Office Mode
The Need for Remote Clients to be Part of the LAN
As remote access to internal networks of organizations becomes widespread, it is essential that remote users are able to access as many of the internal resources of the organization as possible. Typically, when remote access is implemented, the client connects using an IP address locally assigned by, for example, an ISP. The client may even receive a non-routable IP which is then hidden behind a NATing device. Because of this, several problems may arise:
-
Some networking protocols or resources may require the client's IP address to be an internal one. Router ACLs (access lists), for example, might be configured to allow only specific or internal IP addresses to access network resources. This is difficult to adjust without knowing the remote client's IP address in advance.
-
When assigned with a non-routable IP address a conflict may occur, either with similar non-routable addresses used on the corporate LAN, or with other clients which may receive the same IP address while positioned behind some other hiding NAT device.
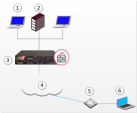
For example, if a client user receives an IP address of 10.0.0.1 which is entered into the headers of the IPSec packet. The packet is NATed. The packet's new source IP address is 192.168.17.5. The Security Gateway
 Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. decapsulates the NATed IP and decrypts the packet. The IP address is reverted to its original source IP address of 10.0.0.1. If there is an internal host with the same IP, the packet will probably be dropped (if Anti-Spoofing is turned on). If there is no duplicate IP, and the packet is forwarded to some internal server, the server will then attempt to reply to a non-existent address.
Dedicated Check Point server that runs Check Point software to inspect traffic and enforce Security Policies for connected network resources. decapsulates the NATed IP and decrypts the packet. The IP address is reverted to its original source IP address of 10.0.0.1. If there is an internal host with the same IP, the packet will probably be dropped (if Anti-Spoofing is turned on). If there is no duplicate IP, and the packet is forwarded to some internal server, the server will then attempt to reply to a non-existent address. -
Two remote users are assigned the same IP address by an ISP (for example, two users are accessing the organization from hotels which provide internal addresses and NAT them on the outbound). Both users try to access the internal network with the same IP address. The resources on the internal network of the organization may have difficulty distinguishing between the users.
Office Mode
Office Mode enables a Security Gateway to assign a remote client an IP address. The assignment takes place once the user connects and authenticates. The assignment lease is renewed as long as the user is connected. The address may be taken either from a general IP address pool, or from an IP address pool specified per user group. The address can be specified per user, or via a DHCP server, enabling the use of a name resolution service. With DNS name resolution, it is easier to access the client from within the corporate network.
It is possible to allow all your users to use Office Mode, or to enable the feature for a specific group of users. This can be used, for example, to allow privileged access to a certain group of users (e.g., administrators accessing the LAN from remote stations). It is also useful in early integration stages of Office Mode, allowing you time to "pilot" this feature on a specific group of users, while the rest of the users continue to work in the traditional way.
Office Mode is supported with the following:
-
Endpoint Security VPN
-
SSL Network Extender
-
Crypto
-
L2TP
How Office Mode Works
When you connect to the organization, an IKE negotiation is initiated automatically to the Security Gateway. When using Office Mode, a special IKE mode called config mode is inserted between phase 1 and phase 2 of IKE. During config mode, the client requests an IP from the Security Gateway. Several other parameters are also configurable this way, such as a DNS server IP address, and a WINS server IP address.
After the Security Gateway allocates the IP address, the client assigns the IP to a Virtual Adapter on the Operating system. The routing of packets to the corporate LAN is modified to go through this adapter. Packets routed in this way bear the IP address assigned by the Security Gateway as their source IP address. Before exiting through the real adapter, the packets will be IPsec encapsulated using the external IP address (assigned to the real adapter) as the source address. In this way, non-routable IP addresses can be used with Office Mode; the Office Mode non-routable address is concealed within the IPsec packet.
For Office Mode to work, the IP address assigned by the Security Gateway needs to be routable to that Security Gateway from within the corporate LAN. This lets packets on the LAN being sent to the client to be routed back through the Security Gateway (see Office Mode and Static Routes in a Non-flat Network).
|
|
Note - A remote user with SecuRemote client only is not supported in Office Mode. |
A Closer Look
The following steps illustrate the process taking place when a remote user connected through Office Mode wishes to exchange some information with resources inside the organization:
-
The user is trying to connect to some resource on the LAN, thus a packet destined for the internal network is to be sent. This packet is routed through the virtual interface that Office Mode had set up, and bears the source IP address allocated for the remote user.
-
The packet is encrypted and builds a new encapsulating IP header for it. The source IP of the encapsulating packet is the remote client's original IP address, and its destination is the IP address of the Security Gateway. The encapsulated packet is then sent to the organization through the Internet.
-
The Security Gateway of the organization receives the packet, decapsulates and decrypts it, revealing the original packet, which bears the source IP allocated for the remote user. The Security Gateway then forwards the decapsulated packet to its destination.
-
The internal resource gets a packet seemingly coming from an internal address. It processes the packet and sends response packets back to the remote user. These packets are routed back to the (internal) IP address assigned to the remote user.
-
The Security Gateway gets the packet, encrypts and encapsulates it with the remote users' original (routable) IP address and returns the packet back to the remote user:
|
Item |
Description |
|---|---|
|
1 |
Host IP Address 10.0.01 |
|
2 |
Server |
|
3 |
Gateway |
|
4 |
Internet |
|
5 |
ISP Router |
|
6 |
User's machine |
-
The remote host uses the Office mode address in the encapsulated packet and 10.0.0.1 in the encapsulating header.
-
The packet is NATed to the new source address: 192.168.17.5
-
The Security Gateway decapsulates the NATed IP address and decrypts the packet. The source IP address is the Office Mode address.
-
The packet is forwarded to the internal server, which replies correctly.
Assigning IP Addresses
The internal IP addresses assigned by the Security Gateway to the remote user can be allocated using one of the following methods:
-
IP Pool
-
DHCP Server
IP Pool
The System Administrator designates a range of IP addresses to be utilized for remote client machines. Each client requesting to connect in Office Mode is provided with a unique IP address from the pool.
IP Assignment Based on Source IP Address
IP addresses from the IP pool may be reserved and assigned to remote users based on their source IP address. When a remote host connects to the Security Gateway, its IP address is compared to a predefined range of source IP addresses. If the IP address is found to be in that range, then it is assigned an Office Mode IP address from a range dedicated for that purpose.
The IP addresses from this reserved pool can be configured to offer a separate set of access permissions given to these remote users.
DHCP Server
A Dynamic Host Configuration Protocol (DHCP) server can be used to allocate IP addresses for Office Mode clients. When a remote user connects to the Security Gateway using Office Mode, the Security Gateway requests the DHCP server to assign the user an IP address from a range of IP addresses designated for Office Mode users.
Security Gateway DHCP requests can contain various client attributes that allow DHCP clients to differentiate themselves. The attributes are pre-configured on the client side operating system, and can be used by different DHCP servers in the process of distributing IP addresses. Security Gateways DHCP request can contain the following attributes:
-
Host Name
-
Fully Qualified Domain Name (FQDN)
-
Vendor Class
-
User Class
RADIUS Server
A RADIUS server can be used for authenticating remote users. When a remote user connects to a Security Gateway, the username and password are passed on to the RADIUS server, which checks that the information is correct, and authenticates the user. The RADIUS server can also be configured to allocate IP addresses.
|
|
Note - Authentication and IP assignment must be performed by the same RADIUS server. |
Office Mode and Static Routes in a Non-flat Network
A flat network is one in which all stations can reach each other without going through a bridge or a router. One segment of a network is a "flat network". A static route is a route that is manually assigned by the system administrator (to a router) and needs to be manually updated to reflect changes in the network.
If the LAN is non-flat (stations reach each other via routers and bridges) then the OM address of the remote client must be statically assigned to the routers so that packets on the LAN, destined for the remote client, are correctly routed to the Security Gateway.
IP Address Lease duration
When a remote user's machine is assigned an Office mode IP address, that machine can use it for a certain amount of time. This time period is called the "IP address lease duration." The remote client automatically asks for a lease renewal after half of the IP lease duration period has elapsed. If the IP lease duration time is set to 60 minutes, a renewal request is sent after 30 minutes. If a renewal is given, the client will request a renewal again after 30 minutes. If the renewal fails, the client attempts again after half of the remaining time, for example, 15 minutes, then 7.5 minutes, and so on. If no renewal is given and the 60 minutes of the lease duration times out, the tunnel link terminates. To renew the connection the remote user must reconnect to the Security Gateway. Upon reconnection, an IKE renegotiation is initiated and a new tunnel created.
When the IP address is allocated from a predefined IP pool on the Security Gateway, the Security Gateway determines the IP lease duration period. The default is 15 minutes.
When using a DHCP server to assign IP addresses to users, the DHCP server's configuration determines the IP lease duration. When a user disconnects and reconnects to the Security Gateway within a short period of time, it is likely that the user will get the same IP address as before.
Using Name Resolution - WINS and DNS
To facilitate access of a remote user to resources on the internal network, the administrator can specify WINS and DNS servers for the remote user. This information is sent to the remote user during IKE config mode along with the IP address allocation information, and is used by the remote user's operating system for name-to-IP resolution when the user is trying to access the organization's internal resources.
Anti-Spoofing
With Anti-Spoofing, a network administrator configures which IP addresses are expected on each interface of the Security Gateway. Anti-Spoofing ensures IP addresses are only received or transmitted in the context of their respective Security Gateway interfaces. Office Mode poses a problem to the Anti-Spoofing feature, since a client machine can connect and authenticate through several interfaces, e.g. the external interface to the Internet, or the wireless LAN interface; thus an Office Mode IP address may be encountered on more than one interface. Office Mode enhances Anti-Spoofing by making sure an encountered Office Mode IP address is indeed assigned to the user, authenticated on the source IP address on the IPsec encapsulating packet, i.e. the external IP.
Using Office Mode with Multiple External Interfaces
Typically, routing is performed before encryption in VPN. In some complex scenarios of Office Mode, where the Security Gateway may have several external interfaces, this might cause a problem. In these scenarios, packets destined at a remote user's virtual IP address will be marked as packets that are supposed to be routed through one external interface of the Security Gateway. Only after the initial routing decision is made do the packets undergo IPsec encapsulation. After the encapsulation, the destination IP address of these packets is changed to the original IP address of the client. The routing path that should have been selected for the encapsulated packet might be through a different external interface than that of the original packet (since the destination IP address changed), in which case a routing error occurs. Office Mode has the ability to make sure that all Office Mode packets undergo routing after they are encapsulated.
Office Mode Per Site
After a remote user connects and receives an Office Mode IP address from a Security Gateway, every connection to that Security Gateways encryption domain will go out with the Office Mode IP as the internal source IP. The Office Mode IP is what hosts in the encryption domain will recognize as the remote user's IP address.
The Office Mode IP address assigned by a specific Security Gateway can be used in its own encryption domain and in neighboring encryption domains as well. The neighboring encryption domains should reside behind Security Gateways that are members of the same VPN community as the assigning Security Gateway. Since the remote hosts' connections are dependent on the Office Mode IP address it received, if the Security Gateway that issued the IP becomes unavailable, all he connections to the site will terminate.
In order for all Security Gateways on the site to recognize the remote users Office Mode IP addresses, the Office Mode IP range must be known by all of the Security Gateways and the IP ranges must be routable in all the networks. However, when the Office Mode per Site feature is in use, the IP-per-user feature cannot be implemented.
|
|
Note - When Office Mode per Site is activated, Office Mode Anti-Spoofing is not enforced. |
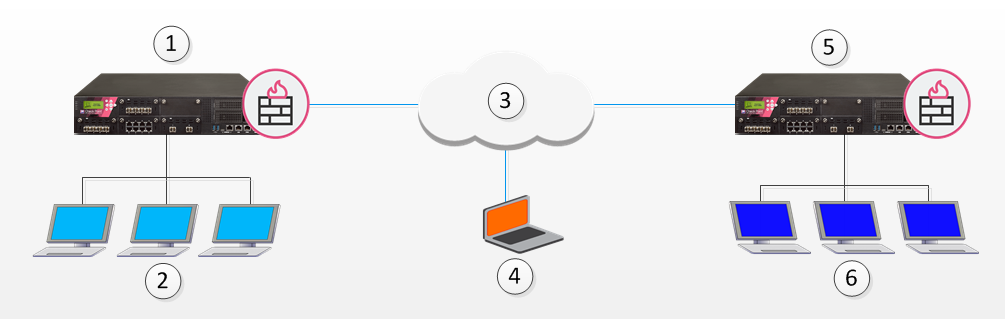
In this scenario:
|
Item |
Description |
|---|---|
|
1 |
Security Gateway 1 |
|
2 |
VPN Domain A |
|
3 |
Internet |
|
4 |
Remote Host |
|
5 |
Security Gateway 2 |
|
6 |
VPN Domain B |
-
The remote user makes a connection to Security Gateway 1.
-
Security Gateway 1 assigns an Office Mode IP address to the remote user.
-
While still connected to Security Gateway 1, the remote user can make a connection to hosts behind Security Gateway 2 using the Office Mode IP address issued by Security Gateway 1.
Enabling IP Address per User
In some configurations, a router or other device restricts access to portions of the network to specified IP addresses. A remote user connecting in Office Mode can get a specified IP address, or an IP address from a specified range, which will allow the connection to pass through the router.
|
|
Note - If this feature is implemented, you must enable Anti-Spoofing for Office Mode (see Anti-Spoofing). |
You can use a DHCP server or IP Pool to allocate IP addresses.
DHCP Server
To configure Office Mode addresses that are allocated by a DHCP server:
-
In SmartConsole
 Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., click Gateways & Servers and double-click the Security Gateway.
Check Point GUI application used to manage a Check Point environment - configure Security Policies, configure devices, monitor products and events, install updates, and so on., click Gateways & Servers and double-click the Security Gateway.The Security Gateway Properties window opens and shows the General Properties page.
-
From the navigation tree, click VPN Clients > Office Mode.
-
Enable Office Mode for a group or all users.
-
In the Office Mode Method section select these options:
-
Click Using one of the following methods
-
Click Automatic (using DHCP)
-
-
Click MAC address for DHCP allocation, select calculated per user name
-
Click OK and publish the changes.
-
Install the Policy on the Security Gateway.
-
Log in to the Security Gateway CLI, run this command to obtain the MAC address assigned to the user.
vpn macutil <username> -
On the DHCP Server make a new reservation, specifying the IP address and MAC address, assigning the IP address for the exclusive use of the given user.
The ipassignment.conf File
The $FWDIR/conf/ipassignment.conf file on the Security Gateway, is used to implement the IP-per-user feature. It lets the administrator to assign specific addresses to specific users or specific ranges to specific groups when they connect using Office Mode or L2TP clients.
|
|
Note:
. |
Sample ipassignment.conf File
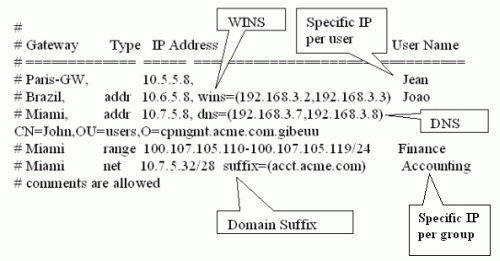
# This file is used to implement the IP-per-user feature. It allows the # administrator to assign specific addresses to specific users or specific# ranges to specific groups when they connect using Office Mode or L2TP. # # The format of this file is simple: Each line specifies the target # gateway, the IP address (or addresses) we wish to assign and the user # (or group) name as in the following examples: # # Gateway Type IP Address User Name # ============= ===== ======================================== ========================================= # Paris-GW, 10.5.5.8, Jean # Brasilia, addr 10.6.5.8, wins=(192.168.3.2,192.168.3.3) Joao # comments are allowed # Miami, addr 10.7.5.8, dns=(192.168.3.7,192.168.3.8) CN=John,OU=users,O=cpmgmt.acme.com.gibeuu # 10.1.1.2 range 100.107.105.110-100.107.105.119/24 Finance # * net 10.7.5.32/28 suffix=(acct.acme.com) Accounting # # Note that real records do not begin with a pound-sign (#), and the commas # are optional. Invalid lines are treated as comments. Also, the # user name may be followed by a pound-sign and a comment. # # The first item is the gateway name or address. On lines that assign # multiple IP addresses to a group of users or a network (range or net # in the second item) this should be the physical address of the gateway, # or an asterisk (*) to signify all gateways. # On lines that assign one IP for one user this could be the gateway # name as well. A gateway will only honor lines that refer to it. # # The second item is a descriptor. It can be 'addr', 'range' or 'net'. # 'addr' specifies one IP for one user. This prefix is optional. # 'range' and 'net' specify a range of addresses. These prefixes are # required. # # The third item is the IP address or addresses. In the case of a single # address, it is specified in standard dotted decimal format. # ranges can be specified either by the first and last IP address, or using # a net specification. In either case you need to also specify the subnet # mask length ('/24' means 255.255.255.0). With a range, this is the subnet# mask. With a net it is both the subnet mask and it also determines the # addresses in the range. # # After the third item come any of three keyword parameters. These are # specifications for WINS (or NBNS) servers, for DNS servers and a DNS # suffix. The parameters themselves are on the format 'keyword=(params)' # where the params can be one address (such as "192.168.3.2"), several # IP addresses (such as "192.168.3.2,192.168.3.3") or a string (only # for the DNS suffix. The relevant keywords are "dns", "wins" and # "suffix" and they are not case-sensitive. # Inside the keyword parameters there must be no spaces or any other # extra characters. These will cause the entire line to be ignored. # # The last item is the user name. This can be a common name if the # user authenticates with some username/password method (like hybrid # or MD5-Challenge) or a DN if the user authenticates with a # certificate. # |
Office Mode Considerations
IP Pool versus DHCP
The question of whether IP addresses should be assigned by the Firewall (using IP pools) or by a DHCP server is a network administration and financial issue. Some network administrators may prefer to manage all of their dynamic IP addresses from the same location. For them, a central DHCP server might be preferable. Moreover, DHCP allows a cluster![]() Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. to assign all the addresses from a single pool, rather than have a different pool per cluster member
Two or more Security Gateways that work together in a redundant configuration - High Availability, or Load Sharing. to assign all the addresses from a single pool, rather than have a different pool per cluster member![]() Security Gateway that is part of a cluster. as you have to with Firewall IP pools. On the other hand, purchasing a DHCP server can be viewed by some as an unnecessary financial burden, in which case the IP pool option might be preferred.
Security Gateway that is part of a cluster. as you have to with Firewall IP pools. On the other hand, purchasing a DHCP server can be viewed by some as an unnecessary financial burden, in which case the IP pool option might be preferred.
Routing Table Modifications
IP addresses, assigned by Office Mode need to be routed by the internal LAN routers to the Security Gateway (or Security Gateway cluster) that assigned the address. This is to make sure packets, destined to remote access Office Mode users, reach the Security Gateway in order to be encapsulated and returned to the client machine. This may require changes to the organization's routing tables.
Using the Multiple External Interfaces Feature
Enabling this feature instructs Office Mode to perform routing decisions after the packets are encapsulated using IPsec, and prevents possible routing problems (see Using Office Mode with Multiple External Interfaces). This feature adds new checks and changes to the routing of packets through the Security Gateway, and has an impact on performance. As a result, we recommend that you use this feature only when these conditions are met:
-
The Security Gateway has multiple external interfaces
-
Office Mode packets are routed to the wrong external interface
Configuring Office Mode
Before configuring Office Mode the assumption is that standard VPN Remote Access has already been configured.
Before starting the Office Mode configuration, you must select an internal address space designated for remote users using Office Mode. This can be any IP address space, as long as the addresses in this space do not conflict with addresses used within the enterprise domain. It is possible to choose address spaces which are not routable on the Internet, such as 10.x.x.x.
The basic configuration of Office Mode is using IP pools. You can also configure Office Mode using DHCP for address allocation (see DHCP Configuration).
IP Pool Configuration
Make sure that all the internal routers are configured to route all the traffic destined to the internal address space you had reserved to Office Mode users through the Security Gateway.
To deploy the basic Office Mode using IP pools:
-
From the Objects Bar click New > Network.
The New Network window opens.
-
In the General tab, set the IP address pool range:
-
Enter a Name for the network.
-
In Network Addressenter the first IP address.
-
In Net Mask enter the subnet mask according to the required amount of IP addresses (entering 255.255.255.0, for example, will designate all 254 IP addresses from 10.130.56.1 to 10.130.56.254 for Office Mode addresses.)
-
Click OK and publish the changes.
-
-
Click Gateways & Servers and double-click the Security Gateway.
The Security Gateway Properties window opens and shows the General Properties page.
-
From the navigation tree, click VPN Clients > Office Mode.
-
Configure these settings:
-
In the Office Mode Method section, from Allocate IP from network select the IP Pool network object
-
Optional Parameters > IP lease duration - Enter the number of minutes that the IP address is used by the remote host
-
To allow routing to be done after the encapsulation of Office Mode packets, click Support connectivity enhancement for gateways with multiple external interfaces
-
To check that Office Mode packets are not spoofed, click PerformAnti-Spoofing on Office Mode addresses
-
-
Click OK and publish the changes.
-
If you completed configuring the settings for Office Mode, install the policy.
To specify which WINS and DNS servers Office Mode users can use:
Note - WINS and DNS servers should be set on the Security Management Server![]() Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. only when IP pool is the selected method.
Dedicated Check Point server that runs Check Point software to manage the objects and policies in a Check Point environment within a single management Domain. Synonym: Single-Domain Security Management Server. only when IP pool is the selected method.
-
Create a DNS server object.
-
From the Objects Bar click New > Host.
-
In the General page, enter the Object Name and IP address settings.
-
In the Servers page, click DNS Server.
-
Click OK.
-
-
Create a WINS server object.
-
From the Objects Bar click New > Host.
-
In the General page, enter the Object Name and IP address settings.
-
Click OK.
-
-
Publish the changes.
-
Click Gateways & Servers and double-click the Security Gateway.
The Security Gateway Properties window opens and shows the General Properties page.
-
From the navigation tree, click VPN Clients > Office Mode.
-
Click Optional Parameters.
-
For the DNS and WINS Servers, click Primary and select the server.
-
Click OK.
-
Install the Policy.
Configuring IP Assignment Based on Source IP Address
Configure the settings of the IP Assignment Based on Source IP Addressfeature in the $FWDIR/conf/user.def file. This file is located on the Security Management Server![]() Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server., which manages the gateways used for remote access.
Check Point Single-Domain Security Management Server or a Multi-Domain Security Management Server., which manages the gateways used for remote access.
You must define a range of source IP addresses and a range of Office Mode addresses. The $FWDIR/conf/user.deffile can contain multiple definitions for multiple gateways.
The first range defined in each line is the source IP address range. The second range in the line is the Office Mode IP address range.
For example:
all@module1 om_per_src_range={<10.10.5.0, 10.10.5.129; 1.1.1.5, 1.1.1.87>,<10.10.9.0, 10.10.9.255; 1.1.1.88, 1.1.1.95>};
all@module2 om_per_src_range={<70.70.70.4, 70.70.70.90; 8.8.8.6,8.8.8.86>};
In this scenario:
-
(10.10.5.0, 10.10.5.129), (10.10.9.0, 10.10.9.255), and (70.70.70.4, 70.70.70.90) are the VPN remote clients source IP address ranges
-
(1.1.1.5, 1.1.1.87), (1.1.1.88, 1.1.1.95), and (8.8.8.6, 8.8.8.68) are the Office Mode IP addresses that will be assigned to the remote users whose source IP falls in the range defined on the same line.
For example: A user with a source IP address between 10.10.10.5.0 and 10.10.5.129, will receive an Office Mode address between 1.1.1.5 and 1.1.1.87.
The IP Assignment Based on the Source IP Address is enabled with a flag in the $FWDIR/conf/objects_5_0.c file on the Security Management Server.
Add an attribute into the object of the Security Gateway:
-
Connect with the Database Tool (GuiDBEdit Tool) to the Security Management Server (Domain Management Server).
-
In the top left pane, go to Global Properties > Properties.
-
In the top right pane, select firewall_properties.
-
In the bottom pane, edit the om_use_ip_src_range parameter and select one of these values:
-
exclusively - If the remote host IP is not found in the source range, the remote user does not get an Office Mode IP address.
-
true - If the remote host IP is not found in the source IP range, the user will get an Office Mode IP address using another method.
-
false (default) - The parameter is not used.
-
Office Mode through the ipassignment.conf File
You can over-ride the Office Mode settings created on Security Management server. Edit the plain text file called ipassignment.conf in $FWDIR/conf on the Check Point Security Gateway. The Security Gateway uses these Office Mode settings and not those defined for the object in Security Management server.
ipassignment.conf can specify:
-
An IP per user/group, so that a particular user or user group always receives the same Office Mode address. This allows the administrator to assign specific addresses to users, or particular IP ranges/networks to groups when they connect using Office Mode.
-
A different WINS server for a particular user or group.
-
A different DNS server.
-
Different DNS domain suffixes for each entry in the file.
Subnet masks and Office Mode Addresses
You cannot use the ipassignment.conf file to assign a subnet mask to a single user. If using IP pools, the mask is taken from the network object, or defaults to 255.255.255.0 if using DHCP.
Checking the Syntax
The syntax of the ipassignment file can be checked using the command ipafile_check.
From a shell prompt run: vpnipafile_check ipassignment.conf
The two parameters are:
-
warn. Display errors
-
detail. Show all details
For example:
[user@Checkpoint conf]# vpn ipafile_check ipassignment.conf warn Reading file records... Invalid IP address specification in line 0057 Invalid IP address specification in line 0058 Invalid subnet in line 0060
[user @Checkpoint conf]# vpn ipafile_check ipassignment.conf detail Reading file records... Line 0051 is a comment (starts with #) Line 0052 is a comment (starts with #) Line 0053 is a comment (starts with #) Line 0054 is a comment (starts with #) Line 0055 is a comment (starts with #) Line 0056 ignored because it is empty Invalid IP address specification in line 0057 Invalid IP address specification in line 0058 line 0059 is OK. User="paul" Invalid subnet in line 0060 line 0061 is OK. Group="dns=1.1.1.1 Line 0062 ignored because it is empty Line 0063 ignored because it is empty Could not read line 64 in conf file - maybe EOF [user@Checkpoint conf]#
|
DHCP Configuration
To configure Office Mode with a DHCP server:
-
On your DHCP server's configuration, make sure that you have designated an IP address space for Office Mode users (e.g., 10.130.56.0).
-
From the Objects Bar click New > Host.
-
Configure the settings for the name, IP address, and subnet mask.
-
Click OK and publish the changes.
-
Double-click the Remote Access Security Gateway object.
The Security Gateway Properties window opens and shows the General Properties page.
-
From the navigation tree, click VPN Clients > Office Mode.
-
Configure these settings:
-
Click Automatic (use DHCP)
-
From Use specificDHCP server, select the DHCP server
-
In Virtual IP address for DHCP server replies, enter an IP address from the sub network of the IP addresses which are designated for Office Mode usage.
Office Mode supports DHCP Relay method for IP assignment, so you can direct the DHCP server as to where to send its replies. The routing on the DHCP server and that of internal routers must be adjusted so that packets from the DHCP server to this address are routed through the Security Gateway.
-
Optional: In the Additional IP addresses forAnti-Spoofing, select the network object you have created with the IP address range you have set aside for Office Mode on the DHCP server.
-
-
Click OK and publish the changes.
To create a new network object for Office Mode on the DHCP server:
-
From the Objects Bar click New > Network.
The New Network window opens.
-
In Network Addressenter the first address that is used (e.g. 10.130.56.0).
-
In Net Mask enter the subnet mask according to the amount of addresses that is used.
For example, the IP address 255.255.255.0 designates that all 254 IP addresses from 10.130.56.1 until 10.130.56.254 are set aside for remote host Office Mode addresses on the DHCP server.
-
Click OK and publish the changes.
-
Install the Access Control policy.
-
Make sure that all the internal routers are configured to route all the traffic destined to the internal address space you had reserved to Office Mode users through the Security Gateway.
For example, in the example above it is required to add routes to the class C sub network of 10.130.56.0 through the Security Gateway's IP address.
-
Make sure that the remote access clients are also configured to use Office Mode.
Office Mode - Using a RADIUS Server
To configure the RADIUS server to allocate IP addresses:
-
From the Objects Bar, click Servers > RADIUS.
-
Right-click the RADIUS server and select Edit.
The RADIUS Server Properties window opens.
-
Click the Accounting tab.
-
Select Enable IP Pool Management.
-
Select the service the RADIUS server uses to communicate with remote users.
-
Click OK and publish the changes.
To configure the RADIUS server to perform authentication for remote users:
-
In SmartConsole, click Gateways & Servers and double-click the Security Gateway.
The Security Gateway Properties window opens and shows the General Properties page.
-
From the navigation tree, click VPN Clients > Office Mode.
-
In the Office Mode Methodsection, click From the RADIUS server used to authenticate the user.
-
Click OK and publish the changes.
Use First Office Mode IP
To configure all gateways to work in Office Mode:
-
From , click Global Properties.
-
From the navigation tree, click Remote Access > VPN - Advanced.
-
In the Office Mode section, click Use first allocated Office Mode IP address for all connections to the Security Gateways of the site.
-
Click OK and publish the changes.