OK and publish the changes.
-
Configure the profile on the remote client to route all communication through the designated Security Gateway.
Adding the Office Mode Range to the VPN Domain
SmartConsole includes a default object for Office Mode IP addresses, CP_default_Office_Mode_addresses_pool. You can use the default object, or create a new one for your network.
To create a new Office Mode IP address object:
-
In SmartConsole, click Objects >Object Explorer (Ctrl+E).
-
Click New > Network.
-
Enter the Name, IP address and Net mask.
-
Click OK and publish the changes.
To configure VPN routing for remote access clients with the VPN domain:
-
Create a network group, click New > Network Group.
-
Add these network groups:
-
VPN domain
-
Office Mode
-
-
Click OK and publish the changes.
-
Click Gateways & Servers and double-click the Security Gateway.
The Security Gateway window opens and shows the General Properties page.
-
From the navigation tree, click Network Management > VPN Domain.
-
Click Manually defined.
-
Select the new network group.
-
Click OK and publish the changes.
The remote clients must connect to the site and perform a site update before they can communicate with each other.
Client to Client via Multiple Hubs Using Hub Mode
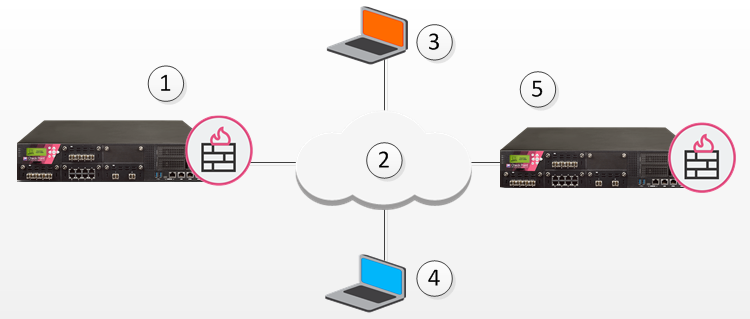
The figure below shows two remote clients each configured to work in Hub mode with a different Security Gateway:
|
Item |
Description |
|---|---|
|
1 |
Hub 1 |
|
2 |
Internet |
|
3 |
Remote Client 1 |
|
4 |
Remote Client 2 |
|
5 |
Hub 2 |
Remote Client 1 works in Hub mode with Hub 1. Remote Client 2 works in Hub mode with the Hub 2. In order for VPN routing to be performed correctly:
-
Remote clients must be working in Office mode
-
Office mode address range of each Security Gateway must be included in the vpn_route.conf file installed on the other Security Gateway.
Destination
Next hop router interface
Install On
Hub1_OfficeMode_range
Hub1
Hub2
Hub2_OfficeMode_range
Hub2
Hub1
When Remote Client 1 communicates with Remote Client 2:
-
The traffic first goes to the Hub 1, since Remote Client 1 is working in Hub mode with Hub 1.
-
Hub 1 identifies Remote Client 2's IP address as belonging to the Office mode range of Hub 2.
-
The vpn_route.conf file on Hub 1 identifies the next hop for this traffic as Hub 2.
-
The traffic reaches the Hub 2; Hub 2 redirects the communication to Remote Client 2.
Link Selection for Remote Clients
Link Selection is a method used to determine which interface to use for incoming and outgoing VPN traffic and the best possible path for the traffic. Using Link Selection, you choose which IP addresses are used for VPN traffic on each Security Gateway.
Load Sharing and Service Based Link Selection are not supported when the peer is a Remote Access Client. If the Probing Redundancy mode configuration is Load Sharing and the peer is a remote access client, High Availability will be enforced for the client's tunnel.
Link selection is configured on each Security Gateway in the Security Gateway Properties> IPSec VPN> Link Selectionwindow. The settings apply to both:
-
Security Gateway to Security Gateway connections
-
Remote access client to Security Gateway connections
You can configure Link Selection for remote users separately. These settings override the settings configured on the Link Selection page.
Configuring Link Selection for Remote Access Only
To configure separate Link Selection settings for remote access VPN:
-
Connect with Database Tool (GuiDBEdit Tool) (see sk13009) to Security Management Server
 Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server..
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server.. -
In the top left pane, to Network Objects > network_objects.
-
In the top right pane, select the Security Gateway / cluster
 Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. object.
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. object. -
In the bottom pane, change the value of
apply_resolving_mechanism_to_SRtofalse. -
In the bottom pane, edit the
ip_resolution_mechanismattribute to determine how remote access clients resolve the IP address of the local Security Gateway. Add one of the following:-
mainIpVpn -Always use the main IP address specified in the IP Address field on the General Properties page of the Security Gateway -
singleIpVpn -The VPN tunnel is created with the Security Gateway using an IP address set insingle_VPN_IP_RA -
singleNATIpVPN -The VPN tunnel is created using a NATed IP address set insingle_VPN_IP_RA -
topologyCalc -Calculate the IP address used for the VPN tunnel by network topology based on the location of the remote peer -
oneTimeProb -Use one time probing to determine which link will be used. -
ongoingProb -Use ongoing probing to determine which link will be used.
-
-
In the bottom pane, edit these parameters if you are using ongoing or one time probing:
-
interface_resolving_ha_primary_if- The primary IP address used for one-time / ongoing probing. -
use_interface_IP- Set to true if all IP addresses defined in topology tab should be probed. Set to false if the manual list of IP addresses should be probed. -
available_VPN_IP_list- A List of IP addresses that should be probed. (This list is used only if the value ofuse_interface_IPisfalse).
-
-
Save changes (File menu > Save All).
-
Close the Database Tool (GuiDBEdit Tool).
-
In SmartConsole, install the Access Policy on the Security Gateway / cluster object.
To use multiple external links with remote access clients:
-
Open SmartConsole.
-
Double-click the Security Gateway / cluster object.
The Security Gateway window opens and shows the General Properties page.
-
From the navigation tree, click VPN Clients > Office Mode.
-
In the Multiple Interfaces section, select Support connectivity enhancement forgateways with multiple external interfaces.
-
Click OK.
-
Install policy on the Security Gateway / cluster object.
Directional VPN in Remote Access Communities
Directional VPN for Remote Access Communities lets you reject connections to or from a specified network object.
|
Source |
Destination |
VPN |
Service |
Action |
|---|---|---|---|---|
|
Any |
Any |
Remote_Access_Community => MyIntranet |
Any |
drop |
|
Any |
Any |
Remote_Access_Community => Any Traffic |
Any |
accept |
Connections are not allowed between remote users and hosts within the "MyIntranet" VPN community. All other connections that start from the Remote Access Community, from inside or outside of the VPN communities, are allowed.
User Groups as the Destination in RA communities
User groups can be placed in the destination column of a rule. This makes:
-
Configuring client to client connections easier
-
Configuring "back connections" between a remote client and a Security Gateway possible.
|
Source |
Destination |
VPN |
Service |
Action |
|---|---|---|---|---|
|
Any |
Remote_Users@Any |
Any Traffic => Remote_Access_Community |
Any |
accept |
To include user groups in the destination column of a rule:
-
The rule must be directional
-
In the VPN column, the Remote Access community must be configured as the endpoint destination
Configuring Directional VPN with Remote Access Communities
To configure Directional VPN with Remote Access communities:
-
From , click Global Properties.
-
From the navigation tree, click VPN > Advanced.
-
Click Enable VPN Directional Match in VPN Column.
-
Click OK and publish the changes.
-
Go to Security Policies > Access Control Policy.
-
Right-click the VPN cell for the rule, and select Directional Match Condition.
The New Directional Match Condition window opens.
-
Configure the directional VPN:
-
From Traffic reaching from, select the source of the connection
-
From Traffic leaving to, select the connection's destination
-
-
Click OK.
-
Install policy.
